Introduction to data encryption
1. Product background
1. Frequent security incidents: consumer order leakage, data value theft, etc.
2. Core business assets: data, data, data...
3. Existing management and control limitations: uncontrollable systems or applications in the ecological link, the cost of management and control is getting higher and higher
4. Security technology bottleneck: The existing encryption technology scenarios are simple and cannot meet the three-party application scenarios, and the decentralized emerging encryption technology cannot be commercialized yet
2. Product Usage
This product provides encryption capabilities for consumer sensitive data storage to prevent data leakage caused by external or internal security threats. , thereby improving the level of data security protection.
3. Product Architecture
An important means to solve data security is the encryption of sensitive data. In order to cover all aspects of protection such as circulation and storage, the solution designed for this product covers the encryption scope from the source to the ISV's persistent storage.
After using the encryption service of this product, the data output from the open platform will be encrypted from the source. This includes the TOP api containing sensitive fields, and the RDS system library containing orders. (For the specific API and field list, please see the technical documentation).
The service provider stores sensitive information in ciphertext in its own database (system push library and other databases) until it is needed, and then calls our SDK to decrypt it. In order to reduce the risk of key theft, the keys are user-granular, that is, each user's data is encrypted with a different key.
When the application needs to retrieve and display sensitive information, call the decryption function provided in the SDK to decrypt it. The SDK will automatically obtain the corresponding key from the TOP server. In addition, network requests, management and local caching of keys are automatically done by the SDK.
ISV needs to modify the code according to its own application business logic, access the SDK of this product, and complete the encryption and decryption conversion of sensitive data through the encryption, decryption and other APIs in the SDK provided by this product. .
Considering that ISVs may have fuzzy query requirements for some fields, the encryption scheme of this product also supports encryption methods that can be fuzzy queried. For details, please refer to the solution introduction in the technical documentation. 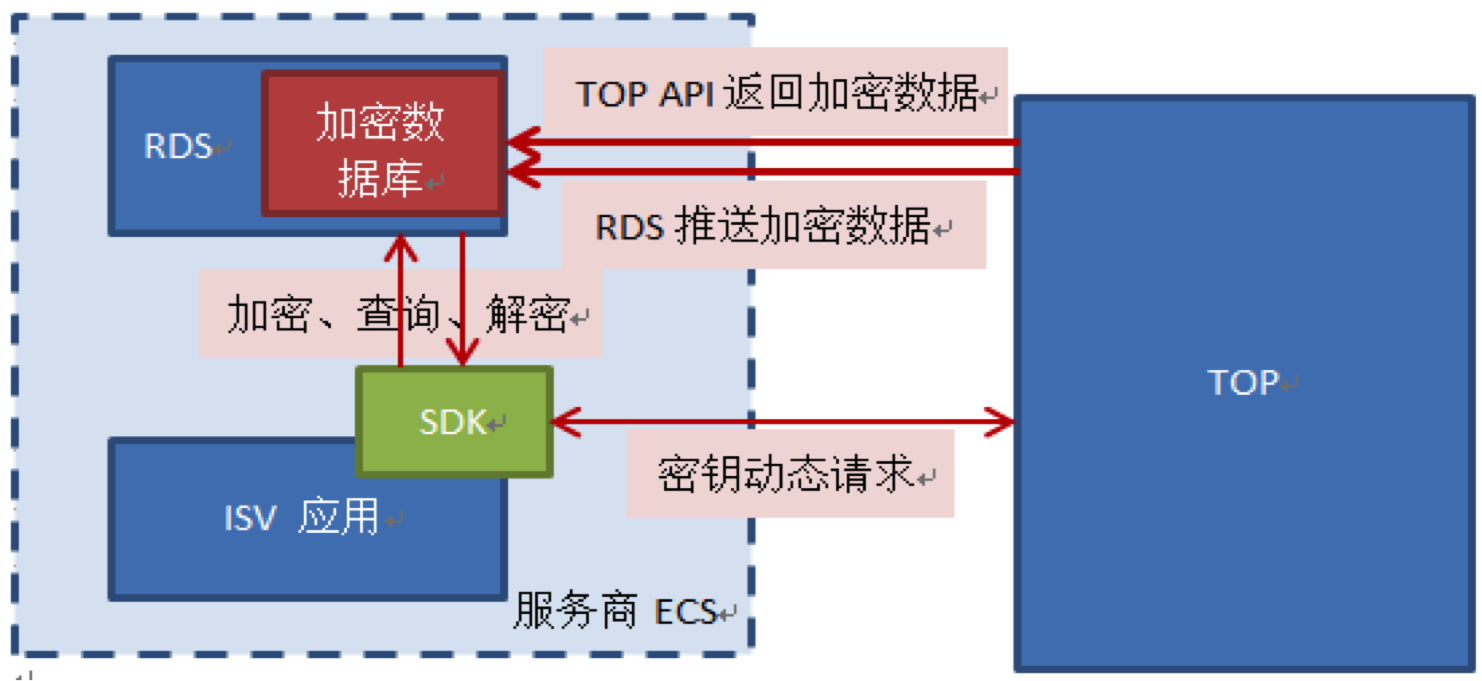
4. Product functions
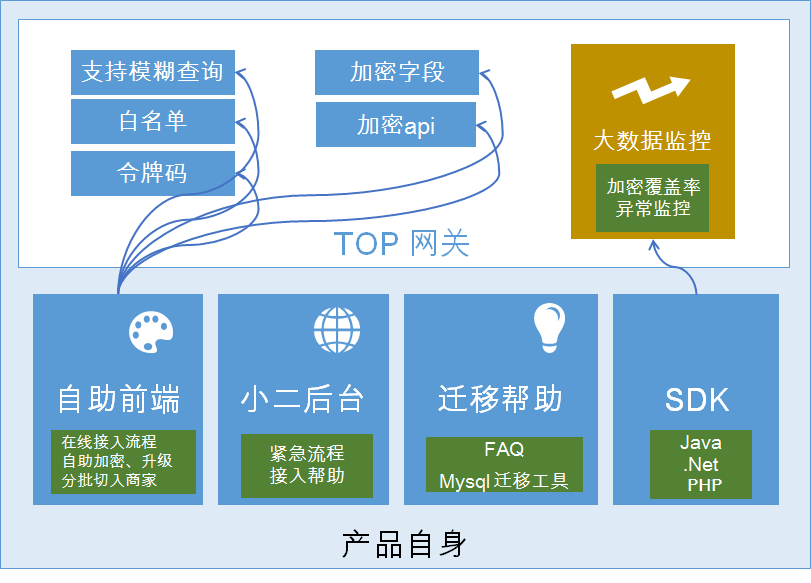
In addition to encryption services , in order to ensure that ISVs can access smoothly and can effectively operate their functions and monitor the healthy operating status of services, this product provides a series of supporting services with encryption as the core.
1. SDK: The encryption function is integrated in the TOP SDK. Encryption and decryption can be completed through the SDK without the need to manage the key.
2. Self-service front-end: On the open platform, this product provides a self-service access platform to guide ISVs to gradually access encryption services.
3. Waiter Backstage: In case of emergency, the platform where the waiter intervenes.
4. Migration help: Help center for data migration tasks.
5. Big data monitoring: Use data analysis methods to model the calling behavior of the SDK, calculate encryption coverage, and monitor and provide early warning for abnormal behavior.
五. Product features
# is an encryption product integrated in TOP. The encryption services of this product include The following advantages:
1. Basic security guarantee
Sensitive data encryption adopts the internationally accepted AES-128 standard, which ensures data security and versatility. Assure.
2. Separation of database content and key storage management
The service provider's ECS and RDS only store encrypted data and do not save keys. Just access the SDK provided by this product, and the key will dynamically initiate a dynamic request to TOP during the running of the service provider's application. This not only enhances the security factor, but also simplifies the service provider's cost of managing and storing keys.
3. Seamlessly integrated into TOP’s open scenarios and fully encrypted.
The encryption service is seamlessly integrated into TOP’s order service. Once encryption is turned on, The content returned from the TOP api to the content pushed by RDS will be converted into ciphertext, ensuring that the data exists in an encrypted state from the source to the entire transmission and storage process.
4. Both security and service smoothness:
The service of this product supports key upgrade operations. The SDK of this product provides intelligent and rich APIs that can automatically identify the version of ciphertext stored in the database, automatically encrypt and decrypt it. After the service provider accesses our SDK, it can upgrade the key under the condition of non-stop service.
5. Algorithm; supports fuzzy query
The encryption service of this product supports fuzzy query for fragments of long text (such as nicknames and names).
6. Easy to use
The encryption solution of this product does not depend on hardware. The SDK of this product is integrated into the existing TOP SDK. There are no special requirements for the database, and the cost of use and modification is low.
FAQ
- There is no FAQ about this document








