
In part because hybrid and remote workplaces are the new normal for most businesses, the sophistication of cyberattacks and the risks they pose have grown rapidly over the past few years . In fact, these new ways of working open up a whole new set of phishing methods for threat actors.
It is estimated that global cybercrime is expected to grow at an annual rate of 15% over the next five years, causing losses of approximately US$10.5 billion by 2025.
The cyberspace is huge. Although hundreds of IT experts analyze threats every day, this is a difficult task. Because humans have limited ability to respond to emerging threats, new, faster and more effective technologies are needed. Artificial intelligence is a potential solution. In this article, I’ll review some common attack methods and how AI solutions can combat cyberattacks.
Domain Name Similarity
Cybercriminals have registered thousands of similar domain names, disguising themselves as well-known brands or trustworthy individuals, tricking victims into submitting sensitive certificates or conducting financial transactions. In this case, the hacker registered a domain name similar to the target company. They change URL names and create fake websites and email addresses by adding characters or replacing single letters. For example, "1" means "l" and "0" means "o". They can also use a series of letters, such as "vv" means "w" and "rn" means "m".
Spelling errors are another common tactic to trick the eye. Imagine if someone registered "gooogle.com" instead of "google.com" or "yahooo.com" instead of "yahoo.com".
Protecting businesses against lookalike domain attacks can be difficult, automation, machine learning and artificial intelligence, brand protection solutions have evolved to:
- Custom algorithms sift through data sets, and Identify suspicious activity and malicious domains impersonating real companies.
- The editor uses distance and image-based technology to pinpoint similar areas of real companies.
- Monitoring tools to detect web attackers scraping content from legitimate websites.
- Automatically trigger to quickly address threats before major damage occurs.
Impersonation and deception
Impersonation refers to cybercriminals using fake display names to impersonate legitimate businesses or individuals. Most email providers allow users to edit their display name, making it easy for hackers to trick victims into believing the email is legitimate. Impersonation spoofing is harder to detect when emails are read on a mobile phone.
Cybercriminals use impersonation to conduct crimes such as account takeovers, whaling, and CEO fraud. A successful name spoofing attack can result in financial losses, reputational damage, and compromised security.
Artificial intelligence solutions can combine predictive threat intelligence, machine learning, and advanced content analytics to detect impersonation attacks. The machine creates a baseline for regular email traffic, and any email that deviates from that baseline is considered unusual and malicious.
URL Detection
URL phishing is a growing threat in which cyber actors create a legitimate-looking website to trick victims into submitting sensitive login credentials. The 2021 Cybersecurity Threat Report stated that about 86% of companies have at least one employee who clicked on a phishing link.
Different methods based on deep learning and machine learning are introduced to protect against URL phishing. One of the ways artificial intelligence can detect URL phishing attacks is to use deep neural networks to discover unusual patterns in URLs. In this way, AI generates alerts that draw attention to suspicious URLs and stop cybercriminals in their tracks.
Artificial Intelligence in Cybersecurity
To combat these cyber threats, artificial intelligence solutions can leverage machine learning and recurrent neural networks. When a pattern of data typical of a phishing website is detected, the interconnected neurons fire together. Collect benign URLs and phishing URLs to create a dataset and identify content-based features. Combined with supervised machine learning, determine the probability that a website is legitimate or malicious.
All businesses are at risk of being attacked by cyber actors. Lookalike, name spoofing and phishing attacks can target any industry, including public administration, healthcare, pharmaceuticals, insurance, research and retail.
When it comes to lookalikes and name spoofing, AI solutions constantly examine domain names and names of organizations that appear to be logged in to uncover hidden patterns that indicate the company may be under spoofing attacks.
Taking phishing URL detection as an example, the algorithm can be trained on millions of phishing samples. Therefore, it detects phishing URLs based on thousands of features extracted from a single URL in a high-dimensional space.
It is difficult for humans to imagine four- or five-dimensional space, because to the human eye, the world is three-dimensional, but artificial intelligence can observe a one-dimensional space and draw conclusions based on it.
Despite these benefits, implementing functional AI solutions with high accuracy remains a challenge for most enterprises. To do this, businesses should consider these best practices.
1.AI models must be trained on real-world data in production. Businesses should start data collection long before developing AI solutions.
2. Enterprises should monitor how the characteristics of the data change over time. Pandemics or climate change may be changes worth tracking.
3. Enterprises should develop and use explainable artificial intelligence technology. Only explainable AI can not only spot phishing attacks but also reason about the origin of decisions.
The field of cyberattacks is getting bigger and bigger, and it’s still growing. Analyzing enterprise threats involves more than just human intervention. Enterprises need emerging technologies to support security teams.
Artificial intelligence is still new in the cybersecurity world, but its ability to learn new things, make informed decisions, and improve models is unparalleled because it can analyze large amounts of information and provide the information security professionals need data to enhance security and protect against cyberattacks.
The above is the detailed content of How AI solutions can protect against cyberattacks. For more information, please follow other related articles on the PHP Chinese website!
 Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AM
Are You At Risk Of AI Agency Decay? Take The Test To Find OutApr 21, 2025 am 11:31 AMThis article explores the growing concern of "AI agency decay"—the gradual decline in our ability to think and decide independently. This is especially crucial for business leaders navigating the increasingly automated world while retainin
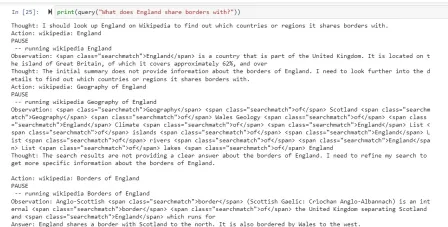 How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AM
How to Build an AI Agent from Scratch? - Analytics VidhyaApr 21, 2025 am 11:30 AMEver wondered how AI agents like Siri and Alexa work? These intelligent systems are becoming more important in our daily lives. This article introduces the ReAct pattern, a method that enhances AI agents by combining reasoning an
 Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM
Revisiting The Humanities In The Age Of AIApr 21, 2025 am 11:28 AM"I think AI tools are changing the learning opportunities for college students. We believe in developing students in core courses, but more and more people also want to get a perspective of computational and statistical thinking," said University of Chicago President Paul Alivisatos in an interview with Deloitte Nitin Mittal at the Davos Forum in January. He believes that people will have to become creators and co-creators of AI, which means that learning and other aspects need to adapt to some major changes. Digital intelligence and critical thinking Professor Alexa Joubin of George Washington University described artificial intelligence as a “heuristic tool” in the humanities and explores how it changes
 Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AM
Understanding LangChain Agent FrameworkApr 21, 2025 am 11:25 AMLangChain is a powerful toolkit for building sophisticated AI applications. Its agent architecture is particularly noteworthy, allowing developers to create intelligent systems capable of independent reasoning, decision-making, and action. This expl
 What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AM
What are the Radial Basis Functions Neural Networks?Apr 21, 2025 am 11:13 AMRadial Basis Function Neural Networks (RBFNNs): A Comprehensive Guide Radial Basis Function Neural Networks (RBFNNs) are a powerful type of neural network architecture that leverages radial basis functions for activation. Their unique structure make
 The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AM
The Meshing Of Minds And Machines Has ArrivedApr 21, 2025 am 11:11 AMBrain-computer interfaces (BCIs) directly link the brain to external devices, translating brain impulses into actions without physical movement. This technology utilizes implanted sensors to capture brain signals, converting them into digital comman
 Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AM
Insights on spaCy, Prodigy and Generative AI from Ines MontaniApr 21, 2025 am 11:01 AMThis "Leading with Data" episode features Ines Montani, co-founder and CEO of Explosion AI, and co-developer of spaCy and Prodigy. Ines offers expert insights into the evolution of these tools, Explosion's unique business model, and the tr
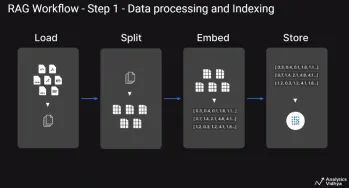 A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AM
A Guide to Building Agentic RAG Systems with LangGraphApr 21, 2025 am 11:00 AMThis article explores Retrieval Augmented Generation (RAG) systems and how AI agents can enhance their capabilities. Traditional RAG systems, while useful for leveraging custom enterprise data, suffer from limitations such as a lack of real-time dat


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

Dreamweaver Mac version
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

WebStorm Mac version
Useful JavaScript development tools






