In the WPS table, if you need to arrange the text vertically, you can do it through simple operations. First, select the text that needs to be arranged vertically in the table, then click the "Home" tab, find the "Text Direction" option in the "Arrangement" group, and select "Vertical Text" to achieve the effect of vertical text arrangement. In this way, you can easily arrange the text in the table vertically, making the layout more flexible and diverse. Hope the above method can help you.
First, open wps and create a new table document. Click the "Plus" sign on the menu bar, then select "Tables" and then click the "New Blank Document" button. This operation is similar to the part marked with a red circle in the picture below.

#2. Then, we enter text on the edge of the cell. Here we can see that the default input text is horizontal, as shown in the red circle in the figure below:

#3. If you want to change the horizontal text to vertical text, select the cell, right-click the mouse and select [Format Cells], and a pop-up box will pop up. As shown in the red circle in the picture below:

4. Select the [Align] button above. There is a [Vertical Text] style in the alignment. Change the previous selection Check the box and click the [OK] button, as shown in the red circle in the figure below:

5. Finally, we can see that the horizontal text becomes It is arranged vertically, as shown by the red arrow in the figure below:

#WPS table text vertical arrangement only takes 5 simple steps to complete. Isn’t it very simple? We can clearly see the comparison between the front and rear settings. This depends on personal preference. If you like the vertical arrangement, just set it to the vertical arrangement. If you don't like it, just set it to the horizontal arrangement.
The above is the detailed content of How to make WPS table text vertical. For more information, please follow other related articles on the PHP Chinese website!
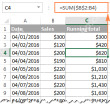 How to do a running total in Excel (Cumulative Sum formula)Apr 21, 2025 am 11:16 AM
How to do a running total in Excel (Cumulative Sum formula)Apr 21, 2025 am 11:16 AMThis concise guide demonstrates how to efficiently calculate running totals (cumulative sums) in Excel using a SUM formula with strategically placed absolute and relative cell references. A running total displays the accumulated sum of a dataset as
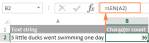 Excel LEN function: count characters in cellApr 21, 2025 am 10:10 AM
Excel LEN function: count characters in cellApr 21, 2025 am 10:10 AMAre you looking for an Excel formula to count characters in a cell? If so, then you have certainly landed up on the right page. This short tutorial will teach you how you can use the LEN function to count characters in Excel, with or with
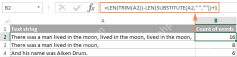 How to count words in Excel - formula examplesApr 21, 2025 am 09:59 AM
How to count words in Excel - formula examplesApr 21, 2025 am 09:59 AMThis tutorial demonstrates how to count words in Excel using a combination of the LEN, SUBSTITUTE, and TRIM functions. It offers both case-sensitive and case-insensitive formulas for counting total words or specific words/text within a cell or range
 Excel: Split string by delimiter or pattern, separate text and numbersApr 21, 2025 am 09:19 AM
Excel: Split string by delimiter or pattern, separate text and numbersApr 21, 2025 am 09:19 AMThis tutorial demonstrates how to efficiently split cells in Excel using both formulas and the advanced "Split Text" feature. Learn to separate text using commas, spaces, or any delimiter, and to split alphanumeric strings into their text
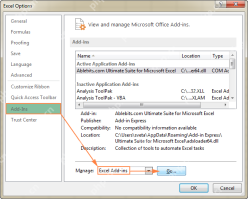 Excel Solver tutorial with step-by-step examplesApr 21, 2025 am 09:15 AM
Excel Solver tutorial with step-by-step examplesApr 21, 2025 am 09:15 AMThis tutorial explains how to locate and utilize the Solver add-in within various Excel versions, ranging from 2003 to 365. Step-by-step instructions and practical examples demonstrate Solver's application in optimizing solutions for linear programm
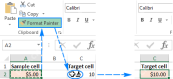 Excel Format Painter and other ways to copy formattingApr 20, 2025 am 10:29 AM
Excel Format Painter and other ways to copy formattingApr 20, 2025 am 10:29 AMThis tutorial demonstrates three efficient methods for copying formatting in Excel: Format Painter, Fill Handle, and Paste Special. These techniques are compatible with all Excel versions (2007-365). Proper formatting enhances worksheet presentation
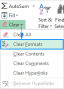 Clear formatting in Excel: how to remove all formats in a cellApr 20, 2025 am 10:12 AM
Clear formatting in Excel: how to remove all formats in a cellApr 20, 2025 am 10:12 AMThis tutorial offers two efficient methods for removing formatting from Excel spreadsheets. Dealing with extensive formatting in large spreadsheets can be cumbersome. These techniques streamline the process. Manually removing formatting is ineffici
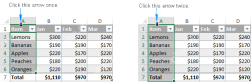 Excel table: comprehensive tutorial with examplesApr 20, 2025 am 09:48 AM
Excel table: comprehensive tutorial with examplesApr 20, 2025 am 09:48 AMThis tutorial unveils the power of Excel tables, often overlooked yet incredibly efficient tools for data management. Discover how tables simplify tasks like dynamic named ranges, formula updates, and data formatting, saving you significant time and


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.





