Data Encryption Access Guide
1. Access prerequisites
* To use any product of the open platform, you must first become an open platform developer.
Open the homepage of the open platform, log in with your Taobao account and click 'Settled in the open platform'. You can refer to the platform access guide
Note: Security of storage encryption The scope of rectification includes all ISV apps involved in obtaining consumer privacy data. Therefore, the platform will conduct security rectification in batches based on the scale of private data involved in the app. 
##2. Open the entrance
Open platform application console-Application Management-Security Center-Data Storage Encryption, as follows Figure:
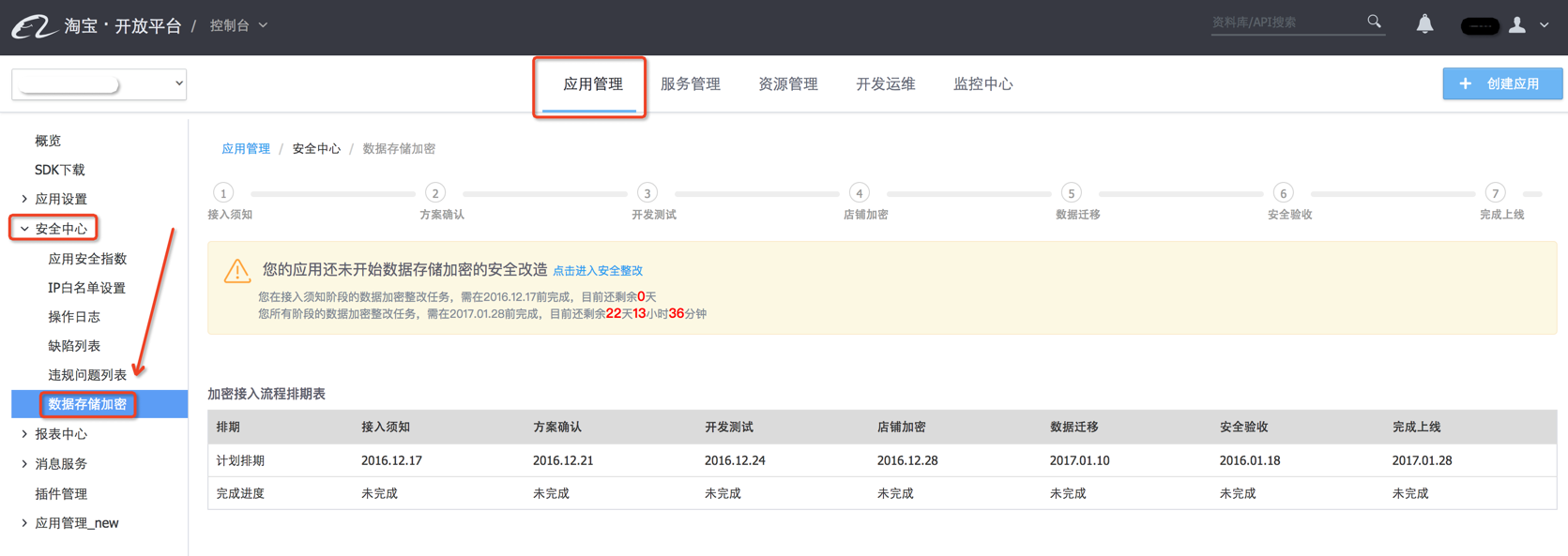
In the 'Encrypted Access Process Schedule' shown in the figure below, Schedule: Indicates the final completion time of each step; Completion progress: Indicates whether the step is completed. If it is completed, the completion time will be displayed. If not, it will be displayed as incomplete.
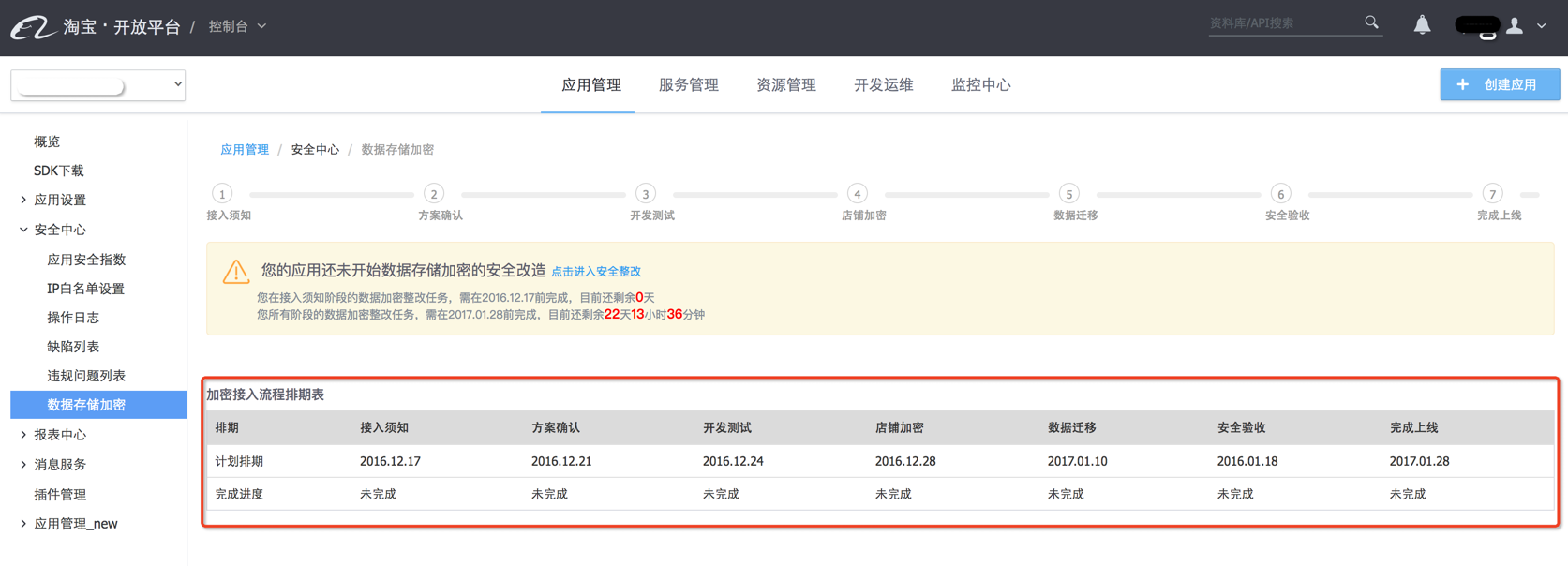
As shown below, 'Click to enter security rectification' to enter the process
##3. Process Overview
Phase 1: The application is required in the "Access Instructions" stage Developers should understand the background, requirements, and content and methods of this security rectification, so that developers can be prepared for security rectification.
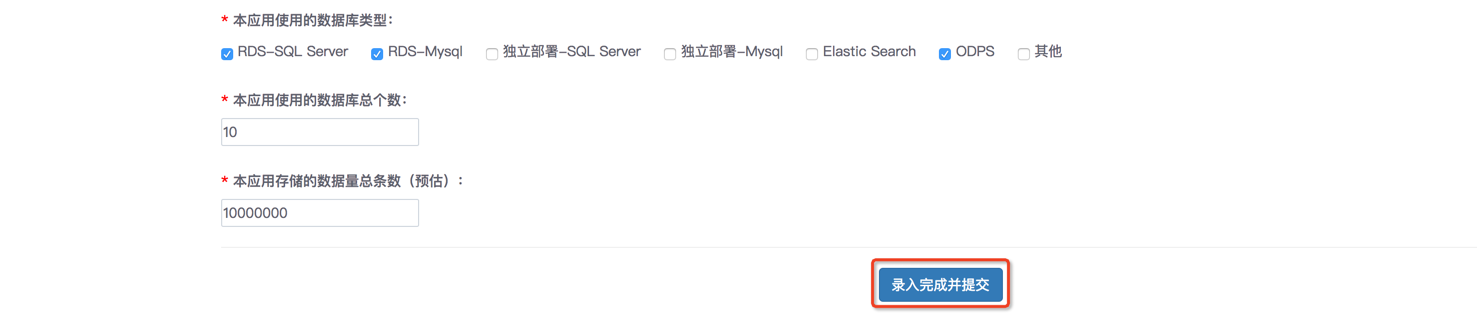
Phase 2: The "Proposal Confirmation" stage requires the developer of the application to specify the contact information of the interface person related to the project and clarify the technology of the application Architecture, application deployment, stored data scale and other relevant information to facilitate subsequent collaboration and communication with the open platform. Phase 3: The "development and testing" phase requires developers of the application to follow the access plan and development documents of this product (if fuzzy queries involving data are involved, please refer to the password Document retrieval), code development, testing and online implementation of the data encryption and decryption logic of its application in order to meet the application functional requirements of this security rectification. Phase 4: The "store encryption" stage requires the developer of the application to gradually use the user (seller) whitelist or blacklist function to The user (seller) data is connected to the developed encryption and decryption application function, which ultimately ensures that all user (seller) data required by the application can be encrypted and decrypted normally. Phase 5: The "data migration" stage requires the developer of the application to migrate its stored historical plaintext data according to the data migration document of this product. to ciphertext to avoid the risk of sensitive plaintext storage. Stage 6: The "security acceptance" stage requires the developer of the application to submit a security questionnaire to the application's system processing logic and data A security self-assessment will be conducted during the processing process so that can confirm with the relevant waiter. Phase 7: The "Complete Online" stage requires the developer of the application to confirm with the platform assistant whether all tasks of this security rectification meet the requirements. This step mainly briefly introduces the data encryption product functions and related requirements... If you have no questions about the above steps, please click 'Next'. ↓ 1) Enter the contact information of the technical interface person and business interface person to facilitate subsequent communication; 2) Please select the deployment method of this application through SAAS service , or the software is deployed independently or both deployment structures exist to provide services to existing users (sellers) of the application. 3) Choose whether this application will use Taobao's account system when providing software services to its users (buyers), or whether it will use the account system built by this application. For an introduction to account plan selection, please refer to relevant documents: Detailed explanation of account system access plan 4) Select the database type you are using (multiple choices are available) and the number of databases , data size (unit: strip, estimate) ## After filling in the above information, click 'Enter and complete Submit', wait for confirmation that the entry is completed, click 'Next' as shown below ##↓ 2) RDS database field length modification setting. When the plan is set, the platform will automatically modify the field according to the date you set. , the execution time will be completed between 2 am and 5 am. 3) Download the TOP SDK with data encryption function, and make logical judgments about switching from plain text to cipher text during the code development process to ensure that both plain text and cipher text can be processed Transitional states of coexistence. 4) You need to manually generate the unique security token code for this application (this security token code is mainly used as a constructor when the encryption and decryption TOP SDK program is initialized) Parameters are passed in so that the program can normally go to the TOP gateway to apply for its key and use the key for encryption or decryption services). 5) Use the sandbox environment officially provided by the platform to test relevant data usage scenarios. For relevant operation code examples of the above steps, please refer to: Data ciphertext retrieval plan, code development plan If you have no questions about the above steps, please click 'Next'. ↓ 1) Configure the whitelist and blacklist of users (sellers): During the encryption switching process of users (sellers) of this application, the pilot users can be selected through the whitelist function. (Seller) data encryption and decryption trials and business verification; if the user (Seller) data has special needs during the encryption switching process, a blacklist can also be temporarily used to ensure that the data of individual users (Sellers) is not encrypted. As shown below: After setting the black and white lists, proceed to 'store encryption' Next step 2) Enable data encryption for all stores: If there are no problems with encryption of all pilot stores, you need to activate data encryption for all stores (ie: cover all users (sellers) )), which also means that the previous white and black lists will be invalid. As shown in the picture: After completing the above, click 'Encrypt all stores' to proceed to the next step ↓ 2) For the specific data migration process, please refer to: Data Migration Plan If you have no questions about the above steps, please click ‘Complete Migration’ to proceed to the next step. ↓ 1) Fill in the relevant security questionnaire and conduct a security self-assessment of the system processing logic and data processing process of its application. 2) After submission, it will be reviewed by the back-end waiter. After passing the review, it can be completed online. Note: If you fail the review, you need to resubmit. If you encounter any problems during the submission process, please ask for feedback in the support center. 1. Check the access progress You can check the access progress by clicking on the 'Security Center—Data Storage Encryption' page again. Note: The red lettered part will remind you of the remaining completion time. If the rectification is not completed within the specified time, our backend assistant will send a notification reminder. As shown below: 2. Playback operation You can click on a step individually to view the specific progress. In some steps, you can modify the relevant information and resubmit. See the specific operations below 1) You can re-edit the submission steps Step 2 'Program Confirmation', Step 5 'Data Migration', Step 6 'Safety Acceptance' can be re-edited and submitted; •Click 'Confirm the plan' to modify the interface person information, database and other information and then resubmit. As shown below: #•'Data Migration' You can refer to the data migration document for the steps. After the re-migration is completed, you can submit it, as shown in the figure: •You can click the 'Safety Acceptance' step to refill the relevant safety questionnaire and submit it for review, as shown in the figure: 2) The steps for submission cannot be re-edited Step 3 'Development Test' and Step 4 'Store Encryption' cannot be re-edited for submission. Once the submission is completed It cannot be modified later and only the submitted configuration details can be viewed. 3) Notes After the entire process has been submitted and reviewed and approved, all steps will be disabled. Re-modify the submission; ##4. Process Operation Guide
•Phase 1'Access Instructions' is shown in the figure below:
•Phase 2'Plan Confirmation' As shown in the figure below:
•Phase 3 'Development Test' As shown below:
1) Select the field that requires ciphertext retrieval , please select according to actual business needs. If this application does not need to support the function of ciphertext retrieval, you do not need to select it; but if support is required, you should select carefully and verify whether the selection is accurate, because after selection, the field length of this field in the database It will change and cannot be rolled back; 
##•Phase 4 'Store Encryption '
##•Stage 5 'Data migration'
1) Developers need to migrate their historically stored plaintext data offline to ciphertext. ##•Phase 6 'Safety Acceptance '
•Stage 7 'Complete online'
5. Other operations
There is no FAQ about this document yet