 Mobile Game Tutorial
Mobile Game Tutorial Mobile Game Guide
Mobile Game Guide Introduction to Xingyan horse-killing weapons in 'Interstellar Area 52'
Introduction to Xingyan horse-killing weapons in 'Interstellar Area 52'Introduction to Xingyan horse-killing weapons in 'Interstellar Area 52'
Hello everyone, game lovers! Today, PHP editor Yuzi will introduce to you the mysterious and powerful Xingyan horse-killing weapon in "Interstellar Area 52". It is said that in the distant ruins of the Keto civilization, the Keto Empire has mastered the power of the stars, plundered the stars and forged amazing weapons. If you are interested in more details and highlights of the Xingyan Horse-Slaying Weapon, please continue reading this article. We will delve into its background story, attributes and abilities, how to obtain it, and other aspects to unveil the mystery of this legendary weapon for you!

"Star Zone 52" Xing Yan Horse Killing Weapon Introduction
Xing Yan Horse Killing

1. Basic attributes
HP: 2625
Attack: 52
Defense: 79
2. Refinement data
Stars : 1
HP: 56K
Attack: 121
Defense: 682
Damage bonus: 2.0%
Damage reduction: 2.0%
3. Effect:
Increases the wearer's damage reduction by 7.5%
Every 10% of life lost in battle will increase the damage caused【 1.2%/1.8%/2.4%/3%/3.6%/4.2%/4.8%], which can increase the damage by up to [12%/18%/24%/30%/36%/42%/48%].
The above is the detailed content of Introduction to Xingyan horse-killing weapons in 'Interstellar Area 52'. For more information, please follow other related articles on the PHP Chinese website!
 Assassin's Creed Shadows The Corrupt Daikan WalkthroughMay 16, 2025 am 04:51 AM
Assassin's Creed Shadows The Corrupt Daikan WalkthroughMay 16, 2025 am 04:51 AMThis guide details the Assassin's Creed Shadows optional quest, "The Corrupt Daikan," providing a step-by-step walkthrough. Location: Omi region Quest Type: The League > Katsuhime > The Corrupt Daikan Unlock: Automatically after comp
 Tears of the Kingdom - Motsusis Shrine Walkthrough - The Legend of Zelda: Tears of the KingdomMay 16, 2025 am 04:50 AM
Tears of the Kingdom - Motsusis Shrine Walkthrough - The Legend of Zelda: Tears of the KingdomMay 16, 2025 am 04:50 AMTo reach the shrine, you must navigate to the upper section of the labyrinth and descend into a small chamber.Once inside this chamber, proceed to drop down on the western side to locate the shrine.The challenge lies in finding the shrine, which is q
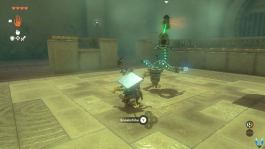 Tears of the Kingdom - Sinatanika Shrine Walkthrough - The Legend of Zelda: Tears of the KingdomMay 16, 2025 am 04:49 AM
Tears of the Kingdom - Sinatanika Shrine Walkthrough - The Legend of Zelda: Tears of the KingdomMay 16, 2025 am 04:49 AMThis is a straightforward combat training session focused on Sneakstrike, also known as stealth attacks. To execute a Sneakstrike, you must be in a crouched position and positioned directly behind your target. You will receive a prompt indicating whe
 Tears of the Kingdom - All Eldin Side-Quests - The Legend of Zelda: Tears of the Kingdom WalkthroughMay 16, 2025 am 04:47 AM
Tears of the Kingdom - All Eldin Side-Quests - The Legend of Zelda: Tears of the Kingdom WalkthroughMay 16, 2025 am 04:47 AMThe Eldin region, a fiery and mountainous area, is the home of the Gorons and features the imposing Death Mountain at its center. This region is situated in the north-eastern section of the map, positioned to the west of the Akkala region, north of t
 Monster Hunter Wilds: Congalala (Large Monster)May 16, 2025 am 04:46 AM
Monster Hunter Wilds: Congalala (Large Monster)May 16, 2025 am 04:46 AMConfronting the Congalala in Monster Hunter Wilds: A Comprehensive Guide This hefty beast, available for both capture and slaying, presents a unique challenge in Monster Hunter Wilds. Characterized by its pink fur, prominent crest (a male display o
 Best Graphics Settings for The Precinct on PCMay 16, 2025 am 04:45 AM
Best Graphics Settings for The Precinct on PCMay 16, 2025 am 04:45 AMIf you're seeking the ideal settings for The Precinct on your PC, you'll be pleased to know that this game performs smoothly, even on older GPUs. However, you can make some adjustments to enhance either the visuals or the frame rate, depending on you
 Tears of the Kingdom - A Bottled Cry for Help Walkthrough - The Legend of Zelda: Tears of the KingdomMay 16, 2025 am 04:44 AM
Tears of the Kingdom - A Bottled Cry for Help Walkthrough - The Legend of Zelda: Tears of the KingdomMay 16, 2025 am 04:44 AMBegin your adventure by locating the Bottled Letter on the beach nestled between Hateno Bay and Kitano Bay, just south of the Hateno Research Lab.It appears someone is in a bit of a jam and is reaching out for assistance—anyone's help, really. They'v
 Tears of the Kingdom - A Picture for Dueling Peaks Stable Walkthrough - The Legend of Zelda: Tears of the KingdomMay 16, 2025 am 04:42 AM
Tears of the Kingdom - A Picture for Dueling Peaks Stable Walkthrough - The Legend of Zelda: Tears of the KingdomMay 16, 2025 am 04:42 AMYou can initiate this quest by examining the empty picture frame located at Dueling Peaks Stable.The task requires us to capture an image of the most stunning sunrise. It appears that the ideal spot for this is at the summit of Tuft Mountain, which l


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 Linux new version
SublimeText3 Linux latest version

SublimeText3 English version
Recommended: Win version, supports code prompts!

Notepad++7.3.1
Easy-to-use and free code editor

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.






