 Technology peripherals
Technology peripherals AI
AI False positive issues in network attack detection based on deep learning
False positive issues in network attack detection based on deep learningFalse positive issues in network attack detection based on deep learning

The problem of false positives in network attack detection based on deep learning
With the increasing number and complexity of network attacks, traditional network security technology can no longer meet the requirements of combating various types of attacks. requirements for similar attacks. Therefore, network attack detection based on deep learning has become a research hotspot, and deep learning has great potential in improving network security. However, while deep learning models perform well in detecting cyberattacks, the issue of false positives has also become a concerning challenge.
The false positive problem means that the deep learning model incorrectly identifies normal network traffic as attack traffic. This kind of incorrect identification not only wastes the time and energy of network administrators, but also leads to the interruption of network services, causing losses to enterprises and users. Therefore, reducing the false alarm rate has become an important task to improve the availability of network attack detection systems.
In order to solve the problem of false positives, we can start from the following aspects.
First of all, for the problem of false positives, we need to understand how the deep learning model works. Deep learning models perform classification by learning large amounts of data and features. In network attack detection, the model learns the characteristics of attack traffic through a training data set, and then classifies unknown traffic based on these characteristics. The false positive problem usually occurs when the model mistakes normal traffic for attack traffic. Therefore, we need to analyze the performance of the model in classifying normal traffic and attack traffic to find out the reasons for false positives.
Secondly, we can use more data to improve the performance of the model. Deep learning models require large amounts of labeled data to train, covering a wide variety of attacks and normal traffic. However, due to the diversity and constant change of cyberattacks, the model may not accurately identify all attacks. At this point, we can expand the training set by adding more data so that the model can better adapt to new attacks. In addition, reinforcement learning methods can also be used to improve the performance of the model. Reinforcement learning can further reduce false positives by continuously interacting with the environment to learn optimal policies.
Again, we can use model fusion to reduce the false alarm rate. Common model fusion methods include voting and soft fusion. The voting method determines the final result through the voting of multiple models, which can reduce misjudgments by individual models. Soft fusion obtains the final result by weighting the output of multiple models, which can improve the overall discriminative ability. Through model fusion, we can make full use of the advantages of different models and reduce the false positive rate.
Finally, we can optimize the model to improve the performance of the model. For example, we can adjust the model's hyperparameters, such as learning rate, batch size, etc., to obtain better performance. In addition, regularization techniques can also be used to avoid overfitting of the model and improve its generalization ability. In addition, we can use transfer learning methods to apply models trained in other fields to network attack detection, thereby reducing the false alarm rate.
Reducing the false positive rate of deep learning-based network attack detection systems is a challenging task. By deeply understanding the characteristics of the model, increasing data sets, and adopting methods such as model fusion and model optimization, we can continuously improve the performance of the network attack detection system and reduce the occurrence of false positives.
The following is a deep learning code example on the false positive problem for network attack detection:
import tensorflow as tf
from tensorflow.keras import layers
# 定义深度学习模型
def create_model():
model = tf.keras.Sequential()
model.add(layers.Dense(64, activation='relu', input_dim=100))
model.add(layers.Dropout(0.5))
model.add(layers.Dense(64, activation='relu'))
model.add(layers.Dropout(0.5))
model.add(layers.Dense(1, activation='sigmoid'))
return model
# 加载数据集
(x_train, y_train), (x_test, y_test) = tf.keras.datasets.mnist.load_data()
x_train = x_train.reshape(60000, 784).astype('float32') / 255
x_test = x_test.reshape(10000, 784).astype('float32') / 255
# 构建模型
model = create_model()
model.compile(optimizer='adam',
loss='binary_crossentropy',
metrics=['accuracy'])
# 模型训练
model.fit(x_train, y_train, epochs=10, batch_size=64)
# 模型评估
loss, accuracy = model.evaluate(x_test, y_test)
print('Test loss:', loss)
print('Test accuracy:', accuracy)The above is a simple deep learning based network attack detection code example, through training and By evaluating the model, the performance of the model on network attack detection tasks can be obtained. In order to reduce false positives, optimization can be performed by increasing training samples, adjusting model parameters, and fusing multiple models. Specific optimization strategies need to be determined based on specific network attack detection tasks and data sets.
The above is the detailed content of False positive issues in network attack detection based on deep learning. For more information, please follow other related articles on the PHP Chinese website!
 Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AM
Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AMThis article explores the growing concern of "AI agency decay"—the gradual decline in our ability to think and decide independently. This is especially crucial for business leaders navigating the increasingly automated world while retainin
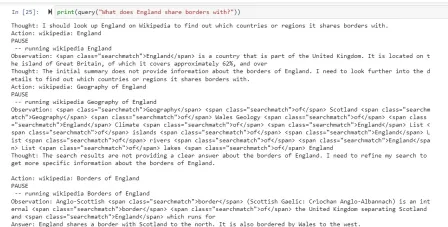 How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AM
How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AMEver wondered how AI agents like Siri and Alexa work? These intelligent systems are becoming more important in our daily lives. This article introduces the ReAct pattern, a method that enhances AI agents by combining reasoning an
 Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM
Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM"I think AI tools are changing the learning opportunities for college students. We believe in developing students in core courses, but more and more people also want to get a perspective of computational and statistical thinking," said University of Chicago President Paul Alivisatos in an interview with Deloitte Nitin Mittal at the Davos Forum in January. He believes that people will have to become creators and co-creators of AI, which means that learning and other aspects need to adapt to some major changes. Digital intelligence and critical thinking Professor Alexa Joubin of George Washington University described artificial intelligence as a “heuristic tool” in the humanities and explores how it changes
 Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AM
Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AMLangChain is a powerful toolkit for building sophisticated AI applications. Its agent architecture is particularly noteworthy, allowing developers to create intelligent systems capable of independent reasoning, decision-making, and action. This expl
 What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AM
What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AMRadial Basis Function Neural Networks (RBFNNs): A Comprehensive Guide Radial Basis Function Neural Networks (RBFNNs) are a powerful type of neural network architecture that leverages radial basis functions for activation. Their unique structure make
 The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AM
The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AMBrain-computer interfaces (BCIs) directly link the brain to external devices, translating brain impulses into actions without physical movement. This technology utilizes implanted sensors to capture brain signals, converting them into digital comman
 Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AM
Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AMThis "Leading with Data" episode features Ines Montani, co-founder and CEO of Explosion AI, and co-developer of spaCy and Prodigy. Ines offers expert insights into the evolution of these tools, Explosion's unique business model, and the tr
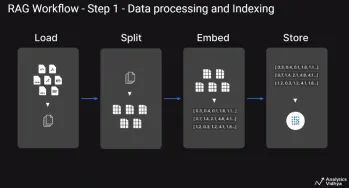 A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AM
A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AMThis article explores Retrieval Augmented Generation (RAG) systems and how AI agents can enhance their capabilities. Traditional RAG systems, while useful for leveraging custom enterprise data, suffer from limitations such as a lack of real-time dat


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

Dreamweaver Mac version
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

WebStorm Mac version
Useful JavaScript development tools




