
Deploying artificial intelligence at the edge has the potential to unleash powerful real-time analytics and processing. Use cases include industrial automation, remote monitoring and healthcare.
Edge deployment of artificial intelligence refers to deploying artificial intelligence models and algorithms on edge devices or local servers instead of relying on cloud-based processing. This approach brings AI capabilities to the point where the data is generated, allowing for faster and more efficient processing, real-time analysis, and reduced reliance on internet connectivity.
The concept of edge computing forms the basis for edge artificial intelligence deployment. This involves allocating resources and data storage to the edge of the network where the data originates. Embedded devices such as smartphones, IoT devices, cameras, and drones can all serve as platforms for deploying AI models.
Edge deployments enable real-time analysis of data streams without relying on cloud connections or external servers, thereby facilitating real-time decision-making. This localization addresses concerns about data privacy and security because the information does not need to be transferred to the cloud. Analyzing data from edge devices themselves can reduce the risk of access or potential data breaches.
Edge AI deployments prioritize delivering insights or aggregated results to minimize network congestion and reduce latency. It uses a hybrid architecture that combines edge deployments and cloud-based processing to create a distributed system.
Edge deployment allows customization and adaptive AI models to meet the needs of edge devices, applications, or users. Models can be tuned to optimize their performance and efficiency based on the limitations of edge hardware. Additionally, edge deployments enable distributed learning across multiple edge devices, which involves AI training models without centralizing data. This approach ensures privacy and preserves model training while leveraging the dataset.
Benefits of edge AI deployment
The benefits of edge AI deployment make it attractive for a range of applications in industries such as healthcare, manufacturing, transportation, surveillance and smart cities force choice.
Let’s discuss the benefits of artificial intelligence edge deployment.
Real-time decision-making
By processing data on edge devices, artificial intelligence algorithms can provide real-time decisions. This capability is important in use cases such as vehicles, industrial automation and critical infrastructure monitoring, where instant insights are critical for safe and efficient operations.
Data flow analysis
Edge deployment enables efficient analysis of data flows. By processing data on edge devices, AI models can provide insights and predictions. This proves advantageous in applications that require rapid action, such as fraud detection, anomaly detection, predictive maintenance and monitoring systems.
Privacy and Security
Edge AI deployments enhance data privacy and security measures. Rather than transmitting data to the cloud for processing, AI algorithms run locally on edge devices. This minimizes risks associated with data exposure during transfer and resolves issues related to data privacy regulations. Critical data remains within the scope of the network, increasing security.
Reduce data transmission to the cloud
Edge deployments minimize the need to send large amounts of data to the cloud. By processing and filtering data, AI edge deployments send only relevant insights or aggregated results. This optimization helps optimally utilize network resources, reduce transmission costs, and alleviate network congestion.
Reduce dependence on internet connectivity
Edge AI enables AI applications to work offline or in environments with intermittent internet connections. AI models are deployed directly on edge devices, which enables them to perform processing without relying on cloud connectivity. This ensures that AI functionality can still be accessed and run even when a reliable network connection is not present.
Flexibility and Customization
Edge deployment provides the flexibility to customize and adjust AI models based on specific edge device, application or user needs. AI models can be customized to fit the constraints and capabilities of edge hardware. This adaptability improves performance, reduces resource usage and optimizes energy efficiency.
5 Practical Applications of Deploying Artificial Intelligence at the Edge
Here are some practical applications where deploying artificial intelligence at the edge brings benefits.
1. Self-driving cars
Deploying artificial intelligence at the edge is crucial for self-driving cars as it enables real-time processing and decision-making for safe navigation. The use of artificial intelligence algorithms on in-car devices can help enable real-time perception, object recognition and collision avoidance. This reduces latency and improves real-time responsiveness.
2. Industrial Automation
The deployment of artificial intelligence at the edge is widely used in factory automation to achieve real-time analysis and control. Equipping edge devices with AI models can help optimize manufacturing processes, detect anomalies, predict equipment failures and enable maintenance. This increases efficiency, reduces downtime and saves costs.
3. Remote monitoring
Deploying artificial intelligence at the edge can monitor infrastructure and remote locations. In oil and gas pipelines, for example, AI-equipped edge devices can perform real-time analysis of sensor data to detect leaks, anomalies or safety threats. Likewise, in environmental monitoring scenarios, edge devices can analyze sensor data to track air quality levels, weather patterns, and natural disaster events.
4. Healthcare
Deploying artificial intelligence at the edge has value in healthcare environments, such as remote patient monitoring applications, real-time diagnostics, and personalized healthcare. Edge devices, such as medical sensors, can directly analyze information from the device itself. This enables any health abnormalities to be identified and insights shared with healthcare professionals in a timely manner. Therefore, it facilitates healthcare interventions and reduces dependence on constant cloud connectivity.
5. Monitoring systems
Deploying artificial intelligence on edge devices is also valuable for monitoring systems because it can enhance real-time threat detection and response. Equipping edge devices with AI models can analyze video feeds locally to identify activity and trigger alerts or actions. This eliminates the need to stream video to the cloud. This can improve the overall efficiency and effectiveness of the surveillance system.
Efficient Data Management in Edge Artificial Intelligence Deployments
Data management plays a vital role in edge deployments as it ensures processing efficiency, reduces bandwidth usage, and maintains data security and privacy. Here’s a look at the importance of data management in edge deployments and how edge devices handle tasks such as data storage, synchronization, and security.
Preprocessing data
Edge devices often receive noisy data from sensors or IoT devices. Techniques such as noise removal, data cleaning, and standardization help improve the quality of data analysis. These methods not only optimize bandwidth usage but also increase the efficiency of subsequent analysis.
Filtering Data
Edge devices can perform initial data filtering to extract information or detect events of interest. By doing this, you ensure that only valuable or important data is transferred to the cloud or local server. This helps reduce network traffic and minimize latency.
Aggregation Data
Employ aggregation techniques at the edge to compress data sets into compact representations. These aggregated representations provide a format that can be transmitted to the cloud for analysis or stored locally depending on bandwidth requirements.
Storing Data
Edge devices need to manage storage for temporary or offline operations because their storage capacity may be limited compared to cloud servers. Therefore, effective management of data storage becomes critical in edge scenarios.
Synchronizing data
Synchronizing data is critical in situations where edge devices have limited network connectivity or operate offline. Edge devices synchronize their data with cloud or local servers whenever they establish a connection.
Protect Data Security
Comprehensive security measures are critical for edge deployments to protect information. Edge devices employ encryption, access control, and security protocols to keep data secure during transmission and storage.
Protect Data Privacy
Data privacy in edge deployment scenarios is very important, especially when handling sensitive or personal information. Edge devices must comply with privacy regulations and implement methods such as data anonymization and differential privacy to protect individual identities and maintain data confidentiality.
Unleashing the Potential of Edge AI Deployments
Overall, deploying AI at the edge promises to drive innovation, increase efficiency, and enable real-time decision-making across industries. As research and technology advance in this field, it is expected that the application of artificial intelligence will revolutionize. This transformation can enable organizations to leverage their data while enabling privacy, security, and seamless integration with existing infrastructure.
The above is the detailed content of Enhance edge intelligence with AI deployment. For more information, please follow other related articles on the PHP Chinese website!
 Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AM
Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AMThis article explores the growing concern of "AI agency decay"—the gradual decline in our ability to think and decide independently. This is especially crucial for business leaders navigating the increasingly automated world while retainin
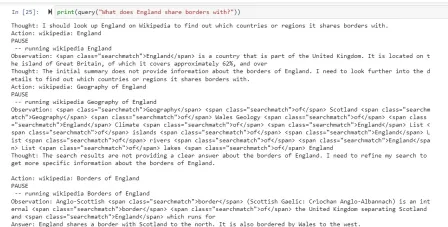 How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AM
How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AMEver wondered how AI agents like Siri and Alexa work? These intelligent systems are becoming more important in our daily lives. This article introduces the ReAct pattern, a method that enhances AI agents by combining reasoning an
 Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM
Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM"I think AI tools are changing the learning opportunities for college students. We believe in developing students in core courses, but more and more people also want to get a perspective of computational and statistical thinking," said University of Chicago President Paul Alivisatos in an interview with Deloitte Nitin Mittal at the Davos Forum in January. He believes that people will have to become creators and co-creators of AI, which means that learning and other aspects need to adapt to some major changes. Digital intelligence and critical thinking Professor Alexa Joubin of George Washington University described artificial intelligence as a “heuristic tool” in the humanities and explores how it changes
 Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AM
Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AMLangChain is a powerful toolkit for building sophisticated AI applications. Its agent architecture is particularly noteworthy, allowing developers to create intelligent systems capable of independent reasoning, decision-making, and action. This expl
 What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AM
What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AMRadial Basis Function Neural Networks (RBFNNs): A Comprehensive Guide Radial Basis Function Neural Networks (RBFNNs) are a powerful type of neural network architecture that leverages radial basis functions for activation. Their unique structure make
 The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AM
The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AMBrain-computer interfaces (BCIs) directly link the brain to external devices, translating brain impulses into actions without physical movement. This technology utilizes implanted sensors to capture brain signals, converting them into digital comman
 Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AM
Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AMThis "Leading with Data" episode features Ines Montani, co-founder and CEO of Explosion AI, and co-developer of spaCy and Prodigy. Ines offers expert insights into the evolution of these tools, Explosion's unique business model, and the tr
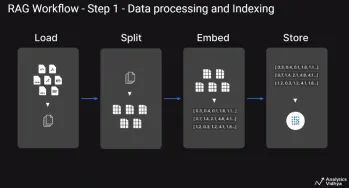 A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AM
A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AMThis article explores Retrieval Augmented Generation (RAG) systems and how AI agents can enhance their capabilities. Traditional RAG systems, while useful for leveraging custom enterprise data, suffer from limitations such as a lack of real-time dat


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

WebStorm Mac version
Useful JavaScript development tools

Atom editor mac version download
The most popular open source editor

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software






