Types of privacy public chains and introduction to some important privacy public chains
For blockchain technology, expansion is no longer the only problem that needs to be solved. The next issue to be realized is privacy. This is also the main reason why the blockchain privacy track has become a hot topic. The current public chain applications are Privacy chain technology is mainly zero-knowledge proof and fully homomorphic encryption. For investors, what are the public privacy chains that investors should know about? Only by seizing the privacy track can you earn your first pot of gold. Currently, the most popular privacy public chains include PlatON, Aleo, Aztec, SecrerNetwork, etc. Next, the editor will introduce to you some of the larger privacy public chains.

What are the public privacy chains?
The currently popular privacy public chains mainly include PlatON, Aleo, Aztec, Secrer Network, etc. The following is a detailed introduction to these public chains:
1, PlatON
PlatON is A project initiated and promoted by the LatticeX Foundation, which is committed to building the next generation Internet infrastructure protocol. The project is based on blockchain technology and supported by a privacy-preserving computing network. PlatON's goal is to protect data privacy, solve data compliance in artificial intelligence applications, and promote the development of smarter artificial intelligence applications.
2. Aleo
Aleo is a privacy-focused blockchain platform that uses zero-knowledge proofs to achieve private transactions and calculations. This way, users can conduct secure transactions without revealing any sensitive information.
3. Aztec
Aztec Network is the first privacy protocol on Ethereum to use ZK-Rollups technology. It provides users with privacy protection, achieved through a unique transaction structure. This architecture is similar to the UTXO model and utilizes ZK proofs to transfer asset ownership while protecting the identities of participants.
4.Secret Network
Secret Network is a blockchain network that focuses on privacy protection and is committed to providing users with a secure and private blockchain experience. By employing privacy smart contracts and privacy protection technology, the network protects users' privacy from being violated by ensuring complete confidentiality of transactions and data. Users can perform various privacy-sensitive operations on this network without worrying about the leakage of personal information. The goal of Secret Network is to provide users with a safe and private environment to enable
What does a private public chain mean?
Privacy public chain is a blockchain network that focuses on providing user transactions and data privacy protection. Different from ordinary public chains, privacy public chains are designed to protect users' identities and transaction information to ensure that operations on the chain are private and secure. Privacy public chains usually support user anonymity, making it difficult for users’ transactions on the chain to be traced to their specific identities.
Zero-knowledge proof is a cryptographic technique that can verify the authenticity of an assertion without revealing specific information. In privacy public chains, zero-knowledge proofs are used to ensure transaction validity while protecting the privacy of transaction details.
Some private public chains support confidential transactions, that is, when transactions are conducted on the chain, the transaction amount and related information are encrypted, making this information invisible to people outside the chain. Some privacy public chains have introduced secret contracts, allowing input and output privacy to be maintained during the execution of smart contracts.
The above is the detailed content of Types of privacy public chains and introduction to some important privacy public chains. For more information, please follow other related articles on the PHP Chinese website!
 Tokenized Treasuries Near $6B Milestone, Led by BlackRockApr 19, 2025 am 11:44 AM
Tokenized Treasuries Near $6B Milestone, Led by BlackRockApr 19, 2025 am 11:44 AMThe value of blockchain-based U.S. Treasuries is closing in on a new milestone, with total holdings approaching $6 billion.
 title: Canary Capital Is Launching a TRX-Tracking ETFApr 19, 2025 am 11:42 AM
title: Canary Capital Is Launching a TRX-Tracking ETFApr 19, 2025 am 11:42 AMCanary Capital is looking to launch an exchange-traded fund (ETF) tracking the price of Tron's native token, TRX, according to a filing.
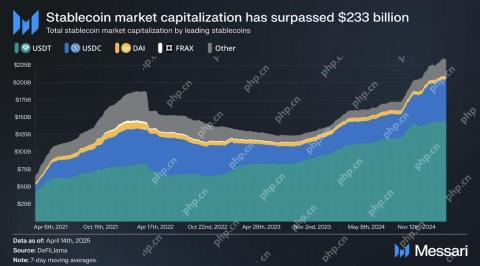 Solana Stablecoin Market Cap Hits Record $12.73 Billion as Sui Supply Reaches $800M with $60M InflowsApr 19, 2025 am 11:40 AM
Solana Stablecoin Market Cap Hits Record $12.73 Billion as Sui Supply Reaches $800M with $60M InflowsApr 19, 2025 am 11:40 AMThe stablecoin market has surpassed a total capitalization of $233 billion. Within this sector, Solana's stablecoins have reached a new all-time high market capitalization of $12.73 billion
 Canary Capital Files for Staking TRX ETF, Targeting Launch Before Spot Bitcoin ETFsApr 19, 2025 am 11:38 AM
Canary Capital Files for Staking TRX ETF, Targeting Launch Before Spot Bitcoin ETFsApr 19, 2025 am 11:38 AMCanary Capital is looking to get the U.S. Securities and Exchange Commission's sign-off for an exchange-traded fund that would track the Tron token TRX and has a staking component.
 MoonPay CEO Ivan Soto-Wright calls on US lawmakers to leave a path open to state-level regulators when passing legislation on stablecoinsApr 19, 2025 am 11:36 AM
MoonPay CEO Ivan Soto-Wright calls on US lawmakers to leave a path open to state-level regulators when passing legislation on stablecoinsApr 19, 2025 am 11:36 AMIn an April 18 X post, Soto-Wright said he wanted Congress to “keep state-regulated issuers in the game” when it comes to stablecoin regulation, referencing efforts in the House of Representatives and Senate to create a federal regulatory framework.
 Michael Saylor Dissects the Philosophy and Technological Potential of Bitcoin in '21 Truths of Bitcoin'Apr 19, 2025 am 11:34 AM
Michael Saylor Dissects the Philosophy and Technological Potential of Bitcoin in '21 Truths of Bitcoin'Apr 19, 2025 am 11:34 AMSaylor's ideas centre on the fixed 21 million coin supply of Bitcoin. He presents this shortage as a revolutionary economic idea rather than only a technical one.
 Official Trump (TRUMP) memecoin unlocked 40 million tokens, worth around $300 millionApr 19, 2025 am 11:32 AM
Official Trump (TRUMP) memecoin unlocked 40 million tokens, worth around $300 millionApr 19, 2025 am 11:32 AMThe TRUMP memecoin has gained significant popularity on the Solana network primarily due to its direct affiliation with the U.S. President Donald Trump.
 TRUMP (TRUMP) memecoin unlocks 40 million tokens, worth around $300 millionApr 19, 2025 am 11:30 AM
TRUMP (TRUMP) memecoin unlocks 40 million tokens, worth around $300 millionApr 19, 2025 am 11:30 AMThe TRUMP memecoin has gained significant popularity on the Solana network primarily due to its direct affiliation with the U.S. President Donald Trump.

Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 Chinese version
Chinese version, very easy to use

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

WebStorm Mac version
Useful JavaScript development tools

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.






