<p> 2018PHP classic entry source code </p> <p> <span>2018PHP Classic Introductory Course Address:</span> </p> <p> <a href="http://www.php.cn/course/897.html" target="_blank">http://www.php.cn/course/897.html</a> </p>
Courseware source code24991242018-05-09
<p> <strong><span style="font-size:14px;">PHP Practical Combination of Tian Long Ba Bu and IQiyi Movie Website</span></strong> </p> <p> Video playback address: <a href="http://www.php.cn/course/801.html" target="_blank">http://www.php.cn/course/801.html</a> </p>
Courseware source code26360412018-04-16- vip courseware source code27449202018-03-17
- Courseware source code27489042018-03-16
- Courseware source code27854822021-12-14

<p> ThinkPHP basic practical notes + PPT </p> <p> Course playback address: <a href="http://www.php.cn/course/864.html" target="_blank">http://www.php.cn/course/864.html</a> </p>
Courseware source code27988852018-03-05
Bootstrap, from Twitter, is a very popular front-end framework. Bootstrap is based on HTML, CSS, and JavaScript. It is simple and flexible, making web development faster. It was developed by Twitter designers Mark Otto and Jacob Thornton and is a CSS/HTML framework. Bootstrap provides elegant HTML and CSS specifications, which are written in the dynamic CSS language Less. Bootstrap has been very popular since its launch and has been a popular open source project on GitHub, including NASA's MSNBC (Microsoft National Broadcasting Company) Breaking News. Some frameworks that are familiar to domestic mobile developers, such as the WeX5 front-end open source framework, are also performance optimized based on the Bootstrap source code.
php e-book28133422018-03-03
Text manipulation exists in almost any application, and handling text properly can improve application performance. <br /> This book introduces VB. NET text processing, such as text storage, text replacement and appending, etc. The book compares the pros, cons, and speed of various text manipulation methods in detail, helping you to easily choose the most appropriate method in your application. This book focuses on using simple language. NET Framework's most important tools for processing strings - regular expressions, and introduces how to build your own expressions for matching and manipulating text. The explanations in this book are practical and vivid, and a large amount of code in the book can be directly used in your applications. <br /> This book is suitable for work. NET developers who want to improve text processing efficiency in their applications. <br /> <br /> Table of Contents <br /> <br /> Chapter 1 How the system processes text<br /> 1.1. net framework<br /> 1.1.1 Common Language Runtime<br /> 1.1.2. net framework class library<br /> 1.2 Text is a data type<br /> 1.2.1 visual basic. net data types<br /> 1.2.2 Characters and character sets<br /> 1.2.3 String data type<br /> 1.3 Text Storage<br /> 1.3.1 Cache technology<br /> 1.3.2 Built-in<br /> 1.3.3 Other methods<br /> 1.3.4. net implementation<br /> 1.4 String operations<br /> 1.4.1 Connection string<br /> 1.4.2 Substring<br /> 1.4.3 Comparing strings<br /> 1.4.4 Data type conversion<br /> 1.4.5 Format string<br /> 1.5 String Usage<br /> .1.5.1 Constructing String<br /> 1.5.2 Analyzing strings<br /> 1.6 Internationalization<br /> 1.7. net resource file<br /> 1.8 Summary<br /> Chapter 2 String and stringbuilder classes<br /> 2.1 Learn the tools you will use in this chapter<br /> 2.2 Text Construction<br /> 2.3 visual basic and. net framework<br /> 2.3.1 Index<br /> 2.3.2 Null value and empty string<br /> 2.4 String class<br /> 2.4.1 Built-in string<br /> 2.4.2 Construction<br /> 2.4.3 Assigning a value to a string<br /> 2.5 stringbuilder class<br /> 2.5.1 Length and capacity<br /> 2.5.2 tostring() method<br /> 2.6 String operations<br /> 2.61 Connection<br /> 2.6.2 Substring<br /> 2.6.3 Comparing strings<br /> 2.6.4 Format<br /> 2.7 Use of strings<br /> 2.7.1 Create string<br /> 2.7.2 Mark<br /> 2.7.3 Reverse the order of strings<br /> 2.7.4 Insertion, deletion and replacement<br /> 2.7.5 Choosing between string and stringbuilder<br /> 2.8 Summary<br /> Chapter 3 String Conversion<br /> 3.1 tostring() method<br /> 3.2 Represent numerical values as strings<br /> 3.3 Represent date and time as string<br /> 3.4 Represent other objects as strings<br /> 3.5 Use string to represent string<br /> 3.6 Represent strings as other types<br /> 3.6.1 Convert strings to numbers<br /> 3.6.2 Convert string to date and time<br /> 3.7 Moving strings between collections and arrays<br /> 3.7.1 Array<br /> 3.7.2 arraylist object<br /> 3.7.3 idictionary object<br /> 3.8 Summary<br /> Chapter 4 Internationalization<br /> 4.1 unicode<br /> 4.2. net framework coding class<br /> 4.3 Processing strings<br /> 4.3.1 cultureinfo class<br /> 4.3.2 Uppercase and lowercase<br /> 4.3.3 Situations where culturally sensitive operations are not required<br /> 4.3.4 Sorting<br /> 4.4 Processing characters<br /> 4.4.1 Necessary information about characters<br /> 4.4.2 Agency pair<br /> 4.4.3 Combining characters<br /> 4.5 Formatting unicode strings<br /> 4.6 Summary<br /> Chapter 5 Regular Expressions<br /> 5.1 system. text. regularexpressions<br /> 5.2 regex class<br /> 5.2.1 regexoptions<br /> 5.2.2 Class constructor<br /> 5.2.3 ismatch() method<br /> 5.2.4 replace() method<br /> 5.2.5 split() method<br /> 5.3 match and matchcollection classes<br /> 5.4 Regex detector example<br /> 5.5 Basic regular expression syntax<br /> 5.5.1 Match different character classes<br /> 5.5.2 Specify matching position<br /> 5.5.3 Specify repeated characters<br /> 5.5.4 Specified replacement<br /> 5.5.5 Special characters<br /> 5.6 Summary<br /> Chapter 6 Advanced Concepts of Regular Expressions<br /> 6.1 Grouping, substitution and backreferencing<br /> 6.1.1 Simple grouping<br /> 6.1.2 group and groupcollection classes<br /> 6.1.3 Replacement<br /> 6. i. 4 Backreference<br /> 6.1.5 Advanced Group<br /> 6.2 Making decisions in regular expressions<br /> 6.3 Setting options within regular expressions<br /> 6.4 Rules of regular expression engine<br /> 6.5 Summary<br /> Chapter 7 Regular Expression Patterns<br /> 7.1 Verification characters<br /> 7.2 Verification numbers<br /> 7.2.1 Only numbers<br /> 7.2.2 Contains only integer numbers<br /> 7.2.3 Floating point numbers<br /> 7.3 Verify phone number<br /> 7.4 Verify zip code<br /> 7.5 Verify email address<br /> 7.5.1 Verify IP address<br /> 7.5.2 Verify domain name<br /> 7.5.3 Verify personal address<br /> 7.5.4 Verify complete address<br /> 7.6 Analyze an smtp log file<br /> 7.7 html tag<br /> 7.7.1 Clear html from user input<br /> 7.7.2 Extract all html tags<br /> 7.7.3 HTML extraction example<br /> 7.8 Summary<br /> Appendix a string class<br /> a. 1 Constructor<br /> a. 2 Properties<br /> a. 3 Methods<br /> Appendix b stringbuilder class<br /> b. 1 Constructor<br /> b. 2 Properties<br /> b. 3 Methods<br /> Appendix c Regular expression syntax<br /> c. 1 Match characters<br /> c. 2 Repeating characters<br /> c. 3 Positioning characters<br /> c. 4 Grouping characters<br /> c. 5 Decision Characters<br /> c. 6 Replacement characters<br /> c. 7 Escape sequences<br /> c. 8 Option flag<br /> Appendix d Technical support, errata and code download<br /> d. 1 How to download the sample code of this book<br /> d. 2 Errata<br /> d. 3 e-mail support<br /> d. 4 p2p. wrox. com<br /> <div> <br /> </div>
php e-book28077032018-03-03
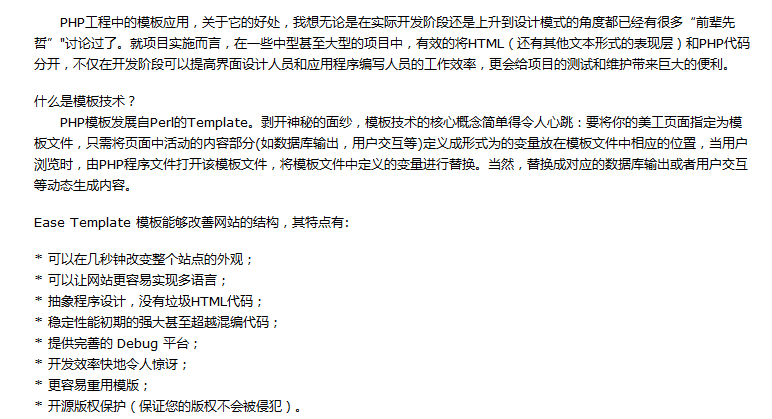
Ease Template is a PHP-specific template system, referred to as ET. <br /> There are currently many types of templates. Since each template targets different directions, they can be roughly divided into:<br /> 1. Compilation and execution (high execution efficiency) requires configuring the Cache directory, which is relatively troublesome and consumes relatively little CPU resources. <br /> 2. Direct call (convenient for development), the program can be executed without configuring the Cache directory. If the algorithm is good, it can reduce resource usage. <br /> This template uses simple syntax that allows users to master and apply it proficiently in the shortest time. In order to have a wider application, this template supports both compilation and execution and calling engines, and ensures the most concise algorithm and the principle of simple program structure. Compared with the same template program, the program code will be less, the variables and statements in the template are clearer, and the advanced serial structure is used to improve the template operation speed, which can have a better degree of separation under the same operation, and also has unique processing for the security of the template. Method, even if a hacker understands the structure or the Cache directory operation method, he cannot obtain program-related information through the Cache file. <br />
php e-book28072632018-03-03
<p> <span style="color:#333333;font-family:arial, Song Dynasty, sans-serif;font-size:14px;background-color:#FFFFFF;">This book is based on the latest version of PHP4.0, starting from Starting from the history, characteristics, and functions of PHP, it gradually introduces the basic statements of the PHP language, database applications, as well as knowledge and skills such as writing, debugging, and troubleshooting, and analyzes it in detail through typical examples. </span> </p> <p> <span style="color:#333333;font-family:arial, Song Dynasty, sans-serif;font-size:14px;background-color:#FFFFFF;">Chapter 1 Initial understanding of PHP</span> </p> <span style="color:#333333;font-family:arial, 宋体, sans-serif;font-size:14px;background-color:#FFFFFF;"> 1. 1 PHP and its characteristics</span><br /> <span style="color:#333333;font-family:arial, 宋体, sans-serif;font-size:14px;background-color:#FFFFFF;"> 1. 2 Development of PHP</span><br / > <span style="color:#333333;font-family:arial, 宋体, sans-serif;font-size:14px;background-color:#FFFFFF;"> 1. 3 Introduction to the functions of PHP</span><br /> <span style="color:#333333;font-family:arial, 宋体, sans-serif;font-size:14px;background-color:#FFFFFF;"> 1. 4 Comparison between PHP and other CGI</span> <br /> <span style="color:#333333;font-family:arial, 宋体, sans-serif;font-size:14px;background-color:#FFFFFF;"> 1. 4. 1 Introduction to CGI</span>
php e-book28165852018-03-03
DoitPHP (original Tommyframework) in short: DoitPHP runs efficiently, is easy to learn and use, and is easy to expand. In other words: DoitPHP is efficient yet powerful, flexible yet scalable. <br /> <div> <br /> </div>
php e-book28075892018-03-03
H5 is a hypermedia document on the World Wide Web called a page. The page where an organization or individual places the starting point on the World Wide Web is called the homepage or home page. The homepage usually includes pointers (hyperlinks) to other related pages or other nodes. The so-called hyperlink is a Uniform Resource Locator pointer. , which allows the browser to easily access new web pages by activating (clicking on it). This is also one of the most important reasons why HTML is widely used. An organic collection of pages that are logically viewed as a whole is called a website. Hypertext Markup Language is a markup language designed for "the creation of web pages and other information that can be viewed in a web browser."
php e-book28073832018-03-03
<p> ThinkPHP basic practical template + source code </p> <p> Course playback address: <a href="http://www.php.cn/course/864.html" target="_blank">http://www.php.cn/course/864.html</a> </p>
Courseware source code28044682018-03-03
Detailed network design and implementation plan (with pictures and texts), the services transmitted in this network are classified according to security levels, and MPLS VPN is implemented on the entire network. All routing devices in the network (including access routers) have the MPLS PE function. <br /> <br /> Directory:<br /> 1. Overall network plan design<br /> 2. Equipment configuration of each node<br /> 3. Routing protocol planning<br /> 4.BGP routing protocol planning<br /> 5.IP address allocation<br /> 6. Network reliability design<br /> 7.Interconnection<br /> 8. Business access solution<br /> 9.MPLS VPN design and configuration<br /> 10.QOS deployment plan<br /> 11.Network management solution<br /> 12.Network security plan
Web page production28070782018-03-02
The 4th edition of "Network Administrator Tutorial" is compiled in accordance with the requirements of the National Computer Technology and Software Professional Technical Qualification (Level) Examination, and the content closely follows the "Network Administrator Examination Syllabus". The book is divided into 8 chapters, which systematically explain the basic concepts of computer networks, the Internet and its applications, LAN technology and integrated wiring, network operating systems, application server configuration, Web website construction, network security and network management. <br /> <br /> This book has clear layers and rich content. It focuses on the combination of theory and practice and strives to reflect the latest development of computer network technology. It can be used as a teaching material for network administrator qualification examinations and basic training on various types of network and communication technologies.
Web page production28092772018-03-02
"Huawei "Network Engineer" Training Tutorial" is Huawei's internal training material. The content ranges from simple to complex, very detailed and popular, but it also explains the necessary skills of Huawei network engineers in a rich way, providing great help for the growth of network engineers. This book has a total of 529 pages. Because there are too many directories, only the following directories are briefly listed: <br /> Chapter 1 Basic knowledge of network<br /> Chapter 2 Common Network Interfaces and Cables <br /> Chapter 3 Ethernet Switch Basics <br /> Chapter 4 LAN Switch Configuration <br /> Chapter 5 Router Basics and Principles <br /> Chapter Six Introduction to Router Configuration <br /> Chapter 7 Network Layer Basics and Subnet Planning <br /> Chapter 8 IPX Protocol and Configuration <br /> Chapter 9 Common WAN protocols and configurations <br /> Chapter 10 Routing Protocol <br /> Chapter 11 Firewall and Configuration <br /> Chapter 12 DDR, ISDN configuration <br /> Chapter 13 Backup Center Configuration <br /> Chapter 14 HSRP Protocol and Configuration <br /> Chapter 15 Analysis and Treatment of Common Network Problems
Web page production28075872018-03-02
"Learning Linux Operations and Maintenance from the Old Boy: Practical Web Cluster Combat" explains in detail the construction, deployment, and optimization of small and medium-sized website clusters. The whole book can be divided into three parts, the first part of which talks about basic and important knowledge related to Linux. , the second part explains the construction of the currently popular Web environment architecture (LNMP) and enterprise-level Web optimization. The third part talks about Web cluster back-end data storage and Web cluster front-end load balancing. If you are an experienced Linux user, you can read the second part directly; but if you are a Linux beginner, please start with the basic knowledge in Chapter 1. <br /> <br /> The first part is the basics (Chapter 1~4), which briefly introduces the history of Linux, enterprise-level selection of Linux, establishment of Linux environment, enterprise-level system installation of Linux, basic optimization of Linux system, and remote connection Linux and client SSH settings, etc., and finally a more in-depth explanation of HTTP protocol and www service-related knowledge, preparing readers for building an enterprise-level Web cluster environment. <br /> <br /> The second part is Web services (Chapter 5~8), focusing on the construction of currently popular Web environment architectures such as Linux, Nginx, MySQL, PHP (LNMP), the installation and deployment of open source blog website products, Web optimization and other knowledge , preparing readers to build a complete enterprise-level website Web cluster architecture. <br /> <br /> The third part is cluster (Chapter 9~15), focusing on the Web cluster backend MySQL database, Web cluster shared storage NFS, Nginx reverse proxy load balancing, Keepalived high availability, Memcached cache and session sharing, Nagios enterprise level Monitoring and other technical practices are implemented, and finally a medium-scale website cluster architecture solution is planned for readers.
Web page production28064352018-03-02
"Practical Construction of High-Performance Linux Servers: Operation and Maintenance Monitoring, Performance Tuning and Cluster Applications" is a book published by Machinery Industry Press in 2012. The author of the book is Gao Junfeng. <br /> <br /> The whole book is divided into 5 parts. The Web application chapter introduces in detail the installation, configuration, management, usage, working principles and performance tuning techniques of Nginx, Varnish and Memcached, three very commonly used Web application software on Linux servers. The data backup and recovery chapter first describes the use and management skills of the open source backup software bacula, and explains the specific methods of performing various backup and recovery operations on bacula through examples; secondly, it explains the use of the open source data mirror backup tools rsync and unison. , and demonstrated the use of these two tools in a production environment through two enterprise-level cases; finally, it explained how to use the ext3grep tool to recover accidentally deleted data files and MySQL databases. The network storage application chapter first systematically explains the configuration and use of the network storage technology iSCSI, and then explains the use and maintenance of the distributed storage system MFS. The operation and maintenance monitoring and performance optimization chapter explains how to use Nagios for performance monitoring, as well as the performance analysis principles and optimization methods of Linux servers through a combination of theory and practice. The advanced application of clusters is a synthesis of the previous content and the core of this book. It mainly describes how to build a highly available load balancing cluster through LVS+heartbeat, piranha, and LVS+Keepalived. Secondly, it explains the configuration of Red Hat Cluster Suite RHCS. Management, maintenance and monitoring, and then explains the Oracle cluster solution, the construction, use and maintenance of the Oracle RAC database. Finally, the book ends with a practical case of building a MySQL+heartbeat+DRBD+LVS cluster system, which cleverly integrates all the core contents of the book.
Web page production28060702018-03-02
"Large Scale Web Service Development Technology" is a book published by Electronic Industry Press in July 2011. The authors are Naoya Ito, Shinji Tanaka, and Li Jian (translated). <br /> <br /> The content of "Large-Scale Web Service Development Technology" starts from the principles of operating systems and computers, and introduces the distributed methods of databases, the application of practical algorithms in the system, the principles of search engines that can support massive data, and the basis for overall overview of the system. It covers a wide range of aspects such as facility design knowledge and even introduces the economic costs of hardware. It is an indispensable reference book for operation and maintenance engineers. <br /> <br /> "Large-scale Web Service Development Technology" is an introductory book for technicians who develop and operate large-scale services. Web services are constantly growing. When the scale of its data becomes larger, it is no longer easy to process. At this time, what should be done? Is it correct? In order to avoid system downtime, what should you pay attention to when writing code? What points should be remembered when designing a system with high scalability? These are the contents of this book.
Web page production28067352018-03-02
"Unix/Linux Programming Practical Tutorial" explains the working principle of Unix and the method of implementing system commands in Unix step by step, allowing readers to understand and gradually become proficient in Unix system programming, and then have the ability to compile Unix applications. The book uses various teaching methods such as heuristics, drawing inferences from one instance, and graphic explanations. The language is vivid, the structure is reasonable, and it is easy to understand. <br /> "Unix/Linux Programming Practical Tutorial" is suitable for use as a teaching material and teaching reference book for computer and related majors in colleges and universities. It can also be used as a self-study teaching material and reference manual for developers with certain system programming foundation. <br /> <br /> Table of Contents:<br /> Chapter 1 Overview of Unix System Programming<br /> Chapter 2 Users, File Operations and Online Help: Writing the Who Command<br /> Chapter 3 Directory and File Attributes: Writing IS<br /> Chapter 4 File Systems: Writing PWD<br /> Chapter 5 Connection Control: Learning STTY<br /> Chapter 6 Programming the User: Terminal Control and Signals<br /> Chapter 7 Event-Driven Programming: Writing a Video Game<br /> Chapter 8 Processes and Programs: Writing a Command Interpreter<br /> Chapter 9 Programmable Shells, Shell Variables, and Environments: Writing Your Own Shell<br /> Chapter 10 I/0 Redirection and Pipes<br />
Web page production28062302018-03-02