php editor Youzi today introduces to you the "read-only mode" in Word documents. This is a setting that protects the document content from being modified or deleted. There are two modes to choose from, one is fully read-only mode, the user cannot modify the document; the other is partially read-only mode, the user can view but cannot edit the document. These two modes can effectively protect the integrity of documents under different circumstances and provide a safer way to manage documents.
There are two modes of "read-only mode" for Word documents. Let's take a look at how to set these two modes.
Mode 1: "Read-only mode" without password
Passwordless "read-only mode", as the name suggests, means that this mode can be canceled directly without passing a password.
The setting method is as follows:
After opening the Word document, click the [File] option in the menu, then click [Information] → [Protect Document] → [Always open as read-only] in the new page, and then save the document, "Read-only" "Method" is set.

When you open the Word document again, a dialog box will pop up, prompting "Do you want to open it in read-only mode?"
Select "Yes", then after opening the document, you can edit and modify it, but the original document cannot be saved unless saved as a new document;
Select "No", then there is no "read-only mode".

If you want to cancel the mode of opening in "read-only mode", that is, you don't want the above prompt to appear every time you open a Word document, you can use two methods to solve it.
One is to directly save the Word document through "Save As", modify the file name, and save it as a new document. There is no "read-only mode".
The other is to cancel directly in the document. First, when opening the document, select "No" in the prompt dialog box to enter the document;

Then follow the operation path when setting up above, click [File] → [Information] → [Protect Document] → [Always open in read-only mode] to cancel the "read-only mode".

Mode 2: "Read-only mode" with password
Word documents can also be set in "read-only mode" with a password. The difference from "Mode 1" is that if you want to edit the document, you need to enter a password, otherwise it can only be opened in "read-only mode".
The setting method is as follows:
After opening the Word document, click the [File] option in the menu, then click [Save As] in the new page, and determine the saving directory after saving on the right;

After the [Save As] dialog box pops up, click [General Options] in the [Tools] list below;

After the [General Options] dialog box pops up, enter the password you want to set in the [Password when modifying files] column, click [OK] and enter it again. The "read-only mode" of the Word document will be set. .

When you open the document again, a dialog box will pop up prompting "You need to enter a password, otherwise it will be opened in read-only mode", which means that you can only edit and save the original document after entering the password. If you click "Read-only", you can also open the file. , but the original document cannot be saved directly after editing.

If you want to cancel the "read-only mode" of mode 2, there are two methods.
One is the same method as Mode 1. Save the Word document as a new document through "Save As", and modify the file name. The new document will not have "read-only mode" .
The other is to follow the set operation path, click [File] → [Save As] → “Select Save Directory” → [Tools] → [General Options], then you can see [Password when modifying the file] 】column contains the originally set password. Delete this row of passwords and save the document to directly remove the "read-only mode".

Of course, we can also use tools to quickly remove the above two "read-only modes" of Word documents. Take the Pepsi Niu Word Password Recovery Tool as an example. There is an "unrestriction" module in the tool. In addition to being able to unblock Word " "Read-only mode", you can also remove the "restricted password", and there is also a "retrieve password" module, which can help retrieve the "open password" of Word. It is a tool worth collecting.
Tool link: Pepsi Niu Word Password Recovery Tool

The above is the detailed content of Two modes of 'read-only mode” for Word documents. For more information, please follow other related articles on the PHP Chinese website!
 Microsoft 365 Will Turn Off ActiveX, Because Hackers Keep Using ItApr 12, 2025 am 06:01 AM
Microsoft 365 Will Turn Off ActiveX, Because Hackers Keep Using ItApr 12, 2025 am 06:01 AMMicrosoft 365 is finally phasing out ActiveX, a long-standing security vulnerability in its Office suite. This follows a similar move in Office 2024. Beginning this month, Windows versions of Word, Excel, PowerPoint, and Visio in Microsoft 365 will
 How to Use Excel's AGGREGATE Function to Refine CalculationsApr 12, 2025 am 12:54 AM
How to Use Excel's AGGREGATE Function to Refine CalculationsApr 12, 2025 am 12:54 AMQuick Links The AGGREGATE Syntax
 How to Format a Spilled Array in ExcelApr 10, 2025 pm 12:01 PM
How to Format a Spilled Array in ExcelApr 10, 2025 pm 12:01 PMUse formula conditional formatting to handle overflow arrays in Excel Direct formatting of overflow arrays in Excel can cause problems, especially when the data shape or size changes. Formula-based conditional formatting rules allow automatic formatting to be adjusted when data parameters change. Adding a dollar sign ($) before a column reference applies a rule to all rows in the data. In Excel, you can apply direct formatting to the values or background of a cell to make the spreadsheet easier to read. However, when an Excel formula returns a set of values (called overflow arrays), applying direct formatting will cause problems if the size or shape of the data changes. Suppose you have this spreadsheet with overflow results from the PIVOTBY formula,
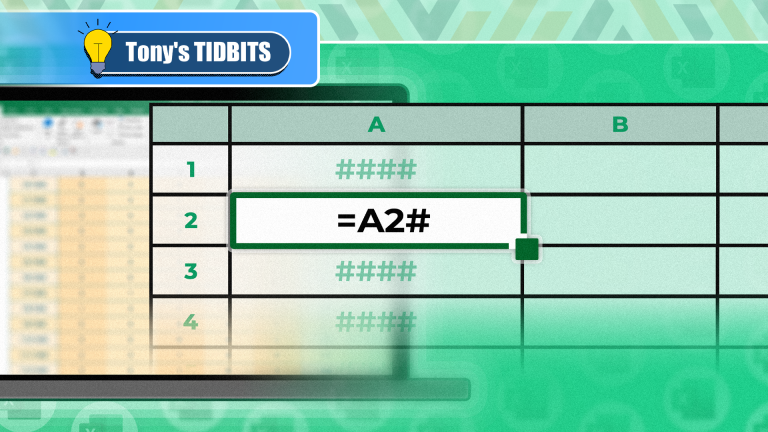 You Need to Know What the Hash Sign Does in Excel FormulasApr 08, 2025 am 12:55 AM
You Need to Know What the Hash Sign Does in Excel FormulasApr 08, 2025 am 12:55 AMExcel Overflow Range Operator (#) enables formulas to be automatically adjusted to accommodate changes in overflow range size. This feature is only available for Microsoft 365 Excel for Windows or Mac. Common functions such as UNIQUE, COUNTIF, and SORTBY can be used in conjunction with overflow range operators to generate dynamic sortable lists. The pound sign (#) in the Excel formula is also called the overflow range operator, which instructs the program to consider all results in the overflow range. Therefore, even if the overflow range increases or decreases, the formula containing # will automatically reflect this change. How to list and sort unique values in Microsoft Excel
 How to Create a Timeline Filter in ExcelApr 03, 2025 am 03:51 AM
How to Create a Timeline Filter in ExcelApr 03, 2025 am 03:51 AMIn Excel, using the timeline filter can display data by time period more efficiently, which is more convenient than using the filter button. The Timeline is a dynamic filtering option that allows you to quickly display data for a single date, month, quarter, or year. Step 1: Convert data to pivot table First, convert the original Excel data into a pivot table. Select any cell in the data table (formatted or not) and click PivotTable on the Insert tab of the ribbon. Related: How to Create Pivot Tables in Microsoft Excel Don't be intimidated by the pivot table! We will teach you basic skills that you can master in minutes. Related Articles In the dialog box, make sure the entire data range is selected (
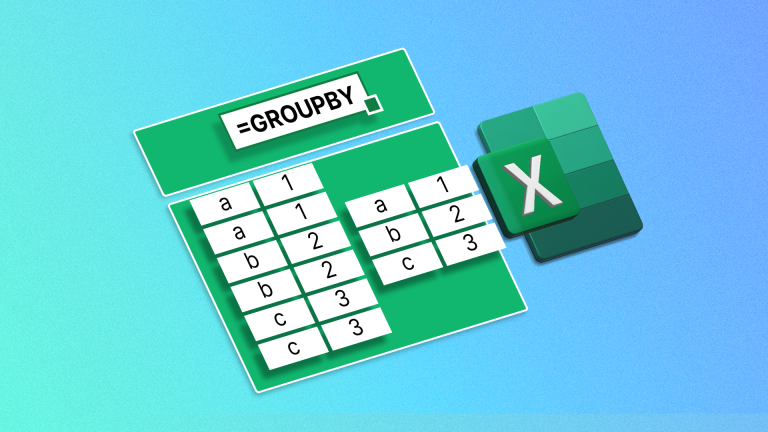 How to Use the GROUPBY Function in ExcelApr 02, 2025 am 03:51 AM
How to Use the GROUPBY Function in ExcelApr 02, 2025 am 03:51 AMExcel's GROUPBY function: Powerful data grouping and aggregation tools Excel's GROUPBY function allows you to group and aggregate data based on specific fields in a data table. It also provides parameters that allow you to sort and filter the data so that you can customize the output to your specific needs. GROUPBY function syntax The GROUPBY function contains eight parameters: =GROUPBY(a,b,c,d,e,f,g,h) Parameters a to c are required: a (row field): A range (one column or multiple columns) containing the value or category to which the data is grouped. b (value): The range of values containing aggregated data (one column or multiple columns).
 Don't Hide and Unhide Columns in Excel—Use Groups InsteadApr 01, 2025 am 12:38 AM
Don't Hide and Unhide Columns in Excel—Use Groups InsteadApr 01, 2025 am 12:38 AMExcel efficient grouping: say goodbye to hidden columns and embrace flexible data management! While hidden columns can temporarily remove unnecessary data, grouping columns are often a better choice when dealing with large data sets or pursuing flexibility. This article will explain in detail the advantages and operation methods of Excel column grouping to help you improve data management efficiency. Why is grouping better than hiding? Hiding columns (right-click on the column title and select "Hide") can easily lead to data forgetting, even the column title prompt is not reliable because the title itself can be deleted. In contrast, grouped columns are faster and more convenient to expand and fold, which not only improves work efficiency, but also enhances user experience, especially when multi-person collaboration. Additionally, grouping columns allow creation of subgroups, which cannot be achieved by hidden columns. This is the number


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

SublimeText3 Chinese version
Chinese version, very easy to use

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

Dreamweaver Mac version
Visual web development tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.






