 Technology peripherals
Technology peripherals AI
AI FisheyeDetNet: the first target detection algorithm based on fisheye camera
FisheyeDetNet: the first target detection algorithm based on fisheye cameraFisheyeDetNet: the first target detection algorithm based on fisheye camera
Target detection is a relatively mature problem in autonomous driving systems, among which pedestrian detection is one of the earliest algorithms to be deployed. Very comprehensive research has been carried out in most papers. However, distance perception using fisheye cameras for surround view is relatively less studied. Due to large radial distortion, standard bounding box representation is difficult to implement in fisheye cameras. To alleviate the above description, we explore extended bounding box, ellipse, and general polygon designs into polar/angular representations and define an instance segmentation mIOU metric to analyze these representations. The proposed model fisheyeDetNet with polygonal shape outperforms other models and simultaneously achieves a mAP metric of 49.5% on the Valeo fisheye camera dataset for autonomous driving. Currently, this is the first study on target detection algorithms based on fisheye cameras in autonomous driving scenarios.
Article link: https://arxiv.org/pdf/2404.13443.pdf
Network structure
Our network structure is built on the YOLOv3 network Based on the model, various representations of bounding boxes, rotated bounding boxes, ellipses, polygons, etc. are performed. To enable the network to be ported to low-power automotive hardware, we use ResNet18 as the encoder. Compared with the standard Darknet53 encoder, the parameters are reduced by more than 60%. The proposed network architecture is shown in the figure below.

Bounding Box Detection
Our bounding box model is the same as YOLOv3, except that the Darknet53 encoder is replaced with a ResNet18 encoder. Similar to YOLOv3, object detection is performed at multiple scales. For each grid in each scale, predict object width (), height (), object center coordinates (,), and object class. Finally, non-maximum suppression is used to filter redundant detections.
Rotated bounding box detection
In this model, the orientation of the box is regressed along with the regular box information (,,,). Directional ground truth range (-180 to 180°) normalized between -1 and 1.
Ellipse detection
Ellipse regression is the same as oriented box regression. The only difference is the output representation. So the loss function is also the same as the directed box loss.
Polygon Detection
Our proposed polygon-based instance segmentation method is very similar to the PolarMask and PolyYOLO methods. Instead of using sparse polygon points and single-scale predictions like PolyYOLO. We use dense polygon annotation and multi-scale prediction.
Experimental comparison
We evaluated the Valeo fisheye dataset, which has 60K images. The images were captured from 4 surround-view cameras in Europe, North America and Asia.
Each model is compared using the average precision metric (mAP) with an IoU threshold of 50%. The results are shown in the table below. Each algorithm is evaluated based on two criteria—identical performance and instance segmentation performance.



The above is the detailed content of FisheyeDetNet: the first target detection algorithm based on fisheye camera. For more information, please follow other related articles on the PHP Chinese website!
 Emergency Operator Voice Chatbot: Empowering AssistanceMay 07, 2025 am 09:48 AM
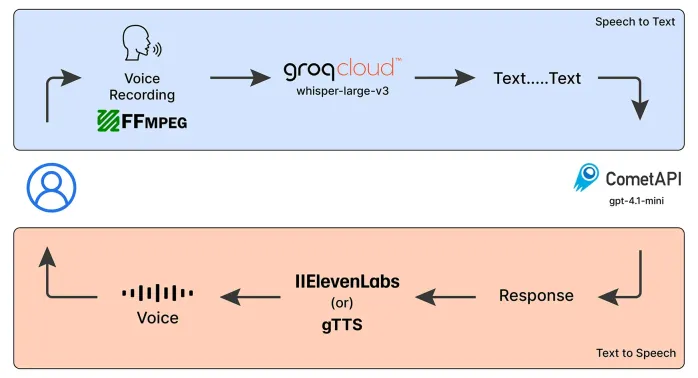
Emergency Operator Voice Chatbot: Empowering AssistanceMay 07, 2025 am 09:48 AMLanguage models have been rapidly evolving in the world. Now, with Multimodal LLMs taking up the forefront of this Language Models race, it is important to understand how we can leverage the capabilities of these Multimodal model
 Microsoft's Phi-4 Reasoning Models Explained SimplyMay 07, 2025 am 09:45 AM
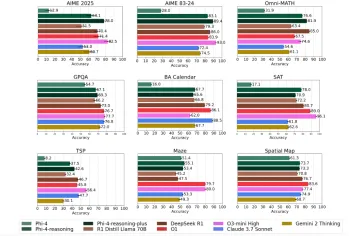
Microsoft's Phi-4 Reasoning Models Explained SimplyMay 07, 2025 am 09:45 AMMicrosoft isn’t like OpenAI, Google, and Meta; especially not when it comes to large language models. While other tech giants prefer to launch multiple models almost overwhelming the users with choices; Microsoft launches a few,
 Top 20 Git Commands Every Developer Should Know - Analytics VidhyaMay 07, 2025 am 09:44 AM
Top 20 Git Commands Every Developer Should Know - Analytics VidhyaMay 07, 2025 am 09:44 AMGit can feel like a puzzle until you learn the key moves. In this guide, you’ll find the top 20 Git commands, ordered by how often they are used. Each entry starts with a quick “What it does” summary, followed by an image display
 Git Tutorial for BeginnersMay 07, 2025 am 09:36 AM
Git Tutorial for BeginnersMay 07, 2025 am 09:36 AMIn software development, managing code across multiple contributors can get messy fast. Imagine several people editing the same document at the same time, each adding new ideas, fixing bugs, or tweaking features. Without a struct
 Top 5 PDF to Markdown Converter for Effortless Formatting - Analytics VidhyaMay 07, 2025 am 09:21 AM
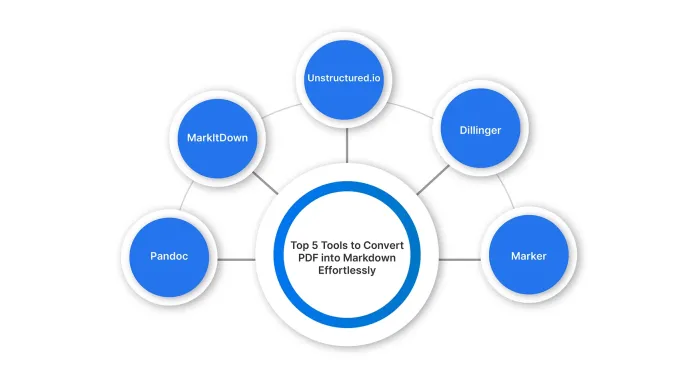
Top 5 PDF to Markdown Converter for Effortless Formatting - Analytics VidhyaMay 07, 2025 am 09:21 AMDifferent formats, such as PPTX, DOCX, or PDF, to Markdown converter is an essential tool for content writers, developers, and documentation specialists. Having the right tools makes all the difference when converting any type of
 Qwen3 Models: How to Access, Features, Applications, and MoreMay 07, 2025 am 09:18 AM
Qwen3 Models: How to Access, Features, Applications, and MoreMay 07, 2025 am 09:18 AMQwen has been silently adding one model after the other. Each of its models comes packed with features so big and sizes so quantized that they are just impossible to ignore. After QvQ, Qwen2.5-VL, and Qwen2.5-Omni this year, the
 How to Build RAG Systems and AI Agents with Qwen3May 07, 2025 am 09:10 AM
How to Build RAG Systems and AI Agents with Qwen3May 07, 2025 am 09:10 AMQwen just released 8 new models as part of its latest family – Qwen3, showcasing promising capabilities. The flagship model, Qwen3-235B-A22B, outperformed most other models including DeepSeek-R1, OpenAI’s o1, o3-mini,
 Why Sam Altman And Others Are Now Using Vibes As A New Gauge For The Latest Progress In AIMay 06, 2025 am 11:12 AM
Why Sam Altman And Others Are Now Using Vibes As A New Gauge For The Latest Progress In AIMay 06, 2025 am 11:12 AMLet's discuss the rising use of "vibes" as an evaluation metric in the AI field. This analysis is part of my ongoing Forbes column on AI advancements, exploring complex aspects of AI development (see link here). Vibes in AI Assessment Tradi


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

SublimeText3 Chinese version
Chinese version, very easy to use

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software






