What are the blockchain architectures? What are the characteristics?
Blockchain technology is widely adopted due to the range of benefits it offers, and since there is no central authority to oversee operations, blockchain is an ideal registry for joint ventures. The digital signature and verification process used in blockchain helps prevent fraudulent activities, and the information in it is not centralized, preventing it from being lost. Blockchain is a distributed ledger that is completely open to anyone. Once data is recorded in the blockchain, it is difficult to change it. The data stored within the block depends on the type of blockchain. Many investors want to know what the blockchain architecture is? Let me introduce it to you below.

What are the blockchain architectures?
1. Blockchain ledger
Blockchain, block chain, blocks contain data information, and data blocks are connected in some way to form a block chain. So, how to represent the information of each data block? The block data of Bitcoin is roughly as follows: There are roughly three parts that make up a data block: block header, block body, and Merkel root (simply understood as identity).
2. Consensus Mechanism
Everyone has to keep accounts and remember the number of bricks moved. Xiao Wang likes to write straight characters, Xiao Li likes to write numbers, and Xiao Zhang has good art talent, so he paints bricks one by one. We went up and debated for a long time but couldn't reach an agreement. So we discussed a rule, for example, the person who is older, does the best job, or has the most say in making decisions. In the end, this person will determine a consensus method, and everyone will follow it. Go back to the blockchain, select the most suitable node, and record the data according to its rules to keep the ledger consistent.
3. Cryptozoological algorithms
Cryptozoological algorithms are widely used in blockchain systems, such as marking, determining blocks, and every business involved in the blocks. For example, in the process of information communication between Xiao Wang -> Xiao Zhang -> Xiao Chen, if everyone is separated by a wall and can only see each other's arms and clothes, then Xiao Zhang will use Xiao Wang's finger characteristics, clothes, skin, and voice. Once it is determined, it is Xiao Wang. These characteristics form part of the basis for judging the information Xiao Wang delivers.
Combined with the previous blockchain structure, the connection between data blocks is actually connected by each other's blockchain hash, and this hash involves cryptography. Each block involves many transactions. Each transaction data calculates a hash value based on cryptography, which uniquely represents a transaction. Finally, this group of transaction hashes is combined and processed to obtain a hash tree. The top is what is mentioned above. of "Mecklgen".
4. Scripting system
The Bitcoin system is relatively simple, only sending and receiving Bitcoins; Ethereum has added smart contracts, allowing users to automatically write some programs. This is one of the reasons why the tokens of many new blockchain projects are developed based on ETH rather than BTC.
These running rules are all implemented by the script system. It is precisely because the script system and accounting blockchain can also record various orders, logistics, crowdfunding and other information.
5. Network routing
Everyone knows about routers. We assume that the router’s network is distributed by a nearby router, and router B can only connect to A, and C can only connect to B. In this way, analogy. B serves C and is also served by A. Everyone synchronizes data with each other and is responsible for finding adjacent routes. The network routing of blockchain is similar to this. We do not rely on the network signal transmitter in the middle, but are related to each other, and there is no center.
Characteristics of blockchain architecture
Blockchain has characteristics that traditional technical systems do not have, such as decentralized operation of the system, third-party trust, collective system maintenance, data tampering, and transaction traceability. .
First, decentralization.
The storage, transmission and verification process of blockchain data are based on a distributed system structure. The entire network is an end-to-end network composed of many nodes. There is no centralized equipment and management organization. Stopping any node will not affect the overall operation of the system.
Second, trust.
In the blockchain system, all nodes can be verified through digital signatures and transactions can be made without third-party certification. In other words, the operation process of the blockchain system does not have the trust guarantee of a third party and only relies on everyone's recognition and certification. With third-party trust, reliable operation of the system is achieved.
Third, collective maintenance.
The data in the blockchain system is jointly maintained by all nodes with accounting functions in the entire system. The damage or loss of any node will not affect the operation of the entire system. The blockchain system does not have institutions such as management centers, and its collective maintenance characteristics make it have good system stability.
Fourth, data cannot be tampered with or forged.
Data on the blockchain system cannot be tampered with or forged. Once the data has been tampered with or forged, it can technically be found immediately through the hash function mentioned above. At the same time, this also destroys the consistency of the entire data network. This kind of data tampering will not be recognized by other nodes and will lose everyone's approval, making the tampering invalid. In other words, data modifications of individual nodes in the blockchain system will not affect the databases of other nodes unless the data of nodes reaching a certain limit in the system are modified simultaneously.
Fifth, traceability.
The data of the blockchain system is traceable. We can concatenate two adjacent blocks from any time node through cryptographic methods, and reversely look for the past and present of these data with the help of the blockchain chain.
The six-level structure of blockchain
The architecture of blockchain is usually divided into six layers, namely data layer, network layer, consensus layer, incentive layer, contract layer and application. layer. Each layer has its specific functions and effects:
1. Technical layer
The technical layer is the bottom layer of the blockchain and the most important core technology layer. This layer is mainly composed of Ethereum, Bitcoin and other decentralized ledger systems. They use encryption technology to protect the security of data, use hash algorithms to record transactions, and use distributed ledger technology to reduce transaction costs and improve transaction efficiency. , and can also provide functions such as smart contracts.
2. Network layer
The network layer is the second layer of the blockchain. It is mainly a system composed of *packer (Miner)* and *miner (Miner)*. They pass The mining algorithm packages the transaction information into blocks and then publishes the blocks to the entire network. All nodes can receive the same block information. In this way, all nodes can be updated synchronously to keep the data in the network valid. It is worth mentioning that the security and durability of the blockchain mainly rely on Bitcoin miners, and the computing power of the miners will be related to the security and reliability of the blockchain.
3. Application layer
What supports the underlying data security and reliability is the application layer, which is mainly for business applications in specific fields. Taking Bitcoin as an example, the Bitcoin application layer mainly includes new transactions, user group management, address management, transaction signatures, etc. Others such as Ethereum, this layer can support applications such as smart contracts.
4. Protocol layer
The protocol layer is the bridge that connects the network layer and the application layer. It is built on the basis of the network layer and is the bridge that connects the network and applications. to provide a higher level of service. The protocol layer can define a variety of related protocols, such as IP protocol, HTTP, SSL/TLS, etc., to meet the various needs of different applications.
5. Platform layer
This layer defines a framework system for application development, which allows developers to build applications on it. The platform layer can also be called a development platform or application network. layer. In addition, it throws the protocol layer services to a higher layer and provides a more convenient interface to enable rapid development of upper-layer applications.
6. Product Layer
The product layer contains different products and is the ultimate application of blockchain technology. Only when users use blockchain technology to produce specific products, will this technology have the ability to change users' existing working methods and provide more detailed services and functions in a user-friendly way, thus bringing blockchain into full play? The greatest value of technology. These products include gaming products, financial service products, etc., all of which use blockchain technology to change the user experience.
The above content is the editor’s detailed elaboration on the issues of blockchain architecture. The goal of blockchain is to allow digital information to be recorded and distributed, but not edited. In this way, blockchain is the basis for an immutable ledger, or record of transactions that cannot be changed, deleted, or destroyed. This is why blockchain is also called distributed ledger technology (DLT). The concept of blockchain was first proposed as a research project in 1991, and had its first widespread application in 2009: Bitcoin. In the years since, blockchain usage has exploded through the creation of various cryptocurrencies, decentralized finance (DeFi) applications, non-fungible tokens (NFTs) and smart contracts.
The above is the detailed content of What are the blockchain architectures? What are the characteristics?. For more information, please follow other related articles on the PHP Chinese website!
 Tokenized Treasuries Near $6B Milestone, Led by BlackRockApr 19, 2025 am 11:44 AM
Tokenized Treasuries Near $6B Milestone, Led by BlackRockApr 19, 2025 am 11:44 AMThe value of blockchain-based U.S. Treasuries is closing in on a new milestone, with total holdings approaching $6 billion.
 title: Canary Capital Is Launching a TRX-Tracking ETFApr 19, 2025 am 11:42 AM
title: Canary Capital Is Launching a TRX-Tracking ETFApr 19, 2025 am 11:42 AMCanary Capital is looking to launch an exchange-traded fund (ETF) tracking the price of Tron's native token, TRX, according to a filing.
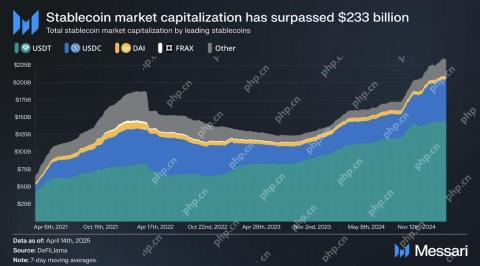 Solana Stablecoin Market Cap Hits Record $12.73 Billion as Sui Supply Reaches $800M with $60M InflowsApr 19, 2025 am 11:40 AM
Solana Stablecoin Market Cap Hits Record $12.73 Billion as Sui Supply Reaches $800M with $60M InflowsApr 19, 2025 am 11:40 AMThe stablecoin market has surpassed a total capitalization of $233 billion. Within this sector, Solana's stablecoins have reached a new all-time high market capitalization of $12.73 billion
 Canary Capital Files for Staking TRX ETF, Targeting Launch Before Spot Bitcoin ETFsApr 19, 2025 am 11:38 AM
Canary Capital Files for Staking TRX ETF, Targeting Launch Before Spot Bitcoin ETFsApr 19, 2025 am 11:38 AMCanary Capital is looking to get the U.S. Securities and Exchange Commission's sign-off for an exchange-traded fund that would track the Tron token TRX and has a staking component.
 MoonPay CEO Ivan Soto-Wright calls on US lawmakers to leave a path open to state-level regulators when passing legislation on stablecoinsApr 19, 2025 am 11:36 AM
MoonPay CEO Ivan Soto-Wright calls on US lawmakers to leave a path open to state-level regulators when passing legislation on stablecoinsApr 19, 2025 am 11:36 AMIn an April 18 X post, Soto-Wright said he wanted Congress to “keep state-regulated issuers in the game” when it comes to stablecoin regulation, referencing efforts in the House of Representatives and Senate to create a federal regulatory framework.
 Michael Saylor Dissects the Philosophy and Technological Potential of Bitcoin in '21 Truths of Bitcoin'Apr 19, 2025 am 11:34 AM
Michael Saylor Dissects the Philosophy and Technological Potential of Bitcoin in '21 Truths of Bitcoin'Apr 19, 2025 am 11:34 AMSaylor's ideas centre on the fixed 21 million coin supply of Bitcoin. He presents this shortage as a revolutionary economic idea rather than only a technical one.
 Official Trump (TRUMP) memecoin unlocked 40 million tokens, worth around $300 millionApr 19, 2025 am 11:32 AM
Official Trump (TRUMP) memecoin unlocked 40 million tokens, worth around $300 millionApr 19, 2025 am 11:32 AMThe TRUMP memecoin has gained significant popularity on the Solana network primarily due to its direct affiliation with the U.S. President Donald Trump.
 TRUMP (TRUMP) memecoin unlocks 40 million tokens, worth around $300 millionApr 19, 2025 am 11:30 AM
TRUMP (TRUMP) memecoin unlocks 40 million tokens, worth around $300 millionApr 19, 2025 am 11:30 AMThe TRUMP memecoin has gained significant popularity on the Solana network primarily due to its direct affiliation with the U.S. President Donald Trump.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

WebStorm Mac version
Useful JavaScript development tools

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.






