Basic steps to build a convolutional neural network using PyTorch

Convolutional neural network (CNN) is a deep learning model widely used in computer vision tasks. Compared with fully connected neural networks, CNN has fewer parameters and more powerful feature extraction capabilities, and performs well in tasks such as image classification, target detection, and image segmentation. Below we will introduce how to build a basic CNN model.
Convolutional Neural Network (CNN) is a deep learning model with multiple convolutional layers, pooling layers, activation functions and fully connected layers. The convolutional layer is the core component of CNN and is used to extract features of the input image. The pooling layer can reduce the size of the feature map and preserve the main features of the image. The activation function introduces nonlinear transformation to increase the expressive ability of the model. The fully connected layer converts the feature map into an output result. By combining these components, we can build a basic convolutional neural network. CNN performs well in tasks such as image classification, target detection, and image generation, and is widely used in the field of computer vision.
Secondly, for the structure of CNN, the parameters of each convolution layer and pooling layer need to be determined. These parameters include the size of the convolution kernel, the number of convolution kernels, and the size of the pooling kernel. At the same time, it is also necessary to determine the dimensions of the input data and the dimensions of the output data. The selection of these parameters usually needs to be determined experimentally. A common approach is to first build a simple CNN model and then gradually adjust the parameters until optimal performance is achieved.
When training a CNN model, we need to set the loss function and optimizer. Typically, the cross-entropy loss function is widely used, while the stochastic gradient descent optimizer is also a common choice. During the training process, we input the training data into the CNN model in batches and calculate the loss value based on the loss function. Then, use the optimizer to update the model parameters to reduce the loss value. Typically, multiple iterations are required to complete training, with each iteration batching training data into the model until a predetermined number of training epochs is reached or certain performance criteria are met.
The following is a code example for building a basic convolutional neural network (CNN) using PyTorch:
import torch
import torch.nn as nn
class Net(nn.Module):
def __init__(self):
super(Net, self).__init__()
self.conv1 = nn.Conv2d(3, 6, 5) # 3个输入通道,6个输出通道,5x5的卷积核
self.pool = nn.MaxPool2d(2, 2) # 2x2的最大池化层
self.conv2 = nn.Conv2d(6, 16, 5) # 6个输入通道,16个输出通道,5x5的卷积核
self.fc1 = nn.Linear(16 * 5 * 5, 120) # 全连接层1,输入大小为16x5x5,输出大小为120
self.fc2 = nn.Linear(120, 84) # 全连接层2,输入大小为120,输出大小为84
self.fc3 = nn.Linear(84, 10) # 全连接层3,输入大小为84,输出大小为10(10个类别)
def forward(self, x):
x = self.pool(torch.relu(self.conv1(x))) # 第一层卷积+激活函数+池化
x = self.pool(torch.relu(self.conv2(x))) # 第二层卷积+激活函数+池化
x = x.view(-1, 16 * 5 * 5) # 将特征图展开成一维向量
x = torch.relu(self.fc1(x)) # 第一层全连接+激活函数
x = torch.relu(self.fc2(x)) # 第二层全连接+激活函数
x = self.fc3(x) # 第三层全连接
return xThe above code defines a class named Net, inherited from nn.Module. This class contains convolutional layers, pooling layers and fully connected layers, as well as the forward method, which is used to define the forward propagation process of the model. In the __init__ method, we define two convolutional layers, three fully connected layers and a pooling layer. In the forward method, we call these layers in sequence and use the ReLU activation function to perform nonlinear transformation on the outputs of the convolutional layer and the fully connected layer. Finally, we return the output of the last fully connected layer as the model’s prediction. To add, the input of this CNN model should be a four-dimensional tensor with the shape of (batch_size, channels, height, width). Where batch_size is the batch size of the input data, channels is the number of channels of the input data, height and width are the height and width of the input data respectively. In this example, the input data should be an RGB color image with a channel count of 3.
The above is the detailed content of Basic steps to build a convolutional neural network using PyTorch. For more information, please follow other related articles on the PHP Chinese website!
 Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AM
Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AMSince 2008, I've championed the shared-ride van—initially dubbed the "robotjitney," later the "vansit"—as the future of urban transportation. I foresee these vehicles as the 21st century's next-generation transit solution, surpas
 Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AM
Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AMRevolutionizing the Checkout Experience Sam's Club's innovative "Just Go" system builds on its existing AI-powered "Scan & Go" technology, allowing members to scan purchases via the Sam's Club app during their shopping trip.
 Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AM
Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AMNvidia's Enhanced Predictability and New Product Lineup at GTC 2025 Nvidia, a key player in AI infrastructure, is focusing on increased predictability for its clients. This involves consistent product delivery, meeting performance expectations, and
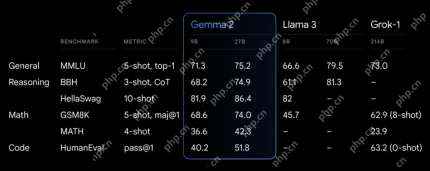 Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AM
Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AMGoogle's Gemma 2: A Powerful, Efficient Language Model Google's Gemma family of language models, celebrated for efficiency and performance, has expanded with the arrival of Gemma 2. This latest release comprises two models: a 27-billion parameter ver
 The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AM
The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AMThis Leading with Data episode features Dr. Kirk Borne, a leading data scientist, astrophysicist, and TEDx speaker. A renowned expert in big data, AI, and machine learning, Dr. Borne offers invaluable insights into the current state and future traje
 AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AM
AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AMThere were some very insightful perspectives in this speech—background information about engineering that showed us why artificial intelligence is so good at supporting people’s physical exercise. I will outline a core idea from each contributor’s perspective to demonstrate three design aspects that are an important part of our exploration of the application of artificial intelligence in sports. Edge devices and raw personal data This idea about artificial intelligence actually contains two components—one related to where we place large language models and the other is related to the differences between our human language and the language that our vital signs “express” when measured in real time. Alexander Amini knows a lot about running and tennis, but he still
 Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AM
Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AMCaterpillar's Chief Information Officer and Senior Vice President of IT, Jamie Engstrom, leads a global team of over 2,200 IT professionals across 28 countries. With 26 years at Caterpillar, including four and a half years in her current role, Engst
 New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AM
New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AMGoogle Photos' New Ultra HDR Tool: A Quick Guide Enhance your photos with Google Photos' new Ultra HDR tool, transforming standard images into vibrant, high-dynamic-range masterpieces. Ideal for social media, this tool boosts the impact of any photo,


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

Dreamweaver Mac version
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software





