php editor Zimo will introduce to you how to cancel the "read-only mode" of a Word document. When we cannot edit a Word document, it may be because the document is set to read-only mode. To deactivate read-only mode, just right-click on the file, select "Properties", cancel the "read-only" option, and save. In addition, you can also copy the document content to a new document, so that you can continue to edit and save the document. Hope these methods can help you solve the problem of document read-only mode.
How to cancel this mode?
First of all, we need to check whether the "read-only mode" is simply set, or whether the "restricted password" is set.
Because these two methods will make the Word document invisible and unable to perform other operations. To be more precise, the read-only mode can be edited, but the original file cannot be saved, and the password restriction makes it completely inoperable.
If you only set the "read-only mode", we can see the words "read-only" at the top of the word document.
 .
.
In this "read-only mode", we only need to save this Word document as a new document, and the "read-only mode" will be cancelled.
 .
.
If the "read-only mode" that restricts passwords is set, we can see that in the Word document, the toolbars above are gray and cannot be used.
 .
.
At this time, the restriction can only be lifted by entering the password. First, find [Review] on the upper toolbar, and then click [Restrict Editing];
 .
.
Click [Stop Protection] under [Restrict Editing], and a password dialog box will appear. As long as you enter the password, the restriction can be removed, and the restricted editing in "read-only mode" will be revoked.

.
If you don’t remember this restriction password, you cannot cancel this mode, because Word does not have a password recovery option, and it cannot be removed directly.
If it doesn't work after trying several times, we have a simpler way to directly remove the "restrictions" of the Word document with the help of relevant tools.
For example, the Pepsi Niu Word password recovery tool imports the Word document into the "Unrestriction" interface. After clicking [Start], you can directly remove the "restricted editing" of the Word document without a password.
Tool link: Pepsi Niu Word Password Recovery Tool

The Word document after the restriction is lifted will be saved as a new document. Click [Go to View] to find it.

The above is the detailed content of How to revoke the 'read-only mode' of a Word document?. For more information, please follow other related articles on the PHP Chinese website!
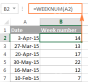 Excel WEEKNUM function – convert week number to date and vice versaMay 09, 2025 am 11:11 AM
Excel WEEKNUM function – convert week number to date and vice versaMay 09, 2025 am 11:11 AMExcel's WEEKNUM function: Your guide to week number calculations While Excel offers numerous functions for dates, the WEEKNUM function stands alone for week number calculations. This tutorial explores its syntax, arguments, and practical applications
 Excel MONTH function - month name from date, last day of month, etc.May 09, 2025 am 10:59 AM
Excel MONTH function - month name from date, last day of month, etc.May 09, 2025 am 10:59 AMThis tutorial delves into the intricacies of Excel's MONTH and EOMONTH functions. Through numerous formula examples, you'll learn to extract month information from dates, determine the first and last days of any month, convert between month names an
 WEEKDAY formula in Excel to get day of week, weekends and workdaysMay 09, 2025 am 10:25 AM
WEEKDAY formula in Excel to get day of week, weekends and workdaysMay 09, 2025 am 10:25 AMIf you are looking for an Excel function to get day of week from date, you've landed on the right page. This tutorial will teach you how to use the WEEKDAY formula in Excel to convert a date to a weekday name, filter, highlight and count
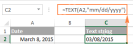 Convert date to text in Excel - TEXT function and no-formula waysMay 09, 2025 am 10:11 AM
Convert date to text in Excel - TEXT function and no-formula waysMay 09, 2025 am 10:11 AMThis article explores several methods for converting Excel dates into text strings, offering both formula-based and non-formula solutions. Traditionally, we start with a formula solution and then explore a couple of non-formula alternatives. Using
 Excel: convert text to date and number to dateMay 09, 2025 am 09:36 AM
Excel: convert text to date and number to dateMay 09, 2025 am 09:36 AMThis tutorial demonstrates various Excel techniques for converting text and numbers into dates, including both formula-based and non-formula methods. You'll learn to efficiently transform text strings into usable date formats. Often, dates imported
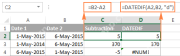 How to add and subtract dates in ExcelMay 08, 2025 am 11:36 AM
How to add and subtract dates in ExcelMay 08, 2025 am 11:36 AMIn this tutorial, you will find a variety of useful formulas to add and subtract dates in Excel, such as subtracting two dates, adding days, weeks, months and years to a date, and more. If you have been following our tutorials to working
 Excel WORKDAY and NETWORKDAYS functions to calculate working daysMay 08, 2025 am 10:49 AM
Excel WORKDAY and NETWORKDAYS functions to calculate working daysMay 08, 2025 am 10:49 AMThis tutorial demonstrates how to use Excel's WORKDAY, WORKDAY.INTL, NETWORKDAYS, and NETWORKDAYS.INTL functions to efficiently calculate weekdays, considering custom weekend settings and holidays. Microsoft Excel offers specialized functions for wor
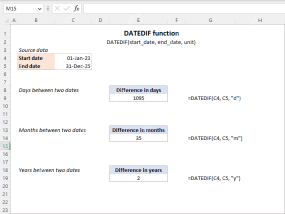 Excel DATEDIF function to get difference between two datesMay 08, 2025 am 10:45 AM
Excel DATEDIF function to get difference between two datesMay 08, 2025 am 10:45 AMThis tutorial provides a concise explanation of Excel's DATEDIF function and offers formula examples for calculating date differences in days, weeks, months, or years. We've previously covered date and time manipulation in Excel, including formattin


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 Chinese version
Chinese version, very easy to use

WebStorm Mac version
Useful JavaScript development tools

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

Zend Studio 13.0.1
Powerful PHP integrated development environment






