 Mobile Tutorial
Mobile Tutorial iPhone
iPhone What vulnerabilities are fixed in the official version of iOS/iPadOS 16.7? Is the update worth it?
What vulnerabilities are fixed in the official version of iOS/iPadOS 16.7? Is the update worth it?On the day the Apple iPhone 15 series was released, Apple released three system versions: iOS/iPadOS 17.0.1, iOS/iPadOS 17.0.2, and iOS/iPadOS 16.7.
The internal version number of this iOS/iPadOS 16.7 system update is 20H19. The official introduction is: "This update provides important bug fixes and security updates. , recommended for all users to install."

The following are the key fixes of this update found in Apple’s official support documents Three vulnerabilities:
CVE-2023-41992: A local attacker can escalate his or her privileges.
CVE-2023-41991: Malware can bypass signature verification.
CVE-2023-41993: A vulnerability in the processing of web content could allow execution of arbitrary code.
In addition, Apple today also released macOS Monterey 12.7, macOS Ventura 13.6 and other system updates, which also fix the above problems.
The official version of iOS / iPadOS 16.7 supports the following model upgrades:
iPhone X
iPhone 8 Plus
iPhone 8
iPad Pro (12.9 inches) 1st generation
iPad Pro (9.7 inches) 1st generation
iPad 5th generation
The new iPhone 15 series has been released. Apple has focused on iOS17 a few months ago. iOS/iPadOS 16.7 is likely to be the last major version update of iOS/iPadOS 16.
After a long period of repairs and improvements, iOS/iPadOS 16 has become more and more stable and has few bugs. If your old device feels unusable after upgrading to iOS17, it is better to choose iOS/iPadOS 16.7 for retirement.
The above is the detailed content of What vulnerabilities are fixed in the official version of iOS/iPadOS 16.7? Is the update worth it?. For more information, please follow other related articles on the PHP Chinese website!
 This Is Windows 11 Running on an iPadApr 25, 2025 pm 09:02 PM
This Is Windows 11 Running on an iPadApr 25, 2025 pm 09:02 PMsummary A developer used a virtual machine (VM) to run the Windows 11 ARM version on iPad Air. The simulation runs slowly and is not a practical alternative. European Union regulations allow users to sideload applications, making this possible. Thanks to the EU's increasingly strict regulations, Apple has been forced to significantly open to its hardware and software - Apple needs to comply with regulations or face the risk of being banned in one of its largest global markets. It is precisely because of the openness that these regulations allow, that someone seems to have successfully run a Windows 11 virtual machine on an iPad. This is really impressive. A developer successfully on Apple M2 iPad Ai
 30 Must-Know New Features in iOS 18.1 and iPadOS 18.1 That'll Make You Want to Update Apr 25, 2025 am 09:06 AM
30 Must-Know New Features in iOS 18.1 and iPadOS 18.1 That'll Make You Want to Update Apr 25, 2025 am 09:06 AMiOS 18.1 and iPadOS 18.1: A Deep Dive into the Latest Features The latest iOS and iPadOS update is here, brimming with exciting new features and improvements for your iPhone and iPad. From enhanced Apple Intelligence capabilities to streamlined Game
 Duolingo Will Now Teach You How to Play Games, TooApr 25, 2025 am 06:03 AM
Duolingo Will Now Teach You How to Play Games, TooApr 25, 2025 am 06:03 AMDuolingo launches a new chess course for players of all levels and teaches through interactive puzzles. The course includes small competitions and games against AI opponents. Duolingo’s goal is to make chess easier for beginners and experienced players through courses targeting different player skill levels. Duolingo has been the go-to choice for language learning for many years and has recently begun to get involved in teaching in other fields. Now, it wants to improve one of your specific skills—chess. Duolingo announced its latest project outside of linguistics: a comprehensive chess course designed to teach people of all levels to learn chess. Each of us has played chess in our lives, but that doesn't necessarily mean we're good at it
 How I Choose Sustainable Phone Accessories to Help the EarthApr 25, 2025 am 03:03 AM
How I Choose Sustainable Phone Accessories to Help the EarthApr 25, 2025 am 03:03 AMChoosing Sustainable Phone Accessories: A Guide to Eco-Friendly Tech Many prioritize style and functionality when buying phone accessories, but environmental impact is equally important. The constant cycle of purchasing and discarding plastic access
 The Apple Watch Series 10 Has Dropped to Its Lowest PriceApr 24, 2025 pm 09:06 PM
The Apple Watch Series 10 Has Dropped to Its Lowest PriceApr 24, 2025 pm 09:06 PMThe Apple Watch Series 10: A Slim, Smart Steal at $299 Introducing the Apple Watch Series 10, Apple's slimmest and most advanced wearable to date. Boasting a vibrant, wide-angle OLED display, advanced sleep apnea detection, and enhanced fitness trac
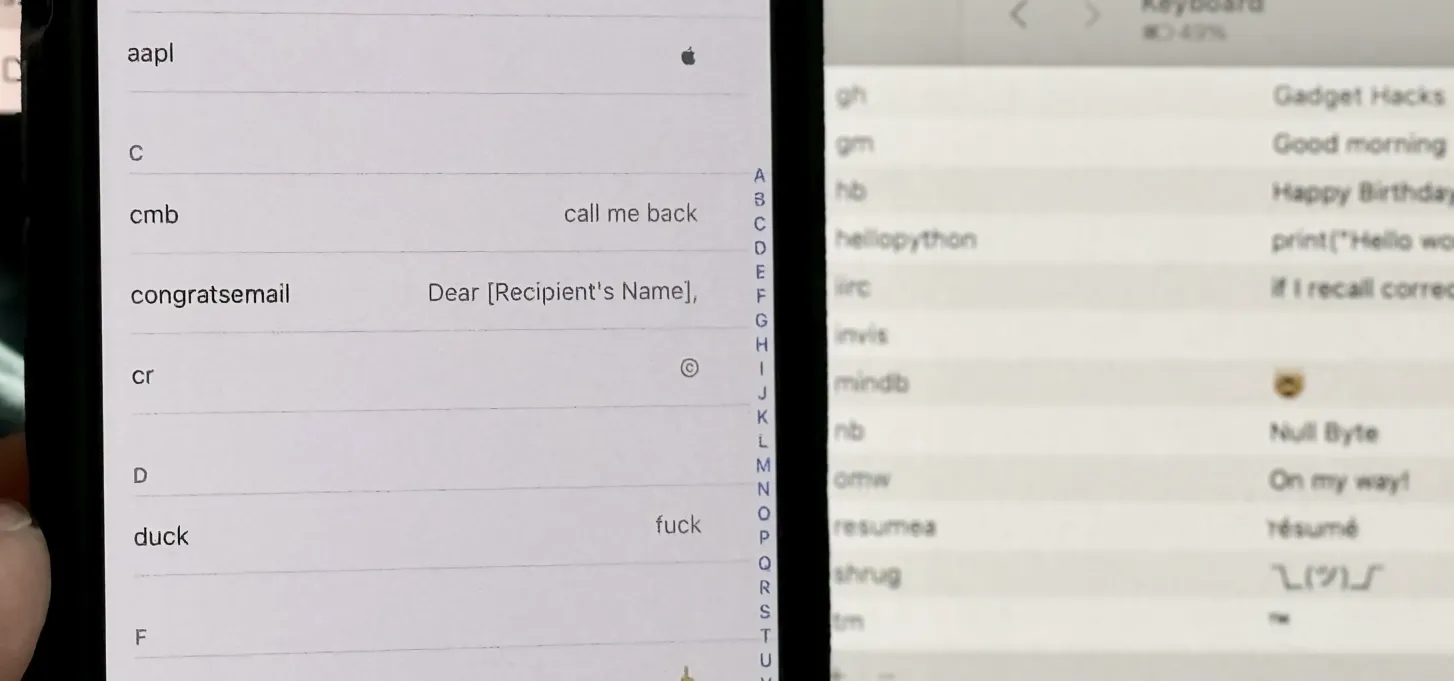 12 Reasons Why You Should Be Using Text Replacements on Your iPhone, iPad, or Mac Apr 24, 2025 am 11:05 AM
12 Reasons Why You Should Be Using Text Replacements on Your iPhone, iPad, or Mac Apr 24, 2025 am 11:05 AMUnlock the Power of Text Replacement: Supercharge Your Typing on iOS, iPadOS, and macOS! Apple's Text Replacement feature is a hidden gem, significantly boosting typing efficiency across your Apple devices. While many are aware of its existence, it
 17 New Accessibility Features Coming to iPhone and iPad with iOS 18 and iPadOS 18 Apr 24, 2025 am 10:00 AM
17 New Accessibility Features Coming to iPhone and iPad with iOS 18 and iPadOS 18 Apr 24, 2025 am 10:00 AMApple's upcoming iOS 18 and iPadOS 18: A wave of accessibility features benefiting everyone. WWDC will soon unveil Apple's plans for iOS 18 and iPadOS 18, but a sneak peek reveals impressive accessibility features launching this fall. These advancem
 Using These 8 Apps Has Reduced My Waste and Now I Can't Live Without ThemApr 23, 2025 pm 12:03 PM
Using These 8 Apps Has Reduced My Waste and Now I Can't Live Without ThemApr 23, 2025 pm 12:03 PM8 environmentally friendly apps help you easily reduce waste and start a sustainable life! Still worrying about garbage sorting and waste reduction? don’t worry! This article recommends 8 practical apps to help you easily start a journey of sustainable life! From garbage recycling reminders to second-hand transactions, to water-saving tracking, these apps can help you effectively reduce domestic waste and contribute to environmental protection. 1. Recycle Coach: Garbage Recycling Calendar and Classification Guide Recycle Coach is your indispensable garbage collection reminder app. It can clearly display the garbage recycling calendar in your area, including recycling time, recycling items and holiday adjustment information, and you no longer have to worry about missing garbage recycling days or classification errors! Garbage classification query is also provided in the app


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool





