What is a file handle in Windows? How is it done?
What are the file handles?
1. Question 1: What are the file handles? In file I/O, to read data from a file, the application must first call the operating system function and transfer the file name, and select a path to the file to open. document. This function gets back a sequence number, that is, the file handle (filehandle), which is the only basis for identification of the open file.
2. The handle is a special smart watch pointer. When an application wants to reference a memory block or object managed by another system (such as a database, operating system), a handle is used. 2. The foundation of the entire Windows programming.

3. The handle is a (generally 32-bit) integer, which represents an object. Handles in Windows are similar to file handles used in traditional C or MS-DOS programming. Programs almost always obtain handles by calling Windows functions. Programs use this handle in other Windows functions to use the object it represents.
4. Handles are unique integers used by WINDOWS to identify objects built or used by applications. WINDOWS uses various handles to identify examples such as application instances, windows, controls, bitmaps, GDI objects, etc. The WINDOWS handle is a bit like a file handle in C language.
5. The handle is a serial number, not a video memory address. It is used by the operating system to query the address of the kernel object. PID is the process number Linux environment variable, which is the ID number assigned to the process by the operating system.
6, handle), this file handle is the only basis for identification of the open file. To read a piece of data from a file, the application needs to call the function ReadFile and transmit the address of the file handle in the video memory and the number of bytes to be copied to the operating system. When the task is completed, the file is closed by calling a system function.
aix set file handle configuration
The AIX file descriptor limit is set in the /etc/security/limits file linux file handle , its default value is 2000. This limit can be modified via the ulimit command or the setrlimit subinterpreter. The maximum size is defined by the OPEN_MAX constant.
(1) Use the ftp command: Set the ASCII transmission type to transmit between a machine running AIX and another machine running Windows. I won’t go into details here.
Configure the array as described in the previous article and assign LUNs to the hosts. Connect optical fibers, one card per card, to two switches on two fabrics. Partition the two switches linux file handle, and the partitions must be appropriate to ensure that the initiator and target are visible to each other. Make sure all LUNs are visible.
The lack of permissions for aixftp may be due to the following reasons: Incorrect permission settings: aixftp may not be configured and authorized correctly. In Unix/Linux systems, file transfer contract (FTP) access permissions are controlled by setting file system permissions and the configuration file of the FTP server.
What should I do if the notebook handle is invalid?
How to deal with invalid handles: Usually this problem occurs because there is a problem with the driver of the copier. You can first try to delete the copier and then reinstall the driver. Open: C:\WINDOWS\system32\spool\driver on the notebook where the driver was added and delete all old drivers.
Solution: Is this warning sound due to the installation of third-party software? If so, it is recommended to uninstall it and not use the Linux system installation tutorial, or to check if there is a problem with the game itself. You can uninstall it and re-download and install it. The system cannot load user configuration, but can load default configuration.
Therefore, this is a problem with the web page, and the solution is as described above. Problem 9: The copier handle is invalid. When installing the driver to the last step of installing the driver, it always displays that the handle is invalid. Through the prompts, it may be caused by a problem with the driver or laptop system.
Next, the editor will give you a detailed solution to the problem that the VM virtual machine handle is invalid and cannot be started under the XP system.
The above is the detailed content of What is a file handle in Windows? How is it done?. For more information, please follow other related articles on the PHP Chinese website!
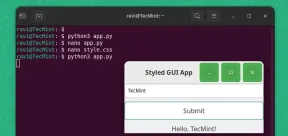 How to Create GUI Applications In Linux Using PyGObjectMay 13, 2025 am 11:09 AM
How to Create GUI Applications In Linux Using PyGObjectMay 13, 2025 am 11:09 AMCreating graphical user interface (GUI) applications is a fantastic way to bring your ideas to life and make your programs more user-friendly. PyGObject is a Python library that allows developers to create GUI applications on Linux desktops using the
 How to Install LAMP Stack with PhpMyAdmin in Arch LinuxMay 13, 2025 am 11:01 AM
How to Install LAMP Stack with PhpMyAdmin in Arch LinuxMay 13, 2025 am 11:01 AMArch Linux provides a flexible cutting-edge system environment and is a powerfully suited solution for developing web applications on small non-critical systems because is a completely open source and provides the latest up-to-date releases on kernel
 How to Install LEMP (Nginx, PHP, MariaDB) on Arch LinuxMay 13, 2025 am 10:43 AM
How to Install LEMP (Nginx, PHP, MariaDB) on Arch LinuxMay 13, 2025 am 10:43 AMDue to its Rolling Release model which embraces cutting-edge software Arch Linux was not designed and developed to run as a server to provide reliable network services because it requires extra time for maintenance, constant upgrades, and sensible fi
![12 Must-Have Linux Console [Terminal] File Managers](https://img.php.cn/upload/article/001/242/473/174710245395762.png?x-oss-process=image/resize,p_40) 12 Must-Have Linux Console [Terminal] File ManagersMay 13, 2025 am 10:14 AM
12 Must-Have Linux Console [Terminal] File ManagersMay 13, 2025 am 10:14 AMLinux console file managers can be very helpful in day-to-day tasks, when managing files on a local machine, or when connected to a remote one. The visual console representation of the directory helps us quickly perform file/folder operations and sav
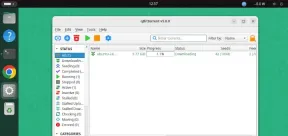 qBittorrent: A Powerful Open-Source BitTorrent ClientMay 13, 2025 am 10:12 AM
qBittorrent: A Powerful Open-Source BitTorrent ClientMay 13, 2025 am 10:12 AMqBittorrent is a popular open-source BitTorrent client that allows users to download and share files over the internet. The latest version, qBittorrent 5.0, was released recently and comes packed with new features and improvements. This article will
 Setup Nginx Virtual Hosts, phpMyAdmin, and SSL on Arch LinuxMay 13, 2025 am 10:03 AM
Setup Nginx Virtual Hosts, phpMyAdmin, and SSL on Arch LinuxMay 13, 2025 am 10:03 AMThe previous Arch Linux LEMP article just covered basic stuff, from installing network services (Nginx, PHP, MySQL, and PhpMyAdmin) and configuring minimal security required for MySQL server and PhpMyadmin. This topic is strictly related to the forme
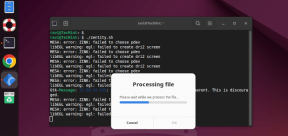 Zenity: Building GTK Dialogs in Shell ScriptsMay 13, 2025 am 09:38 AM
Zenity: Building GTK Dialogs in Shell ScriptsMay 13, 2025 am 09:38 AMZenity is a tool that allows you to create graphical dialog boxes in Linux using the command line. It uses GTK , a toolkit for creating graphical user interfaces (GUIs), making it easy to add visual elements to your scripts. Zenity can be extremely u
 Top 22 Best Music Players for LinuxMay 13, 2025 am 09:25 AM
Top 22 Best Music Players for LinuxMay 13, 2025 am 09:25 AMSome may describe it as their passion, while others may consider it a stress reliever or a part of their daily life. In every form, listening to music has become an inseparable part of our lives. Music plays different roles in our lives. Sometimes it


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Dreamweaver Mac version
Visual web development tools

Dreamweaver CS6
Visual web development tools

SublimeText3 Chinese version
Chinese version, very easy to use






