 Development tools
Development tools php development environment (integrated)
php development environment (integrated) Website malicious web Trojan scanner (WebshellScanner)
Website malicious web Trojan scanner (WebshellScanner)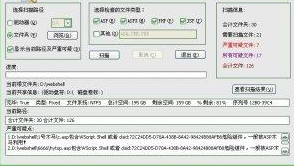
Main functions of the software:
1. Search for web Trojans (Webshell) in the website
2. Generate statistical reports
It is used to check whether the website has been hacked. It is generally used for operations on the server, or to download the source code on the server to the local, and then use this software to search.
We have dealt with everyone's requests for the first version, fixed some minor bugs, and added an automatic update program. The test passed in windows2003, windows xp, windows 2000 server without .net environment. The simple update instructions are as follows:
1. Add automatic upgrade module, online upgrade can be completed in .net environment;
-------------------------------------------------- ------
Upgrading requires requesting the server to download file replacement. If the download fails, please download the update manually. The update program requires the server to be installed with .net v2.0.50727 or above in order to run, so servers that do not support .net cannot use automatic updates.
2. No .net environment is required to run the scanner;
-------------------------------------------------- ------
This problem is quite troublesome. The program is developed in .NET and needs to install the .NET Framework. However, Windows 2000, Windows XP and Windows 2003 do not have a .NET 2.0 operating environment by default. Therefore, using the principle of Mobile Fetion and using fetion's program to load the main program, the main program can run in an environment that does not support .net. You can use the files in the VMDotNet package to run most .net developed programs. If the dll is missing, just add it.
3. Add asp rules, mainly for the webshell bypass mechanism of asp;
-------------------------------------------------- ------
Since the original rules are basically lake2 rules and a slightly modified version, many comrades have found many mechanisms to bypass detection, such as using access or excel to create asp files, including tricks such as include gif, etc. etc. These bypass mechanisms are all addressed in this release. (Friends who still want to bypass it, try to see if my regular expression is robust or not)
4. Update php rules and add a few encryption functions running under eval;
-------------------------------------------------- ------
Under PHP, encrypted files are first decrypted through functions and then run through eval. This version handles several uncommon functions: gzinflate, str_rot13, etc. PHP does have many bypass methods, and it is difficult to detect. Alas, I No choice...
5. Added checks for shells that exploit IIS6.0 folder parsing vulnerabilities and file parsing vulnerabilities;
-------------------------------------------------- ------
There is nothing to say about this. The directory is called 1.asp or the file is called 1.asp;2.jpg. It is obviously hacked and needs to be carefully checked to check the problem.
6. Fixed a bug (the first directory under the drive cannot be scanned);
-------------------------------------------------- ------
I discovered it accidentally during testing. It seems that no one has submitted this problem to me. I guess everyone scanned the directory directly and did not scan the disk (there is really no need to scan the disk~)
All resources on this site are contributed by netizens or reprinted by major download sites. Please check the integrity of the software yourself! All resources on this site are for learning reference only. Please do not use them for commercial purposes. Otherwise, you will be responsible for all consequences! If there is any infringement, please contact us to delete it. Contact information: admin@php.cn
Related Article
 Which C IDE is Best for Windows Developers?
Which C IDE is Best for Windows Developers?11Nov2024
Choosing the Optimal C Development Environment on WindowsWhen it comes to selecting an Integrated Development Environment (IDE) or editor for...
 The 5 Best IDEs for WordPress Development (And Why)
The 5 Best IDEs for WordPress Development (And Why)03Mar2025
Choosing the Right Integrated Development Environment (IDE) for WordPress Development For ten years, I've explored numerous Integrated Development Environments (IDEs) for WordPress development. The sheer variety—from free to commercial, basic to fea
 Install Apache2.4 MySql5.7 PHP5.6 under windows environment, apache2.4mysql5.7_PHP tutorial
Install Apache2.4 MySql5.7 PHP5.6 under windows environment, apache2.4mysql5.7_PHP tutorial12Jul2016
Install Apache2.4 MySql5.7 PHP5.6, apache2.4mysql5.7 under windows environment. Install Apache2.4 MySql5.7 PHP5.6, apache2.4mysql5.7 under Windows environment. Before learning PHP, I always only used the phpStudy integrated development environment. This is undoubtedly a great help for novices, because
 How Docker arranges PHP development environment, docker arranges PHP development
How Docker arranges PHP development environment, docker arranges PHP development06Jul2016
How Docker arranges PHP development environment, docker arranges PHP development. How Docker arranges PHP development environment, docker arranges PHP development environment deployment has always been a big problem, whether it is development environment or production environment, but Docker combines development environment and production environment
 How Docker arranges PHP development environment, docker arranges PHP development_PHP tutorial
How Docker arranges PHP development environment, docker arranges PHP development_PHP tutorial12Jul2016
How Docker arranges PHP development environment, docker arranges PHP development. How Docker arranges PHP development environment, docker arranges PHP development environment deployment has always been a big problem, whether it is development environment or production environment, but Docker combines development environment and production environment
 How to Access the Command Line for XAMPP on Windows?
How to Access the Command Line for XAMPP on Windows?18Oct2024
Accessing the Command Line for XAMPP on WindowsXAMPP, the popular web development package, provides an integrated development environment on Windows. It includes essential components such as Apache, MySQL, and PHP. However, unlike Linux-based systems


Hot Tools
Hailink virtual serial port v1.0.0.2
Hailink virtual serial port v1.0.0.2
Super batch batch text replacement V5.02 green version (server web page hanging horse batch replacement)
Super batch batch text replacement V5.02 green version (server web page hanging horse batch replacement)

Dragon Shield Feibao Web Trojan Remover
Dragon Shield Feibao Web Trojan Remover

McAfee VirusScan Enterprise 8.8 Licensed Edition
McAfee VirusScan Enterprise 8.8 Licensed Edition

Server security dog
Server security dog



