Artificial intelligence (AI) has the potential to change the nature of society. Although artificial intelligence tools bring us a lot of expectations, we also need to be vigilant in many aspects. For example, cybercriminals and other threat actors are weaponizing artificial intelligence, and even AI image generators are not immune to abuse.
What is an AI image generator? How do they work? If you've ever used an AI image generator, it's pretty clear what they are all about. Even if you've never used one, you've likely encountered AI-generated images on social media and elsewhere. Today's popular software works very simply: the user enters text, and artificial intelligence generates an image based on that text.

In recent years, with the development of artificial intelligence technology, most text-to-image generators adopt diffusion models, which means that they accept Long hours of "training", which is the main reason why their work is so impressive and stunningly realistic.
What makes these AI tools even more impressive is that they not only modify existing images or merge thousands of images into one, but also create new original images from scratch. The more people use these text-to-image generators, the more information they get and the better their creations become.
There are already many famous AI image generators: WOMBO, DALL-E, Stable Diffusion, Midjourney, DeepAI, Fotor and Craiyon. Tech giants - including Google - are releasing their own, so we can only speculate that more value will come in the future.
4 Ways Threat Actors Weaponize AI Image Generators
Like almost all technologies, AI image generators can be abused by malicious actors. In fact, they have been used for all sorts of nefarious purposes. But exactly what types of scams can criminals pull off with the help of AI image generators?
1. Social Engineering
One obvious thing that threat actors can do with AI image generators is to engage in social engineering; for example, creating fake social media profiles . Some of these programs can create incredibly realistic images that look like real photos of real people, and scammers can use these fake social media profiles for phishing purposes.
Unlike photos of real people, AI-generated photos cannot be discovered through reverse image searches, and cybercriminals don’t have to use a limited number of photos to deceive targets — using AI, they can generate any number of photos, Build a compelling online identity from the ground up.
However, in real life, threat actors can use AI image generators to trick people. In April 2022, Tech Talk blogger Ben Dickinson received an email from a law firm claiming that he had used an image without permission. The attorneys emailed a DMCA copyright infringement notice, telling Dickinson he needed to link back to their client or remove the image.
Dickinson searched the law firm on Google and found the official website. It all seems completely legal; the website even has photos of 18 attorneys, including their biographies and credentials. But none of this is true. The photos were all generated by artificial intelligence, and the alleged copyright infringement notice was sent by someone hoping to extort backlinks from unsuspecting bloggers.
2. Charity Scam
When devastating earthquakes hit Turkey and Syria in February 2023, millions of people around the world expressed their gratitude by donating clothes, food and money. Solidarity with victims.
Scammers are taking advantage of this, using artificial intelligence to create realistic images and solicit donations, according to a BBC report. A scammer showed off AI-generated images of ruins on TikTok Live, asking their viewers for donations. Another posted an AI-generated image of a Greek firefighter rescuing an injured child from rubble and asked his followers to donate.
One can only imagine what types of charity scams criminals will run with the help of artificial intelligence in the future, but it’s a safe bet that they will only get better at abusing the software.
3. Deepfakes and disinformation
Governments, activist groups and think tanks have long warned of the dangers of deepfake AI image generators, and that’s because nothing can Stop disinformation agents from creating false images with the help of bots and promoting it on social media.
In March 2022, a fake video depicting the Ukrainian president telling Ukrainians to surrender circulated online, according to NPR. While this is just one example, the possibilities are nearly endless, and there are countless ways threat actors can damage someone’s reputation, promote false narratives or spread fake news with the help of artificial intelligence.
4. Advertising fraud
Trend Micro researchers discovered in 2022 that scammers are using artificial intelligence-generated content to create misleading ads and promote shady products. They create images suggesting popular celebrities use certain products and run advertising campaigns based on those images.
For example, one ad for “Financial Advice Opportunities” features Tesla’s founder and CEO. Of course, Musk never endorsed the product in question, but the AI-generated footage made it look like this, presumably to lure unsuspecting viewers into clicking on the ad.
Artificial Intelligence and Cybersecurity: Complex Issues We Need to Solve
Looking ahead, government regulators and cybersecurity experts may have to work together to address the emerging emergence of AI-driven cybercrime threats. But how can we regulate AI and protect ordinary people without stifling innovation and limiting digital freedom? This issue will become prominent in the coming years.
Until you get an answer, do what you can to protect yourself: scrutinize anything you see online, avoid questionable websites, use security software, keep your devices up to date, and learn to use Use artificial intelligence to your advantage.
Original title: AI Image Generators: An Emerging Cybersecurity Threat
##Original author: DAMIR MUJEZINOVIC
The above is the detailed content of AI Image Generator: An Emerging Cybersecurity Threat. For more information, please follow other related articles on the PHP Chinese website!
 Gemini 2.5 Pro vs GPT 4.5: Can Google Beat OpenAI's Best?Apr 24, 2025 am 09:39 AM
Gemini 2.5 Pro vs GPT 4.5: Can Google Beat OpenAI's Best?Apr 24, 2025 am 09:39 AMThe AI race is heating up with newer, competing models launched every other day. Amid this rapid innovation, Google Gemini 2.5 Pro challenges OpenAI GPT-4.5, both offering cutting-edge advancements in AI capabilities. In this Gem
 Karun Thanks's bluepring for data science successApr 24, 2025 am 09:38 AM
Karun Thanks's bluepring for data science successApr 24, 2025 am 09:38 AMKarun Thankachan: A Data Science Journey from Software Engineer to Walmart Senior Data Scientist Karun Thankachan, a senior data scientist specializing in recommender systems and information retrieval, shares his career path, insights on scaling syst
 We Tried Gemini 2.5 Pro Experimental and It's Mind-Blowing!Apr 24, 2025 am 09:36 AM
We Tried Gemini 2.5 Pro Experimental and It's Mind-Blowing!Apr 24, 2025 am 09:36 AMGoogle DeepMind's Gemini 2.5 Pro (experimental): A Powerful New AI Model Google DeepMind has released Gemini 2.5 Pro (experimental), a groundbreaking AI model that has quickly ascended to the top of the LMArena Leaderboard. Building on its predecess
 Top 5 Code Editors to Vibe Code in 2025Apr 24, 2025 am 09:31 AM
Top 5 Code Editors to Vibe Code in 2025Apr 24, 2025 am 09:31 AMRevolutionizing Software Development: A Deep Dive into AI Code Editors Tired of endless coding, constant tab-switching, and frustrating troubleshooting? The future of coding is here, and it's powered by AI. AI code editors understand your project f
 5 Jobs AI Can't Replace According to Bill GatesApr 24, 2025 am 09:26 AM
5 Jobs AI Can't Replace According to Bill GatesApr 24, 2025 am 09:26 AMBill Gates recently visited Jimmy Fallon's Tonight Show, talking about his new book "Source Code", his childhood and Microsoft's 50-year journey. But the most striking thing in the conversation is about the future, especially the rise of artificial intelligence and its impact on our work. Gates shared his thoughts in a hopeful yet honest way. He believes that AI will revolutionize the world at an unexpected rate and talks about work that AI cannot replace in the near future. Let's take a look at these tasks together. Table of contents A new era of abundant intelligence Solve global shortages in healthcare and education Will artificial intelligence replace jobs? Gates said: For some jobs, it will Work that artificial intelligence (currently) cannot replace: human touch remains important Conclusion
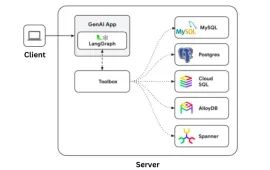 Google Gen AI Toolbox: A Python Library for SQL DatabasesApr 24, 2025 am 09:23 AM
Google Gen AI Toolbox: A Python Library for SQL DatabasesApr 24, 2025 am 09:23 AMGoogle's Gen AI Toolbox for Databases: Revolutionizing Database Interaction with Natural Language Google has unveiled the Gen AI Toolbox for Databases, a revolutionary open-source Python library designed to simplify database interactions using natura
 OpenAI's GPT 4o Image Generation is SUPER COOLApr 24, 2025 am 09:21 AM
OpenAI's GPT 4o Image Generation is SUPER COOLApr 24, 2025 am 09:21 AMOpenAI's ChatGPT Now Boasts Native Image Generation: A Game Changer ChatGPT's latest update has sent ripples through the tech world with the introduction of native image generation, powered by GPT-4o. Sam Altman himself hailed it as "one of the
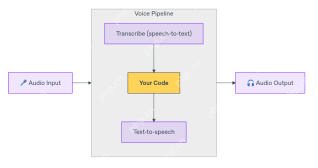 How to Build Multilingual Voice Agent Using OpenAI Agent SDK? - Analytics VidhyaApr 24, 2025 am 09:16 AM
How to Build Multilingual Voice Agent Using OpenAI Agent SDK? - Analytics VidhyaApr 24, 2025 am 09:16 AMOpenAI's Agent SDK now offers a Voice Agent feature, revolutionizing the creation of intelligent, real-time, speech-driven applications. This allows developers to build interactive experiences like language tutors, virtual assistants, and support bo


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Dreamweaver CS6
Visual web development tools

WebStorm Mac version
Useful JavaScript development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

SublimeText3 Mac version
God-level code editing software (SublimeText3)






