Radial Basis Function Neural Networks (RBFNNs): A Comprehensive Guide
Radial Basis Function Neural Networks (RBFNNs) are a powerful type of neural network architecture that leverages radial basis functions for activation. Their unique structure makes them particularly well-suited for tasks such as pattern recognition, function approximation, and time series forecasting. Unlike traditional multi-layered neural networks with varied activation functions, RBFNNs offer distinct advantages in specific applications.

Key Concepts:
This guide covers the fundamentals of RBFNNs, including their components, the role of radial basis functions, training methodologies, and diverse applications.
Table of Contents:
- Understanding RBFNNs
- Network Architecture and Components
- The Role of Radial Basis Functions
- Training RBFNNs Efficiently
- Applications in Diverse Fields
- Frequently Asked Questions
RBFNN Architecture and Components:

RBFNNs typically comprise three layers:
- Input Layer: Receives the initial data and transmits it to the hidden layer.
- Hidden Layer (Radial Basis Functions): The core of the RBFNN. Each neuron employs a radial basis function (often a Gaussian function) to measure the distance between the input vector and the neuron's center. The output of each neuron reflects this distance, modified by the RBF.
- Output Layer: Combines the outputs from the hidden layer using weighted summation to produce the final network output.
Radial Basis Functions (RBFs):
RBFs are functions that calculate distances. The Gaussian function is a popular choice, defined as:

Where:
-
xrepresents the input vector. -
cdenotes the center of the RBF. -
σ(sigma) is the spread parameter, controlling the function's width.
The RBF quantifies the proximity of the input to the center c. Other RBF types exist (e.g., multi-quadratic, inverse multi-quadratic), but the Gaussian function is often preferred due to its smoothness and localized nature.
Training RBFNNs:
Training an RBFNN involves determining the RBF parameters (centers and spreads) and the output layer weights. This usually occurs in two phases:
- Center and Spread Determination: Methods like k-means clustering can be used to determine the RBF centers. Spreads are often derived from the distances between these centers.
- Weight Learning: With fixed centers and spreads, the output layer weights are learned using linear regression techniques. This two-stage approach contributes to the relatively fast training of RBFNNs compared to traditional backpropagation networks.
Applications of RBFNNs:
The ability of RBFNNs to approximate complex functions and handle non-linear data makes them applicable across various domains:
- Pattern Classification: Effective for image and speech recognition.
- Function Approximation: Useful for tasks like curve fitting and surface modeling.
- Time Series Prediction: Applicable to financial market forecasting and weather prediction.
Conclusion:
RBFNNs provide an efficient solution for tackling non-linear data and performing tasks such as pattern recognition, function approximation, and time series forecasting. Their unique architecture, combined with the use of radial basis functions, allows for accurate and efficient results in a wide range of machine learning applications. Understanding their structure, training methods, and applications is crucial for successful implementation.
Frequently Asked Questions:
Q1: What are the key components of an RBFNN?
A1: An RBFNN comprises an input layer, a hidden layer with radial basis functions, and an output layer.
Q2: What are the advantages of using RBFNNs?
A2: RBFNNs offer advantages such as their ability to handle non-linear data, fast training due to linear weight optimization, and their effectiveness in pattern recognition and function approximation.
Q3: How are the centers and spreads of RBFs determined?
A3: Centers are often determined using clustering techniques (like k-means), while spreads are typically calculated based on the distances between the centers.
Q4: How do Gaussian functions function within RBFNNs?
A4: Gaussian functions measure the distance between the input vector and the RBF center, transforming this distance into the output of the corresponding hidden layer neuron.
Q5: What are common applications of RBFNNs?
A5: RBFNNs find applications in function approximation, time-series prediction, and pattern classification due to their ability to handle non-linear data and approximate complex functions.
The above is the detailed content of What are the Radial Basis Functions Neural Networks?. For more information, please follow other related articles on the PHP Chinese website!
 Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AM
Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AMSince 2008, I've championed the shared-ride van—initially dubbed the "robotjitney," later the "vansit"—as the future of urban transportation. I foresee these vehicles as the 21st century's next-generation transit solution, surpas
 Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AM
Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AMRevolutionizing the Checkout Experience Sam's Club's innovative "Just Go" system builds on its existing AI-powered "Scan & Go" technology, allowing members to scan purchases via the Sam's Club app during their shopping trip.
 Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AM
Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AMNvidia's Enhanced Predictability and New Product Lineup at GTC 2025 Nvidia, a key player in AI infrastructure, is focusing on increased predictability for its clients. This involves consistent product delivery, meeting performance expectations, and
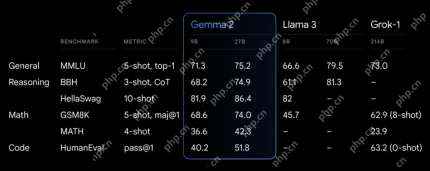 Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AM
Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AMGoogle's Gemma 2: A Powerful, Efficient Language Model Google's Gemma family of language models, celebrated for efficiency and performance, has expanded with the arrival of Gemma 2. This latest release comprises two models: a 27-billion parameter ver
 The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AM
The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AMThis Leading with Data episode features Dr. Kirk Borne, a leading data scientist, astrophysicist, and TEDx speaker. A renowned expert in big data, AI, and machine learning, Dr. Borne offers invaluable insights into the current state and future traje
 AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AM
AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AMThere were some very insightful perspectives in this speech—background information about engineering that showed us why artificial intelligence is so good at supporting people’s physical exercise. I will outline a core idea from each contributor’s perspective to demonstrate three design aspects that are an important part of our exploration of the application of artificial intelligence in sports. Edge devices and raw personal data This idea about artificial intelligence actually contains two components—one related to where we place large language models and the other is related to the differences between our human language and the language that our vital signs “express” when measured in real time. Alexander Amini knows a lot about running and tennis, but he still
 Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AM
Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AMCaterpillar's Chief Information Officer and Senior Vice President of IT, Jamie Engstrom, leads a global team of over 2,200 IT professionals across 28 countries. With 26 years at Caterpillar, including four and a half years in her current role, Engst
 New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AM
New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AMGoogle Photos' New Ultra HDR Tool: A Quick Guide Enhance your photos with Google Photos' new Ultra HDR tool, transforming standard images into vibrant, high-dynamic-range masterpieces. Ideal for social media, this tool boosts the impact of any photo,


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

Dreamweaver Mac version
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software





