Protecting Privacy: A Guide to Encrypting Word Documents
Guarantee Privacy: Word Document Encryption Operation Guide
In today's highly developed information technology, our personal information, business secrets and other important data are often stored in various documents in electronic form. In order to ensure that this information is not peeked by unauthorized persons and protect the security of personal privacy and confidential information, encryption has become one of the important means. This article will introduce how to encrypt documents in the commonly used office software Word to ensure their security and privacy.
1. The Importance of Word Document Encryption
Word document is one of the document formats often used in our daily work and study, which may contain personal privacy, business secrets, personal information, etc. Sensitive information. If this information is leaked or stolen, it will cause immeasurable losses to individuals or organizations. Therefore, it is particularly important to encrypt Word documents.
2. How to encrypt Word documents
- Use password encryption
Open the Word document to be encrypted, click "File" - "Information" - "Protect Document" - "Encrypted Document". Enter the password in the pop-up dialog box, confirm it and enter the password again to ensure it is consistent. After saving the document, you will need to enter a password to view the document content next time you open the document. - Using permission settings
In addition to password protection, Word also provides the function of permission settings. You can set the document's opening, editing, printing and other permissions as needed to restrict unauthorized personnel's operations on the document. Similarly, settings can be made through "File" - "Information" - "Protect Document" - "Restrict Editing". - Use third-party encryption software
In addition to the encryption function that comes with Word, you can also use third-party encryption software to provide a higher level of encryption protection for Word documents. These software typically offer more encryption options and settings to ensure document security.
3. Precautions for encrypting documents
- Password settings
When setting a password, choose a complex enough combination, including uppercase and lowercase letters, numbers, and special characters. characters to avoid using easy-to-guess passwords and enhance document security. - Change the password regularly
In order to increase the security of the document, it is recommended to change the encryption password regularly to avoid the risk of password leakage caused by long-term use of the same password. - Reasonable sharing permissions
If you need to share encrypted documents, you should pay attention to reasonably controlling the sharing permissions to avoid misoperation or unauthorized users viewing the document content.
4. Protect privacy, starting with encrypted documents
With the continuous development of information technology, data leakage and information security issues have become increasingly prominent. Protecting personal privacy and the security of important data has become an issue that everyone should pay attention to. By encrypting Word documents in such a simple and effective way, the security and privacy of documents can be guaranteed to a certain extent. We hope that through the introduction of this article, readers can understand in more detail how to encrypt Word documents, thereby effectively protecting the privacy and security of individuals and organizations.
The above is the detailed content of Protecting Privacy: A Guide to Encrypting Word Documents. For more information, please follow other related articles on the PHP Chinese website!
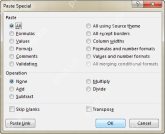 Excel Paste Special: shortcuts to copy values, comments, column width, etc.Apr 17, 2025 am 11:54 AM
Excel Paste Special: shortcuts to copy values, comments, column width, etc.Apr 17, 2025 am 11:54 AMThis tutorial unlocks the power of Excel's Paste Special feature, showing you how to significantly boost your efficiency with paste special shortcuts. Learn to paste values, formulas, comments, formats, column widths, and more, all while avoiding co
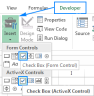 How to add, copy and delete multiple checkboxes in ExcelApr 17, 2025 am 11:01 AM
How to add, copy and delete multiple checkboxes in ExcelApr 17, 2025 am 11:01 AMThis tutorial shows you how to efficiently add, modify, and delete multiple checkboxes in Excel. Last week, we explored using checkboxes for checklists, conditional formatting, interactive reports, and dynamic charts. This week, we'll focus on the
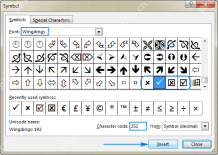 How to insert a tick symbol (checkmark) in ExcelApr 17, 2025 am 09:53 AM
How to insert a tick symbol (checkmark) in ExcelApr 17, 2025 am 09:53 AMThis tutorial explores six methods for inserting checkmarks in Excel, along with formatting and counting techniques. Excel offers two checkmark types: interactive checkboxes and tick symbols. Checkboxes allow selection/deselection via mouse clicks
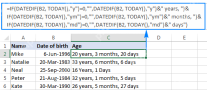 How to calculate age in Excel from birthdayApr 17, 2025 am 09:47 AM
How to calculate age in Excel from birthdayApr 17, 2025 am 09:47 AMThe tutorial shows different ways to get age from birthday in Excel. You will learn a handful of formulas to calculate age as a number of complete years, get exact age in years, months and days at today's date or a particular date. There
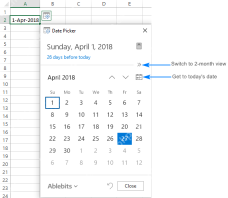 How to insert calendar in Excel (Date Picker & printable calendar template)Apr 17, 2025 am 09:07 AM
How to insert calendar in Excel (Date Picker & printable calendar template)Apr 17, 2025 am 09:07 AMThis tutorial demonstrates how to add a drop-down calendar (date picker) to Excel and link it to a cell. It also shows how to quickly create a printable calendar using an Excel template. Data integrity is a major concern in large or shared spreadshe
 Why You Should Always Rename Worksheets in ExcelApr 17, 2025 am 12:56 AM
Why You Should Always Rename Worksheets in ExcelApr 17, 2025 am 12:56 AMImprove Excel’s productivity: A guide to efficient naming worksheets This article will guide you on how to effectively name Excel worksheets, improve productivity and enhance accessibility. Clear worksheet names significantly improve navigation, organization, and cross-table references. Why rename Excel worksheets? Using the default "Sheet1", "Sheet2" and other names is inefficient, especially in files containing multiple worksheets. Clearer names like “Dashboard,” “Sales,” and “Forecasts,” give you and others a clear picture of the workbook content and quickly find the worksheets you need. Use descriptive names (such as "Dashboard", "Sales", "Forecast")
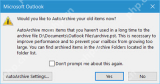 How to archive in Outlook automatically or manuallyApr 16, 2025 am 11:48 AM
How to archive in Outlook automatically or manuallyApr 16, 2025 am 11:48 AMThis comprehensive guide explains how to effectively manage your Outlook email storage by archiving emails, tasks, and other items across various Outlook versions (365, 2021, 2019, 2016, 2013, and earlier). Learn to configure automatic archiving, pe
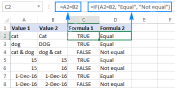 Excel: Compare strings in two cells for matches (case-insensitive or exact)Apr 16, 2025 am 11:26 AM
Excel: Compare strings in two cells for matches (case-insensitive or exact)Apr 16, 2025 am 11:26 AMThe tutorial shows how to compare text strings in Excel for case-insensitive and exact match. You will learn a number of formulas to compare two cells by their values, string length, or the number of occurrences of a specific character, a


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

AI Hentai Generator
Generate AI Hentai for free.

Hot Article

Hot Tools

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

SublimeText3 Chinese version
Chinese version, very easy to use

SublimeText3 Linux new version
SublimeText3 Linux latest version

Zend Studio 13.0.1
Powerful PHP integrated development environment





