 Technology peripherals
Technology peripherals AI
AI IDC report: Generative AI has entered an explosive period of industry exploration, and the technology supply side is in the early stages of commercialization
IDC report: Generative AI has entered an explosive period of industry exploration, and the technology supply side is in the early stages of commercialization
According to the introduction of IDC Consulting’s official public account, since the second half of 2023, more and more manufacturers have begun to update and upgrade generative artificial intelligence-related products and accelerate the integration of these products. Bringing it to the market
In order to deeply understand the needs, pain points and market status of China's generative AI users, IDC conducted a survey in order to "provide strong support for the future development of the industry. In order to maintain the original intention, the content needs to be Rewritten into Chinese. No original sentence required."
This site summarizes the IDC report as follows:
On the industry user side, generative AI has entered an exploratory period
- Industry users should avoid blind obedience. Strengthen management. Although there are currently obstacles such as brand and regulatory risks, data and intellectual property protection, budget and cost, the implementation timetable of the initially explored generative AI applications has not yet been clear, but the entire market continues to have a strong interest in generative AI technology. Introduce, express acceptance and recognition.
- Industry users should avoid potential risks. Enterprises can prioritize the establishment of evaluation and guidance methods for generative AI technology, as well as strengthen collaborative practices for application cases and data sharing, and introduce third parties to the application development process. Regulate potential ethical and legal risks arising from generative AI applications.
 ▲ Picture source IDC Consult the official public account
▲ Picture source IDC Consult the official public account
 ▲ Picture source IDC Consult the official public account
▲ Picture source IDC Consult the official public account
On the technology supplier side, generative AI has entered the early stage of commercialization
- Technology supply for different roles Businesses should avoid technology anxiety and pay attention to product upgrades.
- AI infrastructure vendors should provide extensive development support and complete AI stack (including libraries, SDKs, orchestration, AI tools), in addition to supporting data across hybrid/multi-cloud architectures Storage integration.
- AI software suppliers should provide AI products with data security and support for multi-modal content (such as text, audio, video, etc.); in addition, they should also consider providing industry-customized models and solutions Program, data management and other functions.
 ▲ Picture source IDC Consult the official public account
▲ Picture source IDC Consult the official public account
 ▲ Picture source IDC Consult the official public account
▲ Picture source IDC Consult the official public account
#In order to keep the original meaning unchanged, the content needs to be rewritten into Chinese. There is no need to appear the original sentence
requiredThe above is the detailed content of IDC report: Generative AI has entered an explosive period of industry exploration, and the technology supply side is in the early stages of commercialization. For more information, please follow other related articles on the PHP Chinese website!
 Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AM
Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AMThis article explores the growing concern of "AI agency decay"—the gradual decline in our ability to think and decide independently. This is especially crucial for business leaders navigating the increasingly automated world while retainin
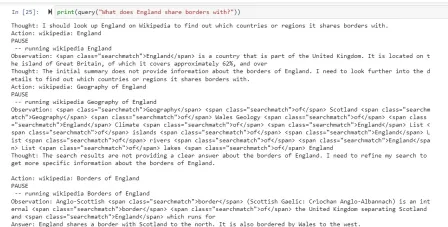 How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AM
How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AMEver wondered how AI agents like Siri and Alexa work? These intelligent systems are becoming more important in our daily lives. This article introduces the ReAct pattern, a method that enhances AI agents by combining reasoning an
 Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM
Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM"I think AI tools are changing the learning opportunities for college students. We believe in developing students in core courses, but more and more people also want to get a perspective of computational and statistical thinking," said University of Chicago President Paul Alivisatos in an interview with Deloitte Nitin Mittal at the Davos Forum in January. He believes that people will have to become creators and co-creators of AI, which means that learning and other aspects need to adapt to some major changes. Digital intelligence and critical thinking Professor Alexa Joubin of George Washington University described artificial intelligence as a “heuristic tool” in the humanities and explores how it changes
 Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AM
Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AMLangChain is a powerful toolkit for building sophisticated AI applications. Its agent architecture is particularly noteworthy, allowing developers to create intelligent systems capable of independent reasoning, decision-making, and action. This expl
 What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AM
What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AMRadial Basis Function Neural Networks (RBFNNs): A Comprehensive Guide Radial Basis Function Neural Networks (RBFNNs) are a powerful type of neural network architecture that leverages radial basis functions for activation. Their unique structure make
 The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AM
The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AMBrain-computer interfaces (BCIs) directly link the brain to external devices, translating brain impulses into actions without physical movement. This technology utilizes implanted sensors to capture brain signals, converting them into digital comman
 Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AM
Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AMThis "Leading with Data" episode features Ines Montani, co-founder and CEO of Explosion AI, and co-developer of spaCy and Prodigy. Ines offers expert insights into the evolution of these tools, Explosion's unique business model, and the tr
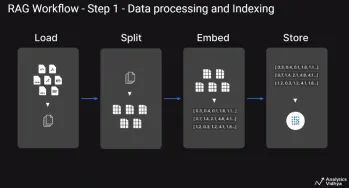 A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AM
A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AMThis article explores Retrieval Augmented Generation (RAG) systems and how AI agents can enhance their capabilities. Traditional RAG systems, while useful for leveraging custom enterprise data, suffer from limitations such as a lack of real-time dat


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

WebStorm Mac version
Useful JavaScript development tools

Atom editor mac version download
The most popular open source editor

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software





