 System Tutorial
System Tutorial Windows Series
Windows Series What to do if win10 shared files do not have permission to access win10 shared files do not have permission to access detailed explanation
What to do if win10 shared files do not have permission to access win10 shared files do not have permission to access detailed explanationHello everyone, we often use shared folders as a tool at work, but sometimes there is a problem that win10 shared files do not have permission to access. Don't worry, I'll teach you how to solve this problem. First, we open the service page, then find the workstation option, and then we can operate it! Now, let’s learn more about how to solve this problem!
Detailed explanation of win10 shared files without permission to access
1. First, we need to press the win key and r key on the keyboard to open the run window, and then enter the [services, msc] command, and then Click OK.

2. Enter the service page, find the [workstation] option on the page, and double-click it to enter.

3. On the page that opens, if your workstation is not enabled, then we need to click the start button to run it.

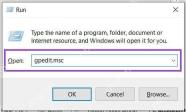
4. Next, we open the run window, enter the [gepdit, msc] options, and then click the OK button to enter.

5. In the window that opens, click [Computer Configuration-Windows Settings-Security Settings-Local Policy-Security Options] on the left to open, and then click on the right Find [Sharing and Security Model for Local Accounts] on the side and double-click it.

6. In the page that opens, we need to set [Classic - authenticate local users without changing their original identity], and then click OK.

7. Next, we right-click the folder to be shared and select the [Properties] option to enter.

8. In the page that opens, we need to click the [Sharing] tab, and then click [Advanced Sharing].

9. Then, in the advanced sharing page that opens, click [Permissions], click and check [Read] in the next window, and then click Click the OK button to save.

The above is the detailed content of What to do if win10 shared files do not have permission to access win10 shared files do not have permission to access detailed explanation. For more information, please follow other related articles on the PHP Chinese website!
 Western Digital Is Preparing 40TB HDDs, but It's Not Stopping ThereApr 25, 2025 am 09:01 AM
Western Digital Is Preparing 40TB HDDs, but It's Not Stopping ThereApr 25, 2025 am 09:01 AMWestern Digital's 40TB HDDs: A Stepping Stone to 100TB Western Digital (WD) is gearing up to launch 40TB hard disk drives (HDDs), but their ambitions extend far beyond that. This move is a crucial step in WD's roadmap to achieve its ambitious goal:
 6 Reasons to Try Windows Subsystem for Linux (WSL)Apr 25, 2025 am 06:09 AM
6 Reasons to Try Windows Subsystem for Linux (WSL)Apr 25, 2025 am 06:09 AMWindows Subsystem for Linux (WSL): Your Gateway to the Linux World While Windows enjoys widespread consumer popularity for its user-friendliness, Linux dominates the professional sphere. Whether you're a curious beginner or seeking seamless Windows-
 Don't Throw Out That Old Keyboard, Fix Up It Up InsteadApr 25, 2025 am 06:01 AM
Don't Throw Out That Old Keyboard, Fix Up It Up InsteadApr 25, 2025 am 06:01 AMHow to Clean and Repair a Broken Keyboard I always have some tools ready before starting to repair any computer parts: Precision screwdriver set Cotton swab Isopropanol Magnetic bowl In addition, you need gentle dishwashing liquid, toothpicks, compressed air and keycap puller. Easy to pull out the key caps. After preparing the materials, you must first determine the degree of damage to the keyboard. Be sure to check for damage to the cable first. Just stained with soda and dust? Or are mechanical parts damaged? Or is there a circuit problem? The easiest first step to diagnose a problem is to open Notepad (or other plain text editor) and press each key on the keyboard to make sure they all appear correctly in Notepad. Note any keys that don't work, are difficult to press, or are stuck. Be sure to check all Cs on your keyboard
 Intel Arrow Lake CPUs Are Getting a Speed Boost, but You Need an UpdateApr 25, 2025 am 03:01 AM
Intel Arrow Lake CPUs Are Getting a Speed Boost, but You Need an UpdateApr 25, 2025 am 03:01 AMIntel's Free Arrow Lake Overclocking Boost: Faster Gaming for Core Ultra CPUs Your Intel Core Ultra 200-series processor might already be a powerhouse, but Intel's latest free update delivers a significant performance boost for gamers. The "Int
 Windows 11 Fixed My Biggest Problem With The TaskbarApr 25, 2025 am 01:10 AM
Windows 11 Fixed My Biggest Problem With The TaskbarApr 25, 2025 am 01:10 AMWindows 11 Taskbar's New "End Task" Button: A Game Changer for App Closing Closing stubborn or frozen apps on Windows has always been a hassle. The simple "Close" button often fails to completely shut down background processes.
 You Should Be Buying Used MonitorsApr 25, 2025 am 01:09 AM
You Should Be Buying Used MonitorsApr 25, 2025 am 01:09 AMComputer monitors boast impressive longevity, outlasting many other PC components. Unlike components with moving parts like hard drives or fans, monitors, particularly VA and IPS types, have a simple design with no moving parts, resulting in extende
 How to Disable Access to Settings in Windows Apr 24, 2025 pm 08:01 PM
How to Disable Access to Settings in Windows Apr 24, 2025 pm 08:01 PMRestricting Access to Windows Settings: Two Proven Methods Many users don't require, and shouldn't have, access to Windows settings that could potentially harm the system. This is especially critical in shared environments or networks where unauthori
 Lenovo's First 2025 ThinkPads Have AMD's Zen 5 And Intel's Arrow Lake ChipsApr 24, 2025 am 09:17 AM
Lenovo's First 2025 ThinkPads Have AMD's Zen 5 And Intel's Arrow Lake ChipsApr 24, 2025 am 09:17 AMLenovo Unveils Revamped ThinkPad Lineup with Cutting-Edge Processors Lenovo has announced a major update to its iconic ThinkPad laptop series, introducing new models across the P, L, and X1 ranges. These laptops boast the latest in processor technol


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Dreamweaver CS6
Visual web development tools

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

SublimeText3 Linux new version
SublimeText3 Linux latest version

SublimeText3 Mac version
God-level code editing software (SublimeText3)





