php editor Xinyi found that many users encountered a common problem when using Windows computers, that is, they could not open photos in iPhone. This problem may cause a lot of inconvenience to users and affect their daily use experience. In response to this problem, we will introduce several solutions for you in this article to help you easily open photos on your iPhone and solve the problem.
In the phone settings, change the camera settings from "High Efficiency" to "Best Compatibility" so that the photos taken will be saved in jpg format for normal viewing on Windows computers.

Open [Pepsi Cow HEIC Picture Expert] for direct conversion on your computer, add the pictures that need to be processed (can be batched), and select the format supported by Windows computers (jpg, png and other regular formats).

After the conversion is successful, click [View File] to directly open the folder where the converted pictures are located.

[Pepsi Cow HEIC Picture Expert] Official download address: https://dl.passneo.cn/down/down?path=passneo_heic_tool_setup.exe
The above is the detailed content of Can't open photos from iPhone on windows computer. For more information, please follow other related articles on the PHP Chinese website!
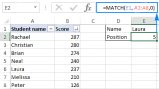 Excel MATCH function with formula examplesApr 15, 2025 am 11:21 AM
Excel MATCH function with formula examplesApr 15, 2025 am 11:21 AMThis tutorial explains how to use MATCH function in Excel with formula examples. It also shows how to improve your lookup formulas by a making dynamic formula with VLOOKUP and MATCH. In Microsoft Excel, there are many different lookup/ref
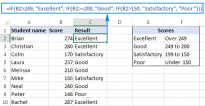 Nested IF in Excel – formula with multiple conditionsApr 15, 2025 am 11:13 AM
Nested IF in Excel – formula with multiple conditionsApr 15, 2025 am 11:13 AMThis tutorial demonstrates how to effectively use multiple IF functions in Microsoft Excel, showcasing nested IF formulas for various tasks. The core concept is using nested IF statements to evaluate multiple conditions and return different results
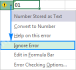 Leading zeros in Excel: how to add, remove and hideApr 15, 2025 am 09:31 AM
Leading zeros in Excel: how to add, remove and hideApr 15, 2025 am 09:31 AMThis tutorial explores various methods for managing leading zeros in Excel, covering their preservation, display, and removal. Whether you're working with zip codes, IDs, or other data requiring leading zeros, this guide provides solutions. Excel of
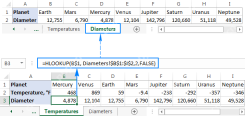 Excel HLOOKUP function with formula examplesApr 15, 2025 am 09:05 AM
Excel HLOOKUP function with formula examplesApr 15, 2025 am 09:05 AMMicrosoft Excel's HLOOKUP function: A comprehensive guide Excel offers three lookup functions – LOOKUP, VLOOKUP, and HLOOKUP – but HLOOKUP often causes confusion. This tutorial clarifies HLOOKUP's specifics and provides examples for efficient use. Wh
 If You Don't Rename Tables in Excel, Today's the Day to StartApr 15, 2025 am 12:58 AM
If You Don't Rename Tables in Excel, Today's the Day to StartApr 15, 2025 am 12:58 AMQuick link Why should tables be named in Excel How to name a table in Excel Excel table naming rules and techniques By default, tables in Excel are named Table1, Table2, Table3, and so on. However, you don't have to stick to these tags. In fact, it would be better if you don't! In this quick guide, I will explain why you should always rename tables in Excel and show you how to do this. Why should tables be named in Excel While it may take some time to develop the habit of naming tables in Excel (if you don't usually do this), the following reasons illustrate today
 Microsoft 365 Will Turn Off ActiveX, Because Hackers Keep Using ItApr 12, 2025 am 06:01 AM
Microsoft 365 Will Turn Off ActiveX, Because Hackers Keep Using ItApr 12, 2025 am 06:01 AMMicrosoft 365 is finally phasing out ActiveX, a long-standing security vulnerability in its Office suite. This follows a similar move in Office 2024. Beginning this month, Windows versions of Word, Excel, PowerPoint, and Visio in Microsoft 365 will
 How to Use Excel's AGGREGATE Function to Refine CalculationsApr 12, 2025 am 12:54 AM
How to Use Excel's AGGREGATE Function to Refine CalculationsApr 12, 2025 am 12:54 AMQuick Links The AGGREGATE Syntax


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

Zend Studio 13.0.1
Powerful PHP integrated development environment

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.






