What software is the MD5 value?
In the computer field, MD5 (Message Digest Algorithm 5) is a commonly used hash algorithm. It was designed in 1992 by American cryptography expert Ronald L. Rivest and officially released to the public in 1996. The MD5 algorithm is widely used in security applications such as data integrity verification, password storage, and identity authentication.
First, let’s take a brief look at the hash algorithm. A hashing algorithm converts input data of arbitrary length into a fixed-length output, often called a hash value or message digest. The hash algorithm has the following characteristics: any small change in the input data will result in a completely different output; the output length is fixed, no matter how long the input data is, the output hash value is always the same length; the hash value is irreversible, that is, it cannot pass the hash value. The hash value is calculated from the original input data.
The design goal of the MD5 algorithm is to produce a 128-bit hash value, usually expressed as a 32-bit hexadecimal number. It generates a fixed-length hash value by performing a series of bit operations and non-linear function operations on the input data. Since the principle and design of the algorithm are relatively simple, the calculation speed is fast.
However, due to the discovery of some security flaws in the MD5 algorithm, its use is no longer recommended in some specific scenarios. First, the MD5 algorithm is susceptible to collision attacks, where two different input data are found, but their hash values are the same. Second, rainbow table attacks on common passwords have become easier due to increased computing power.
Despite this, MD5 is still widely used in some asymmetric authentication scenarios, such as password storage and data integrity verification. In password storage, the user's password can be converted into a hash value and stored in the database using the MD5 algorithm. When a user logs in, the system will recalculate the hash value of the password entered by the user and compare it with the hash value in the database to verify the user's identity. In data integrity verification, the MD5 algorithm can be used to check whether any changes have occurred in the data during transmission or storage. As long as the hash value of the received data is the same as the expected hash value, the integrity of the data is guaranteed.
However, in scenarios such as password storage and data integrity verification, in order to increase security, more powerful hash algorithms are often used, such as SHA-256 (Secure Hash Algorithm 256-bit) or bcrypt, etc. . These algorithms typically have longer output lengths, producing more complex and more secure hashes for the same input.
In short, MD5 is a commonly used hash algorithm and is widely used in security applications such as data integrity verification, password storage, and authentication. Although it is no longer recommended in some specific scenarios, it still plays an important role in some situations. For more advanced security requirements, we should choose a more powerful hash algorithm to protect data security.
The above is the detailed content of What kind of software is MD5?. For more information, please follow other related articles on the PHP Chinese website!
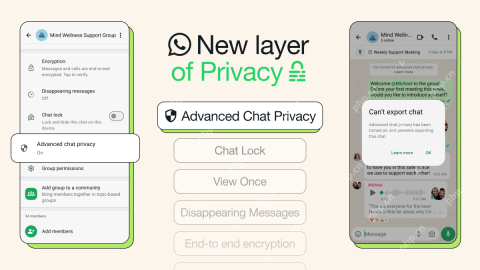 WhatsApp Now Lets You Block People From Exporting ChatsMay 08, 2025 am 10:40 AM
WhatsApp Now Lets You Block People From Exporting ChatsMay 08, 2025 am 10:40 AMWhatsApp enhances user privacy with its new "Advanced Chat Privacy" feature, rolling out globally. This update restricts others from exporting chats, automatically downloading media, and utilizing your messages for AI functionalities. How t
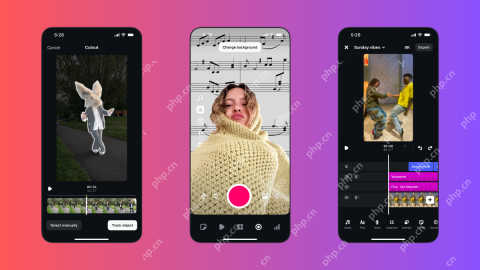 Instagram Just Launched Its Version of CapCutApr 30, 2025 am 10:25 AM
Instagram Just Launched Its Version of CapCutApr 30, 2025 am 10:25 AMInstagram officially launched the Edits video editing app to seize the mobile video editing market. The release has been three months since Instagram first announced the app, and two months after the original release date of Edits in February. Instagram challenges TikTok Instagram’s self-built video editor is of great significance. Instagram is no longer just an app to view photos and videos posted by individuals and companies: Instagram Reels is now its core feature. Short videos are popular all over the world (even LinkedIn has launched short video features), and Instagram is no exception
 Chess Lessons Are Coming to DuolingoApr 24, 2025 am 10:41 AM
Chess Lessons Are Coming to DuolingoApr 24, 2025 am 10:41 AMDuolingo, renowned for its language-learning platform, is expanding its offerings! Later this month, iOS users will gain access to new chess lessons integrated seamlessly into the familiar Duolingo interface. The lessons, designed for beginners, wi
 Blue Check Verification Is Coming to BlueskyApr 24, 2025 am 10:17 AM
Blue Check Verification Is Coming to BlueskyApr 24, 2025 am 10:17 AMBluesky Echoes Twitter's Past: Introducing Official Verification Bluesky, the decentralized social media platform, is mirroring Twitter's past by introducing an official verification process. This will supplement the existing self-verification optio
 Google Photos Now Lets You Convert Standard Photos to Ultra HDRApr 24, 2025 am 10:15 AM
Google Photos Now Lets You Convert Standard Photos to Ultra HDRApr 24, 2025 am 10:15 AMUltra HDR: Google Photos' New Image Enhancement Ultra HDR is a cutting-edge image format offering superior visual quality. Like standard HDR, it packs more data, resulting in brighter highlights, deeper shadows, and richer colors. The key differenc
 You Should Try Instagram's New 'Blend' Feature for a Custom Reels FeedApr 23, 2025 am 11:35 AM
You Should Try Instagram's New 'Blend' Feature for a Custom Reels FeedApr 23, 2025 am 11:35 AMInstagram and Spotify now offer personalized "Blend" features to enhance social sharing. Instagram's Blend, accessible only through the mobile app, creates custom daily Reels feeds for individual or group chats. Spotify's Blend mirrors th
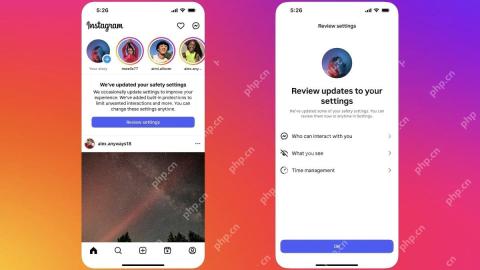 Instagram Is Using AI to Automatically Enroll Minors Into 'Teen Accounts'Apr 23, 2025 am 10:00 AM
Instagram Is Using AI to Automatically Enroll Minors Into 'Teen Accounts'Apr 23, 2025 am 10:00 AMMeta is cracking down on underage Instagram users. Following the introduction of "Teen Accounts" last year, featuring restrictions for users under 18, Meta has expanded these restrictions to Facebook and Messenger, and is now enhancing its
 Should I Use an Agent for Taobao?Apr 22, 2025 pm 12:04 PM
Should I Use an Agent for Taobao?Apr 22, 2025 pm 12:04 PMNavigating Taobao: Why a Taobao Agent Like BuckyDrop Is Essential for Global Shoppers The popularity of Taobao, a massive Chinese e-commerce platform, presents a challenge for non-Chinese speakers or those outside China. Language barriers, payment c


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

WebStorm Mac version
Useful JavaScript development tools

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function






