php editor Xiaoxin brings a guide on "disguising mac address to connect to WiFi". In some cases, we may need to spoof the device's MAC address to connect to the WiFi network. This technique can help us bypass some restrictions or improve network security. Next, we will introduce in detail how to achieve this operation so that you can easily master it.
The school restricts wifi connections through mac. How can the computer disguise the mac of the mobile phone?
Currently, most mobile phones use random MAC addresses by default. If the router at home is not set up to prevent others from connecting to the network, , you can keep your phone using the default random MAC address.
How to remove the WIFI speed limit of the wireless router: After connecting to the wifi network, use a computer browser to enter the gateway IP address on the nameplate on the back of the router (usually 192.168.1.1), and then enter the gateway configuration interface.
According to the current level of technology, it is impossible to crack WPA encryption (the encryption method used by almost all Wi-Fi networks). WPA encryption is highly secure. Even if the password is cracked, the network administrator may enable MAC address filtering, further increasing the difficulty of intrusion.
After searching various tutorials and experiences, I also used the same method to solve this problem.
I have successfully connected to the school’s Wi-Fi. This Wi-Fi does not have MAC filtering or binding set up.

How to connect a Mac computer to a WiFi network
1. According to Baidu’s experience, the steps for connecting an Apple notebook to WiFi are shown: Click the Network option to enter the system preferences of the Mac computer. Click on the network option inside the interface. Click to turn on wifi and then select and click on the turn on wifi function button in the network interface.
2. In the top column, on the right side, click the Wi-Fi button. If WiFi is off (Turn Wi-Fi Off), turn it on. Select your wireless network and click on it.
In order to connect to wireless WiFi, you first need to open System Preferences. On an Apple computer, you can click the Apple icon in the upper left corner of the screen and select System Preferences, or use the shortcut Command key to quickly open System Preferences.
How to crack the router restriction mac
One method is to statically bind through the router. You can log in to the router's background management interface, and then turn off the "Router DHCP Dynamic Allocation Function" in the "DHCP Server" tab. Then switch to the "Static Address Reservation" tab and click the "Add New Entry" button to set up static binding.
2. The system is connected to wifi. Open your computer browser, enter the gateway IP address on the nameplate on the back of the router (usually 19161), and enter the gateway configuration interface. Enter the DHCP client interface and view the host name. Record the licensed device hostname and its MAC address.
3. If the router specifies a certain MAC address and does not allow access to the Internet, you can manually change the MAC address of your own network card.
4. Method 1: Unrestrict your computer after entering the router; Method 2: Reset the router; Method 3: If the router blocks the IP, you can change the computer IP; Method 4: If If the router blocks Mac, you can change the computer’s Mac address.
5. If you are sure that the Internet account and password are correct, it is because the broadband network limits the number of computers that the router can use. This can be solved. The problem can be solved by setting up the router. The principles of each router are similar, and the specific requirements are Routing settings.
6. Method to solve the problem of broadband client restricting router sharing Internet access - mac address cloning. Method 1: First make sure that the computer applying for Internet access can already access the Internet in a stand-alone state. This means that the mac address of the computer's network card is a legal mac address.
How to use a mobile phone to break through other people's mac address binding and use other people's wifi to access the Internet
1. You can use other people's WIFI to access the Internet. The cracking method is nothing more than opening the mobile data and then opening the master key, etc. Network cracking APP. But if the other party turns on the background query and filters your MAC address, then you will not be able to use other people's WIFI in the future.
2. According to the current technical level, it is impossible to crack the WPA encryption method (the encryption method used by almost all Wi-Fi networks). WPA encryption is highly secure. Even if the password is cracked, the network administrator may enable MAC address filtering, further increasing the difficulty of intrusion.
3. Please update to the latest ColorOS 11 or above system. In the WiFi connection interface, click the small exclamation point on the far right to enter WiFi details and select a random mac in the privacy option to randomly generate and Use a random mac. Note: This answer applies to all OPPO series models.
4. First, turn off the Wi-Fi on your phone, and enter [*#*#3646633#*#*] on the phone’s “Dial” interface to enter the phone’s “Engineering Mode” interface. After entering the "Engineering Mode" interface of the mobile phone, switch to the "Connectivity" tab and click the "WiFi" item to enter the detailed settings interface.
5. The first is to only allow the mac addresses bound in the list to access the Internet through the router; in this case, you cannot access the Internet even if you know the password if you are not in the category of binding other people's mac addresses.
6. The computer can be changed, but the mobile phone is not very clear, but Baidu search: There are corresponding posts about changing the mac address of android mobile phones. You can see if it can be achieved.
Conclusion: The above is all the content about camouflaging mac to connect to wifi compiled by this site. Thank you for taking the time to read the content of this site. I hope it will be helpful to you. For more related content, don’t forget to check out Search this site.
The above is the detailed content of Pretend mac connects to wifi?. For more information, please follow other related articles on the PHP Chinese website!
 How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AM
How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AMThe MacOS Sequoia public beta program is now available, providing Mac users with an early chance to explore the new major MacOS system software update. However, it's important to note that, like all beta versions, MacOS Sequoia public beta may be mor
 How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AM
How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AMInterested in running Ubuntu Linux on your Apple Silicon Mac? It's now simpler than ever to run Ubuntu alongside MacOS without the hassle of partitioning, dual booting, or risking your Mac's operating system. Thanks to virtual machine technology, you
 How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AM
How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AMThere are multiple methods to track CPU usage on a Mac, with the most popular being Activity Monitor for the graphical interface and htop or top for command line users. While Activity Monitor can display an optional core graph and htop shows CPU core
 chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AM
chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AMSome Mac users occasionally find that the "chronod" process in MacOS either consumes a lot of system resources or requests access to a network connection. Sometimes, chronods are also marked by overly alert antivirus applications. While many people will ignore this situation, there are also curious Mac users who actively explore what specific processes that consume a lot of resources are, or what the intentions are of a process that requires or requires Internet access. So, what is chronod on Mac? Why does it use high CPU and system resources? Why does it require network access? Let's dive into the chronod process to better understand its functionality. What is chronod? The chronod process is
 Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AM
Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AMWhat is Security Agent on MacSecurity Agent on Mac functions as a background process responsible for managing user authentication, system security notifications, and requests for application permissions. It collaborates with macOS's Security Server t
 2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AM
2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AMHex editors are specialized software tools designed for viewing and editing hexadecimal data as well as raw binary data within files. These tools are indispensable for programmers, developers, and reverse engineers who need to inspect, debug, and ana
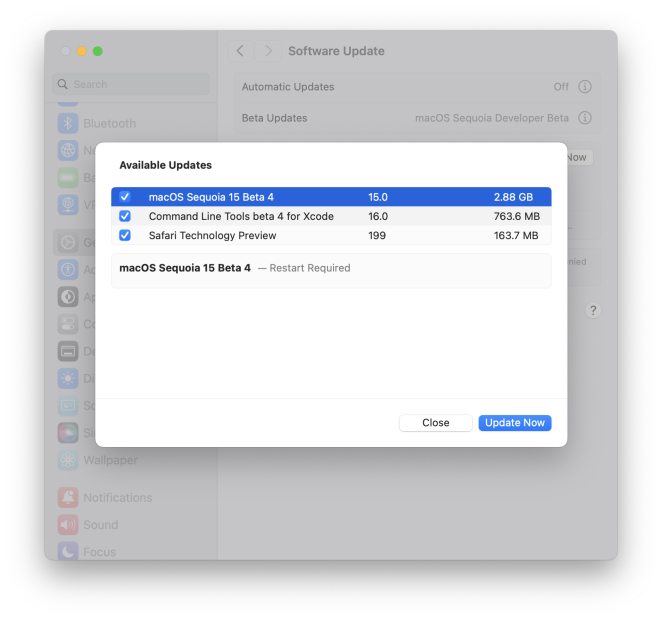 MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AM
MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AMApple has unveiled the fourth beta release of MacOS Sequoia 15 for those engaged in the macOS Sequoia developer beta testing program. Typically, the corresponding build for public beta testers, labeled as macOS Sequoia public beta 2, is released shor
 FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AM
FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AMApple's FaceTime application is designed to connect Apple users seamlessly, offering features such as dual-camera support on smartphones for enhanced video chat experiences.Occasionally, though, FaceTime might not function as intended. This article d


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver Mac version
Visual web development tools

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

Dreamweaver CS6
Visual web development tools







