 Software Tutorial
Software Tutorial Office Software
Office Software How to protect worksheets and unprotect Excel sheet without password
How to protect worksheets and unprotect Excel sheet without passwordThis tutorial demonstrates how to safeguard Excel spreadsheets with or without passwords, and how to recover access if a password is forgotten.
Protecting your worksheets, especially when sharing them externally, is crucial to prevent unauthorized modifications or data loss. Excel offers straightforward methods to lock sheets and password-protect workbooks.
Understanding Excel Worksheet Protection
It's important to understand that Excel's worksheet protection isn't a robust security measure. The encryption is relatively weak, particularly in older versions (pre-Excel 2010), making password cracking relatively easy. While newer versions employ stronger methods, complete security isn't guaranteed. Therefore, rely on sheet protection to prevent accidental changes, not to secure sensitive data.
For maximum security:
- Use the latest Excel versions with improved encryption.
- Implement strong, random passwords using a variety of alphanumeric characters and symbols.
- Protect the workbook structure to prevent manipulation of sheets.
- Employ separate passwords for opening and modifying the workbook.
- Store sensitive files in a secure location (e.g., an encrypted drive).
Protecting an Excel Sheet
-
Right-click a worksheet tab and select "Protect Sheet..." Alternatively, use the "Protect Sheet" button on the "Review" tab.

-
In the "Protect Sheet" dialog:
- Set a password (optional, but recommended to prevent accidental changes).
- Choose which actions users can perform (e.g., selecting cells, sorting, filtering). Restricting actions enhances protection.

-
Confirm the password.
Unprotecting an Excel Sheet
Unprotection is simple if you know the password:
- Right-click the sheet tab and select "Unprotect Sheet...".
- Use the "Unprotect Sheet" button on the "Review" tab.
- Use the "Unprotect Sheet" option under the "Home" tab's "Format" dropdown.



If password-protected, Excel will prompt for the password.
Unprotecting without a Password (for older versions)
For Excel 2010 and earlier, a VBA macro can bypass protection (though this is not recommended for ethical reasons). For newer versions, consider saving the file as an older .xls format, then applying the macro and converting back. Alternative methods include using third-party tools or Google Sheets. Copying the sheet contents to a new sheet can also work if certain actions are permitted.
Protecting a Workbook
To protect the workbook's structure (preventing sheet manipulation):
-
On the "Review" tab, click "Protect Workbook".
-
Select "Structure" (and optionally "Windows").
-
Set a password (optional).
-
Confirm the password.


To unprotect, click "Protect Workbook" again and enter the password.
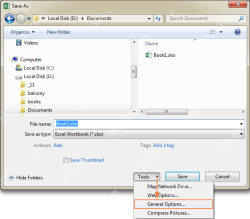
Password Protecting a Workbook from Opening or Modification
For stronger security, encrypt the workbook to prevent opening or modification:
- Opening: Use "Encrypt with Password" under "File" > "Info" > "Protect Workbook".
- Modification: Use "General Options" under "Save As" > "Tools" to set a "Password to modify".




To remove protection, repeat the steps and remove the password(s). Remember, these methods offer varying levels of security; consider additional security measures for highly sensitive data.
The above is the detailed content of How to protect worksheets and unprotect Excel sheet without password. For more information, please follow other related articles on the PHP Chinese website!
 How to Use the SORTBY Function in ExcelApr 25, 2025 am 01:00 AM
How to Use the SORTBY Function in ExcelApr 25, 2025 am 01:00 AMExcel's SORTBY function: a tool for efficient sorting Microsoft Excel provides a variety of data sorting methods, and the SORTBY function is undoubtedly the simplest and most convenient one. It allows you to dynamically sort data based on multiple arrays while maintaining the integrity of the original data. SORTBY function syntax The syntax of the SORTBY function is concise and clear: =SORTBY(a,b¹,b²,c¹,c²...) in: a (required) is the region or array to be sorted; b¹ (Required) is the first region or array to sort by; b² (optional) is the sort order of b¹; c¹ and c² (optional)
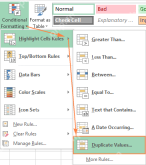 How to find and highlight duplicates in ExcelApr 24, 2025 am 10:42 AM
How to find and highlight duplicates in ExcelApr 24, 2025 am 10:42 AMThis tutorial shows you how to automatically highlight duplicate entries in Excel. We'll cover shading duplicate cells, entire rows, or consecutive duplicates using conditional formatting and a powerful add-in. Last week, we looked at using formulas
 How to identify duplicates in Excel: find, highlight, count, filterApr 24, 2025 am 10:06 AM
How to identify duplicates in Excel: find, highlight, count, filterApr 24, 2025 am 10:06 AMThe tutorial explains how to search for duplicates in Excel. You will learn a few formulas to identify duplicate values or find duplicate rows with or without first occurrences. You will also learn how to count instances of each duplicate
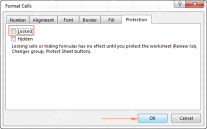 How to lock cells in Excel and unlock certain cells on a protected sheetApr 24, 2025 am 09:43 AM
How to lock cells in Excel and unlock certain cells on a protected sheetApr 24, 2025 am 09:43 AMThis tutorial explains how to safeguard specific Excel cells from accidental modification or unauthorized editing. It covers locking individual cells, unlocking cells on a protected sheet (with or without a password), and identifying locked/unlocked
 How to protect worksheets and unprotect Excel sheet without passwordApr 24, 2025 am 09:27 AM
How to protect worksheets and unprotect Excel sheet without passwordApr 24, 2025 am 09:27 AMThis tutorial demonstrates how to safeguard Excel spreadsheets with or without passwords, and how to recover access if a password is forgotten. Protecting your worksheets, especially when sharing them externally, is crucial to prevent unauthorized mo
 Don't Ignore the Power of F4 in Microsoft ExcelApr 24, 2025 am 06:07 AM
Don't Ignore the Power of F4 in Microsoft ExcelApr 24, 2025 am 06:07 AMA must-have for Excel experts: the wonderful use of the F4 key, a secret weapon to improve efficiency! This article will reveal the powerful functions of the F4 key in Microsoft Excel under Windows system, helping you quickly master this shortcut key to improve productivity. 1. Switching formula reference type Reference types in Excel include relative references, absolute references, and mixed references. The F4 keys can be conveniently switched between these types, especially when creating formulas. Suppose you need to calculate the price of seven products and add a 20% tax. In cell E2, you may enter the following formula: =SUM(D2 (D2*A2)) After pressing Enter, the price containing 20% tax can be calculated. But,
 Count unique and distinct values in Excel with formula or pivot tableApr 23, 2025 am 11:21 AM
Count unique and distinct values in Excel with formula or pivot tableApr 23, 2025 am 11:21 AMThis tutorial shows you how to count unique and distinct values in Excel using formulas and PivotTables. We'll cover counting unique names, text, numbers, and case-sensitive values, as well as handling blank cells. The key difference between "u
 COUNT and COUNTA functions to count cells in ExcelApr 23, 2025 am 10:46 AM
COUNT and COUNTA functions to count cells in ExcelApr 23, 2025 am 10:46 AMThis tutorial provides a concise overview of Excel's COUNT and COUNTA functions, illustrating their use with practical examples. You'll also learn how to leverage COUNTIF and COUNTIFS for counting cells based on specific criteria. Excel excels at nu


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

SublimeText3 Linux new version
SublimeText3 Linux latest version

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.









