Using artificial intelligence to strengthen network security protection

Artificial intelligence holds great promise for protecting valuable and vulnerable data, but security teams face challenges in taking full advantage of it.
The value of data continues to increase and becomes the core of modern business, but it also faces the risk of more attacks. The proliferation of hybrid cloud and remote working gives bad actors more opportunities to attack. As a result, the threat landscape continues to evolve and regulation becomes more difficult.
As attack vectors continue to increase, managing huge amounts of information has also brought about the problem of data overload, adding greater pressure to the tense workforce. In addition, the introduction of new applications and IT infrastructure and skills shortages further complicate the situation. So it’s no surprise that in today’s digital-first world, security often fails to meet growing demands.
This requires IT managers to quickly find ways to integrate various different elements into a unified defense system. Fortunately, with next-generation artificial intelligence tools becoming widely available, IT managers can leverage this technology to combat potential attacks.
Complex Security Landscape
To more effectively monitor their IT security infrastructure and handle growing data volumes, organizations need a high degree of expertise and a significant investment of time. However, this often leaves organizations and IT leaders feeling at a disadvantage when facing attackers. Furthermore, due to the high diversity of the environment, many different security methods are employed. For example, securing an endpoint is completely different than securing an S3 bucket in the cloud. To solve these challenges, artificial intelligence technology emerged. By leveraging artificial intelligence, organizations can better respond to complex security threats and attacks, automatically monitor and analyze large amounts of security data, and detect abnormal behavior in a timely manner. The introduction of this technology will greatly improve the organization's security protection capabilities and enable it to respond to different types of security risks more quickly and accurately.
Traditional artificial intelligence is very effective at classification and is particularly useful for filtering and sorting events in different IT environments. In these environments, there will always be some activity that may be "bad," but 80% of it may be harmless. However, the opportunity for malicious activity is always present. No one wants to miss an attack or data-related issue, as this could result in everything being listed as critical. Fortunately, AI is good at ranking events from high to low priority, ensuring that actions and efforts can be focused where they are most urgently needed. Therefore, the application of traditional artificial intelligence in IT environments is of great significance.
With the application of generative artificial intelligence, we usher in another defense frontier. Leveraging natural language processing (NLP) technology can have a substantial impact on long-standing skills shortages. By translating security alerts into plain, understandable English, security teams receive timely, clear, and immediately actionable notifications.
Economic Pressures and Fast Action
Of course, security teams don’t want to be a hindrance to the organization, nor do they want to get in the way of business development plans. The fundamental question facing security leaders and their teams is “How do I move faster?” To achieve this, they must be able to gain insights from their IT environment quickly and accurately. Only in this way can we better defend against attacks.
Unfortunately, security teams cannot escape the impact the economic environment has on them. With limited resources, they are under pressure to do more. Therefore, they need to streamline operations and become more efficient. But this has become particularly difficult as the attack surface continues to expand and threat levels continue to increase.
AI-based security tools offer a way to help alleviate some of the stress, and more than half of executives (52%) already recognize that AI will help them better allocate resources, capabilities or skills. However, there is one hurdle to overcome. Essentially, security professionals don’t trust IT in general, and AI output is no exception. People will question the validity of the data it provides and the source of its insights. Without transparency, it’s difficult to build trust, so openness must be at the core of any AI implementation.
Assembling the most correct AI-based tools is not a one-time task. By 2025, AI security budgets are expected to increase 116% from 2021, as enterprises quickly and effectively protect today while planning for the future. Choosing the right technology partner will be a cornerstone of this strategy. Cybercriminals only have to get lucky once, but defenses must always work.
In short, the application of artificial intelligence (AI) in the field of network security has become a trend, which can enhance network security defense by improving detection accuracy, strengthening real-time response, and reducing false alarm rates. Here are some ways to use artificial intelligence to enhance network security defenses:
1. Threat detection and analysis:
Behavioral analysis: Use machine learning algorithms to analyze threats in the network Normal and abnormal behavior for timely detection of potential threats.
Anomaly detection: AI can quickly detect potential attacks by learning patterns of normal network activities and identifying abnormal activities that are inconsistent with these patterns.
2. Intrusion Detection System (IDS):
Deep learning: Using deep learning technology, complex intrusion behaviors, including unknown threats, can be detected more accurately.
Real-time monitoring: AI can monitor network traffic in real time, detect abnormal behaviors in time, and improve the speed of intrusion detection.
3. Automated response:
Intelligent countermeasures: AI can automatically identify and take countermeasures, such as blocking attackers, adjusting network configuration or isolating infected systems to mitigate the damage caused by attacks.
Automatic repair: AI can assist in automatically repairing systems under attack, reducing reliance on manual intervention.
4. Malware detection:
Feature analysis: Use AI to analyze the characteristics of malware to improve the accuracy of detection.
Behavioral Analysis: Behavioral analysis based on machine learning can detect malware variants, even if they have new characteristics.
5. User identity verification:
Biometric identification: Use artificial intelligence technology for biometric identification, such as fingerprints, iris scanning, etc., to strengthen the security of user identity verification sex.
Behavior Analysis: Use AI to analyze users’ normal behavior patterns to detect potential identity theft in a timely manner.
6. Data privacy protection:
Sensitive data monitoring: Use AI to monitor and identify sensitive data in the network, and promptly discover potential data leakage risks.
Encryption technology: AI can help improve and optimize encryption algorithms and improve the security of data transmission and storage.
Comprehensive use of artificial intelligence technology, network security defense systems can respond to various threats more intelligently and in real time, improving the level of network security. However, it should be noted that AI also faces some challenges in network security, such as combating adversarial attacks, privacy protection and other issues, so security and ethical issues need to be carefully considered in practical applications.
The above is the detailed content of Using artificial intelligence to strengthen network security protection. For more information, please follow other related articles on the PHP Chinese website!
 Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AM
Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AMSince 2008, I've championed the shared-ride van—initially dubbed the "robotjitney," later the "vansit"—as the future of urban transportation. I foresee these vehicles as the 21st century's next-generation transit solution, surpas
 Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AM
Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AMRevolutionizing the Checkout Experience Sam's Club's innovative "Just Go" system builds on its existing AI-powered "Scan & Go" technology, allowing members to scan purchases via the Sam's Club app during their shopping trip.
 Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AM
Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AMNvidia's Enhanced Predictability and New Product Lineup at GTC 2025 Nvidia, a key player in AI infrastructure, is focusing on increased predictability for its clients. This involves consistent product delivery, meeting performance expectations, and
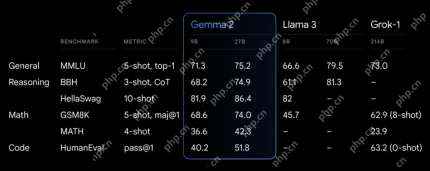 Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AM
Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AMGoogle's Gemma 2: A Powerful, Efficient Language Model Google's Gemma family of language models, celebrated for efficiency and performance, has expanded with the arrival of Gemma 2. This latest release comprises two models: a 27-billion parameter ver
 The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AM
The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AMThis Leading with Data episode features Dr. Kirk Borne, a leading data scientist, astrophysicist, and TEDx speaker. A renowned expert in big data, AI, and machine learning, Dr. Borne offers invaluable insights into the current state and future traje
 AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AM
AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AMThere were some very insightful perspectives in this speech—background information about engineering that showed us why artificial intelligence is so good at supporting people’s physical exercise. I will outline a core idea from each contributor’s perspective to demonstrate three design aspects that are an important part of our exploration of the application of artificial intelligence in sports. Edge devices and raw personal data This idea about artificial intelligence actually contains two components—one related to where we place large language models and the other is related to the differences between our human language and the language that our vital signs “express” when measured in real time. Alexander Amini knows a lot about running and tennis, but he still
 Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AM
Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AMCaterpillar's Chief Information Officer and Senior Vice President of IT, Jamie Engstrom, leads a global team of over 2,200 IT professionals across 28 countries. With 26 years at Caterpillar, including four and a half years in her current role, Engst
 New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AM
New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AMGoogle Photos' New Ultra HDR Tool: A Quick Guide Enhance your photos with Google Photos' new Ultra HDR tool, transforming standard images into vibrant, high-dynamic-range masterpieces. Ideal for social media, this tool boosts the impact of any photo,


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

Zend Studio 13.0.1
Powerful PHP integrated development environment

Notepad++7.3.1
Easy-to-use and free code editor

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.






