 Technology peripherals
Technology peripherals AI
AI Meticulous quantum computing could pose security risks that are even greater than artificial intelligence.
Meticulous quantum computing could pose security risks that are even greater than artificial intelligence.Meticulous quantum computing could pose security risks that are even greater than artificial intelligence.
In recent years, controversy surrounding the risks of artificial intelligence has been widespread. Tesla CEO Elon Musk once publicly warned that computer systems may possess human intelligence as early as 2029. If the government does not regulate and intervene in it, this technology may become mankind's "biggest existential threat." In fact, regardless of whether artificial intelligence technology can truly acquire autonomous thinking capabilities similar to those of humans, the negative effects of its application have already emerged: it has been widely used to illegally monitor public spaces, monitor social media, conduct deep fakes, and create lethal weapons. All have affected and harmed people's lives.
When mankind cannot effectively respond to the crisis of artificial intelligence, similar mistakes should not be allowed to happen again! But some researchers say there is a more powerful emerging technology that could cause even more serious damage - quantum computing. There is no doubt that quantum computing technology can bring benefits, but just like two sides of a coin, humans still do not know enough about the destructive effects it will cause. Quantum computing can be used for good as well as for evil. Even when used in good faith, potential security risks must be considered.
Quantum computing operates on a completely different basis than current semiconductor-based computing technology. With their ability to process large amounts of data quickly, quantum computers can easily crack private records, private communications and passwords on any computing device in the world. Especially once quantum computing is combined with artificial intelligence technology, this destructiveness will increase exponentially, and then the catastrophic consequences that Musk warned will most likely occur.
Although it is still in the initial stage of application, the whole society urgently needs to understand all possible security impacts of this technology before its large-scale application, and respond in advance. We must not repeat the past mistakes that were detrimental to the management and control of artificial intelligence technology. Recently, security experts from the Forbes Technology Committee discussed the risks that human society may face in the application of quantum computing.
Risk 1. Modern encryption methods will be ineffective
Today’s cryptography is to encode data in large number combinations, using regular It is impossible for computing technology to crack these passwords in a reasonable amount of time. But quantum computers may use quantum mechanics principles, such as superposition, entanglement and uncertainty, to crack encryption instantly through brute force. Any modern password or key can be compromised by a brute force attack and rendered useless, and the industry currently has no idea how to combat this problem.
Risk 2. Internet infrastructure will be disrupted
Since quantum computers can quickly crack current encryption keys, all existing Internet information transmission is at risk, and attackers can use quantum computers to intercept various data information transmitted on the network. When information transmission is no longer secure, the existing Internet infrastructure will be subverted.
Risk 3. DNN models are more difficult to evaluate
If quantum computing is used for machine learning to form enhanced quantum machine learning, it may It will bring about the ultimate security black box problem. It is well known that deep neural network (DNN) models are not transparent. Although there are tools to monitor how the algorithm layers in DNN are working, once quantum machine learning is implemented, it will become more difficult to evaluate the DNN and judge the decision-making process, which may cause the machine learning process and results to lose control.
Risk 4. Now encrypted data will be decrypted in advance
A new threat called "collect first, decrypt later" is This refers to an attacker's attempt to steal encrypted data and potentially hold the data for years so that it can be decrypted using future quantum computing technology. Because even years later, much of the encrypted content may still be valuable to attackers.
Risk 5. The cost of enterprise digitalization will further increase
The cost of quantum computing is a potential risk. In a recession, environmental, social and governance issues are top of mind for most organizations, and starting and maintaining quantum computing projects is expensive. Quantum computing power will be expensive for a long time to come, but organizations should carefully consider their reasons for adopting quantum technology before investing too much in the technology.
Risk 6. The digital divide is sharply widening
A huge social risk of quantum computing is the sharp widening of the digital divide. The high cost of quantum computing means that only institutions and organizations with financial capabilities can enjoy powerful computing power, which may be used to further widen the gap between rich and poor and undermine social equality. As quantum computing takes off, one risk companies may face is that competitors will use the technology to outdo themselves, as quantum computers will be able to solve problems that traditional computers cannot. This could lead to a kind of "arms race" in which companies are forced to Upgrade your system or face crisis.
Risk 7. Damage to ecological resources
The stable operation of quantum computing relies on helium cooling to keep particles static. However, helium is a very scarce resource, and both quantity and price in its supply chain are at risk. First, organizations must ensure that they have enough access to helium to maintain the operation of quantum computing equipment; second, due to the temptation of huge commercial interests, there is a risk that quantum computing resources will be monopolized and concentrated in a few privileged operators.
Risk 8. Blockchain technology will be cracked
The rise of quantum computing may bring new challenges to the emerging blockchain and cryptocurrency economy bring risks. Blockchain relies on asymmetric key encryption algorithms (RSA and EC). These algorithms can also be broken through quantum computing, leading to malicious manipulation of the blockchain. This is a significant risk for companies and consumers investing in blockchain technology.
Risk 9. Risk of amplifying existing security vulnerabilities
Quantum computing is expected to disrupt technology as we know it today due to its powerful computing power . The biggest risk is that quantum computing will bring unforeseen risks to today's computing systems, as attackers can use the new computing power to find previously undiscovered security holes. This will pose challenges to existing vulnerability management programs.
Risk 10. Increase the risk of military confrontation between countries
While quantum computing promises to solve extremely complex problems in today’s society, it can also Used maliciously by national governments in war. If some countries' militaries have access to quantum computing but another's cannot, this information asymmetry could put the latter at a disadvantage in a war. Once the balance of military power between countries is broken, the risk of global military conflict will increase.
The above is the detailed content of Meticulous quantum computing could pose security risks that are even greater than artificial intelligence.. For more information, please follow other related articles on the PHP Chinese website!
 Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AM
Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AMThis article explores the growing concern of "AI agency decay"—the gradual decline in our ability to think and decide independently. This is especially crucial for business leaders navigating the increasingly automated world while retainin
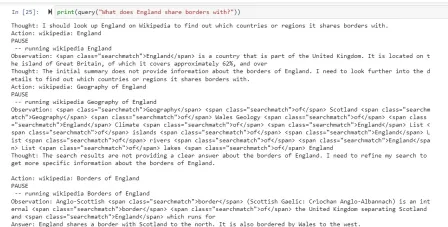 How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AM
How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AMEver wondered how AI agents like Siri and Alexa work? These intelligent systems are becoming more important in our daily lives. This article introduces the ReAct pattern, a method that enhances AI agents by combining reasoning an
 Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM
Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM"I think AI tools are changing the learning opportunities for college students. We believe in developing students in core courses, but more and more people also want to get a perspective of computational and statistical thinking," said University of Chicago President Paul Alivisatos in an interview with Deloitte Nitin Mittal at the Davos Forum in January. He believes that people will have to become creators and co-creators of AI, which means that learning and other aspects need to adapt to some major changes. Digital intelligence and critical thinking Professor Alexa Joubin of George Washington University described artificial intelligence as a “heuristic tool” in the humanities and explores how it changes
 Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AM
Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AMLangChain is a powerful toolkit for building sophisticated AI applications. Its agent architecture is particularly noteworthy, allowing developers to create intelligent systems capable of independent reasoning, decision-making, and action. This expl
 What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AM
What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AMRadial Basis Function Neural Networks (RBFNNs): A Comprehensive Guide Radial Basis Function Neural Networks (RBFNNs) are a powerful type of neural network architecture that leverages radial basis functions for activation. Their unique structure make
 The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AM
The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AMBrain-computer interfaces (BCIs) directly link the brain to external devices, translating brain impulses into actions without physical movement. This technology utilizes implanted sensors to capture brain signals, converting them into digital comman
 Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AM
Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AMThis "Leading with Data" episode features Ines Montani, co-founder and CEO of Explosion AI, and co-developer of spaCy and Prodigy. Ines offers expert insights into the evolution of these tools, Explosion's unique business model, and the tr
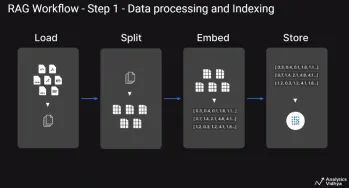 A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AM
A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AMThis article explores Retrieval Augmented Generation (RAG) systems and how AI agents can enhance their capabilities. Traditional RAG systems, while useful for leveraging custom enterprise data, suffer from limitations such as a lack of real-time dat


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

Dreamweaver Mac version
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

WebStorm Mac version
Useful JavaScript development tools





