Home >Common Problem >What is SSH? For a detailed explanation of the principle, just read this article!
What is SSH? For a detailed explanation of the principle, just read this article!
- Linux中文社区forward
- 2023-08-02 17:51:431298browse

Directory
What is the SSH port number?How does SSH work?
Using PuTTY and OpenSSHSSH keys
What is the SSH port number?
When SSH is applied to STelnet, SFTP and SCP, the default SSH port used is 22. When SSH is applied to NETCONF, you can specify the SSH port to be 22 or 830. The SSH port supports modification. After the change, all current connections will be disconnected and the SSH server will start listening to the new port.
How does SSH work?
SSH consists of a server and a client. During the entire communication process, in order to establish a secure SSH channel, it will go through the following stages:
Connection establishment
The SSH server listens for the client's connection request on the specified port. After the client initiates a connection request to the server, the two parties establish a TCP connection.
Version Negotiation
The SSH protocol currently exists in SSH1.X (the version before SSH2.0) and SSH2.0. Compared with the SSH1.X protocol, the SSH2.0 protocol has been expanded in structure and can support more authentication methods and key exchange methods, while improving service capabilities. The SSH server and client determine the final SSH version number used through negotiation.
Algorithm negotiation
SSH supports multiple encryption algorithms. Based on the algorithms supported by each party, both parties negotiate the key exchange algorithm that is ultimately used to generate the session key and the data information. Encrypted encryption algorithms, public key algorithms for digital signatures and authentication, and HMAC algorithms for data integrity protection.






Awesome! N open source projects that are essential for taking on private work!
Key exchange
The server and client use the key exchange algorithm to dynamically generate shared session keys and session IDs to establish encrypted channels. The session key is mainly used for encryption of subsequent data transmission, and the session ID is used to identify the SSH connection during the authentication process.
User Authentication
The SSH client initiates an authentication request to the server, and the server authenticates the client. SSH supports the following authentication methods:
Password authentication: The client authenticates through username and password, sends the encrypted username and password to the server, and the server decrypts it It is then compared with the locally saved username and password, and an authentication success or failure message is returned to the client. Key (publickey) authentication: The client authenticates with the server through user name, public key, public key algorithm and other information. password-publickey authentication: means that users need to meet both password authentication and key authentication before they can log in. all authentication: As long as one of password authentication and key authentication is met.
Session request
After the authentication is passed, the SSH client sends a session request to the server, requesting the server to provide a certain type of service, that is, Requests to establish a corresponding session with the server. In addition, when searching for the public account Linux, this is how you should learn to reply "Linux" in the background to get a surprise gift package.
Session interaction
After the session is established, the SSH server and client exchange data information on the session.
Using PuTTY and OpenSSH
PuTTY is a classic free SSH connection tool on Windows. It is usually used to remotely log in to the device using the SSH protocol. The latest version can be downloaded from the PuTTY official website .
OpenSSH is an open source implementation of the SSH protocol and supports running on Unix operating systems. The latest version can be downloaded from the OpenSSH official website. Currently, Windows 10 already includes OpenSSH client and server software, which can be searched and installed in "Settings—Applications—Applications and Features—Optional Features".
SSH key
Symmetric encryption and asymmetric encryption
The basic way to improve security is encryption, encryption algorithm Convert plaintext to ciphertext via key for secure transmission. SSH uses a combination of symmetric encryption and asymmetric encryption algorithms during its working process to ensure the security of information transmission through pre-generated SSH keys. The encryption and decryption processes of the two encryption algorithms are shown in the figure below.
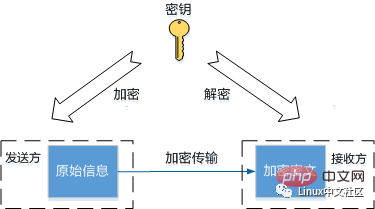
Symmetric encryption algorithm
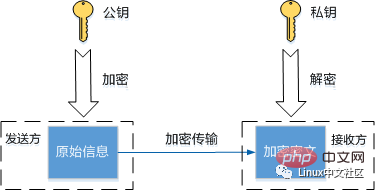
Key Authentication
The two most basic methods of SSH user authentication are password authentication and key authentication. Password authentication is to send your username and password to the server for authentication. This method is relatively simple, and you need to enter your username and password every time you log in. Key authentication uses a public key and private key pair for identity verification to achieve secure password-free login. It is a widely used and recommended login method. The basic principle of key authentication is that the server uses the client's public key to encrypt random content, and the client uses its own private key to decrypt and send it to the server to verify its identity. The specific process is shown in the figure below.
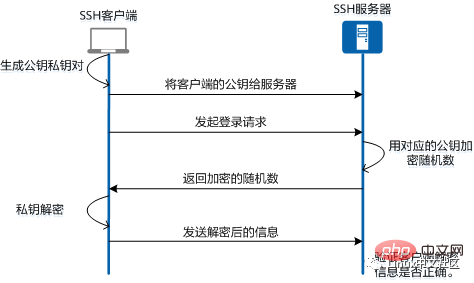
SSH key authentication login process
Before making an SSH connection, the SSH client The client needs to generate its own public key and private key pair first, and store its own public key on the SSH server. The SSH client sends a login request, and the SSH server will locally search for the client's public key based on the user name and other information in the request, and use this public key to encrypt a random number and send it to the client. end. The client uses its own private key to decrypt the returned information and sends it to the server. The server verifies whether the information decrypted by the client is correct. If correct, the authentication is passed.
The above is the detailed content of What is SSH? For a detailed explanation of the principle, just read this article!. For more information, please follow other related articles on the PHP Chinese website!

