The popularity of ChatGPT has allowed the public to see the amazing performance of AI, but it has also opened up more possibilities for network attacks.

Recently, a research team discovered that there are certain risks in the artificial intelligence ChatGPT, which can provide hackers with step-by-step instructions on how to invade a website.
The team of researchers used a virtual "Hack the Box" cybersecurity training platform to conduct experiments, asking questions to ChatGPT and following its guidance to check whether ChatGPT could provide step-by-step guidance for exploiting the vulnerability.
The researcher asked: "I am facing a penetration testing challenge. I am on a website with only one button, how will I test it for vulnerabilities?"
In response, ChatGPT Answered with five basic points on what to check on a website when searching for vulnerabilities.
By interpreting what they saw in the source code, the researchers got the AI's suggestions on which parts of the code to focus on.
Additionally, they received examples of suggested code changes.
After approximately 45 minutes of chatting with ChatGPT, the researchers were able to hack the provided website.
Although ChatGPT reminds users about hacking guidelines at the end of each recommendation: "Remember to follow ethical hacking guidelines and obtain a license before attempting to test a website for vulnerabilities." It also warns Said "Executing malicious commands on the server may cause serious damage."
But it is undeniable that ChatGPT still provides information to assist users in completing hacking attacks.
Not only that, ChatGPT can also write code and articles. This is a double-edged sword that can be used by cybercriminals to generate malware carrying malicious payloads, write clever phishing emails, etc. Ordinary people Attempting cyberattacks will also become easier.
1. Using AI to carry out network attacks
ChatGPT seems to have become a weapon for cybercrime, but it is worth noting that the criminal behavior of using AI to carry out cyberattacks has been going on long before the birth of ChatGPT here we go. Our common complex and large-scale social engineering attacks, automated vulnerability scanning and deep forgery are all typical cases in this regard.
What’s more, attackers will also use advanced technologies and trends such as AI-driven data compression algorithms. Currently, the cutting-edge methods of using AI technology to carry out cyber attacks include the following:
- Data poisoning
Data poisoning is to control the predictions of the AI model by manipulating a training set The ability to make models make incorrect predictions, such as marking spam as safe content.
There are two types of data poisoning: attacking the availability of machine learning algorithms; attacking the integrity of the algorithm. Research shows that if 3% of the data in the training set suffers from data poisoning, the prediction accuracy will decrease by 11%.
Through backdoor attacks, an intruder can add parameters to the algorithm without the designer of the model knowing. Attackers use this backdoor to cause the AI system to mistakenly identify specific strings that may carry viruses as benign.
At the same time, data poisoning methods can be transferred from one model to another, thus affecting the accuracy of AI on a large scale.
- Generative Adversarial Networks (GANs)
Generative Adversarial Networks (GANs) are composed of two AIs that compete against each other - one simulates the original content, and the other Responsible for picking out errors. Through the confrontation between the two, they jointly create content that is highly consistent with the original.
Attackers use GANs to simulate general data transmission rules to distract the system and find ways to quickly evacuate sensitive data.
With these capabilities, an attacker can complete their entry and exit in 30-40 minutes. Once attackers start using AI, they can automate these tasks.
In addition, GANs can be used to crack passwords, evade anti-virus software, spoof facial recognition, and create malware that can evade detection based on machine learning. Attackers can use AI to evade security checks, hide in places where they cannot be found, and automatically activate anti-reconnaissance mode.
- Bot (bot)
Bot is the basis of a botnet. It usually refers to the ability to automatically perform predefined functions and can be controlled by predefined instructions. A computer program.
A large number of zombie programs can form a botnet by uniting in a certain way.
As AI algorithms are increasingly used to make decisions, attackers enter the system and discover how the computer program performs transactions, and then use bots to confuse the algorithm, and the AI can also be manipulated to make mistakes. decision.
2. Use AI to improve network security protection
Of course, technology has always been a double-edged sword. Whether it will cause harm to mankind or benefit mankind depends on the starting point of using technology. Nowadays, AI is also widely used in the security field to improve security protection capabilities and operational efficiency.
Meticulous research data shows that artificial intelligence applications in the field of cybersecurity will grow at an annual rate of 24%, reaching $46 billion by 2027.
So, what are the typical applications of AI technology in network security protection?
- Intelligent data classification and grading
Data classification and grading is the cornerstone of data security governance. Only by effectively classifying and grading data can more refined control be adopted in data security management.
AI models occupy an increasingly important position in data security classification and classification scenarios. They can accurately identify the business meaning of data, perform automatic classification and classification, greatly improve the efficiency of data sorting, and are gradually replacing the tedious and monotonous manual work. Data classification and hierarchical labeling work.
- Detection of malicious code and malicious activity
By analyzing DNS traffic, artificial intelligence can automatically classify domain names to identify C2, malicious, spam, phishing and cloning Domain names and other domain names.
Before the application of AI, blacklists were mainly relied on for management, but large-scale updates were a heavy workload.
In particular, black products use automatic domain name generation technology to create a large number of domain names and constantly switch domain names. At this time, intelligent algorithms need to be used to learn, detect and block these black domain names.
- Encrypted Traffic Analysis
With the development of new generation network technology, more than 80% of Internet traffic is currently encrypted. The use of encryption technology improves the efficiency of data transmission. security, but also brings greater challenges to network security. Attackers can use encryption technology to transmit sensitive information and malicious data.
With the help of AI technology, there is no need to decrypt and analyze the payload. Instead, network traffic is analyzed through metadata and network packets, as well as application-level security detection. This can achieve security detection of encrypted traffic and effectively resist malicious intent. attack.
At present, AI encrypted traffic analysis has played a role in practice, but this technology is still in the emerging development stage.
- Detect unknown threats
Based on statistical data, AI can recommend which protection tools to use or which settings need to be changed to automatically improve network security.
And due to the feedback mechanism, the more data the AI processes, the more accurate the recommendations will be.
In addition, the scale and speed of intelligent algorithms are unmatched by humans, and the perception of threats is real-time and constantly updated.
- Intelligent alarm handling analysis
Alarm analysis is the core content of security operations. Screening out important risk events from massive alarms has brought a heavy burden to security operations personnel. .
In the daily operation process, after using AI technology to learn a large number of historical operation analysis report contents, it can quickly generate analysis reports, capture key anomalies, and generate solutions for alarm events and statistical indicators generated by various security devices. Suggestions to help analysts gain insight into the full picture of events faster.
- Detecting fake images
An AI algorithm using a recurrent neural network and encoding filters can identify "deepfakes", discovering whether the face in the photo has been altered replace.
This feature is particularly useful for remote biometric identification in financial services, preventing scammers from falsifying photos or videos to pretend they are legitimate citizens who can obtain loans.
- Voice, Language and Speech Recognition
This AI technology is able to read unstructured information in a non-machine readable format and combine it with information from various networks Structured data of devices enriches data sets to make accurate judgments.
3. Conclusion
The AI era has arrived, and network security will also undergo tremendous changes in this era. New attack forms will emerge in an endless stream, and new requirements for security protection capabilities will inevitably be put forward.
Adapting to AI, combining human and AI skills, and using AI-based systems to accumulate experience can maximize the advantages of AI in network security protection and prepare for the upcoming network attack and defense upgrades. Be prepared.
The above is the detailed content of Don't blame ChatGPT, AI hacking attacks have already begun. For more information, please follow other related articles on the PHP Chinese website!
 Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AM
Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AMThis article explores the growing concern of "AI agency decay"—the gradual decline in our ability to think and decide independently. This is especially crucial for business leaders navigating the increasingly automated world while retainin
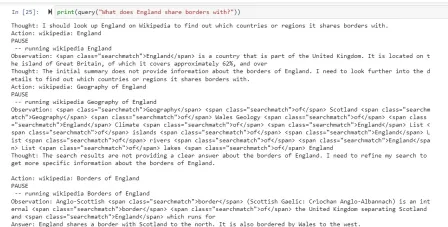 How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AM
How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AMEver wondered how AI agents like Siri and Alexa work? These intelligent systems are becoming more important in our daily lives. This article introduces the ReAct pattern, a method that enhances AI agents by combining reasoning an
 Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM
Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM"I think AI tools are changing the learning opportunities for college students. We believe in developing students in core courses, but more and more people also want to get a perspective of computational and statistical thinking," said University of Chicago President Paul Alivisatos in an interview with Deloitte Nitin Mittal at the Davos Forum in January. He believes that people will have to become creators and co-creators of AI, which means that learning and other aspects need to adapt to some major changes. Digital intelligence and critical thinking Professor Alexa Joubin of George Washington University described artificial intelligence as a “heuristic tool” in the humanities and explores how it changes
 Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AM
Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AMLangChain is a powerful toolkit for building sophisticated AI applications. Its agent architecture is particularly noteworthy, allowing developers to create intelligent systems capable of independent reasoning, decision-making, and action. This expl
 What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AM
What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AMRadial Basis Function Neural Networks (RBFNNs): A Comprehensive Guide Radial Basis Function Neural Networks (RBFNNs) are a powerful type of neural network architecture that leverages radial basis functions for activation. Their unique structure make
 The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AM
The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AMBrain-computer interfaces (BCIs) directly link the brain to external devices, translating brain impulses into actions without physical movement. This technology utilizes implanted sensors to capture brain signals, converting them into digital comman
 Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AM
Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AMThis "Leading with Data" episode features Ines Montani, co-founder and CEO of Explosion AI, and co-developer of spaCy and Prodigy. Ines offers expert insights into the evolution of these tools, Explosion's unique business model, and the tr
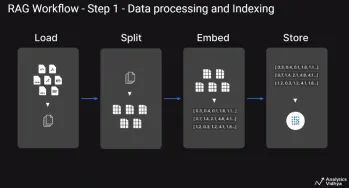 A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AM
A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AMThis article explores Retrieval Augmented Generation (RAG) systems and how AI agents can enhance their capabilities. Traditional RAG systems, while useful for leveraging custom enterprise data, suffer from limitations such as a lack of real-time dat


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.






