
Rust is a systems-level programming language focused on safety, performance, and concurrency. It aims to provide a safe and reliable programming language suitable for scenarios such as operating systems, network applications, and embedded systems.
Rust's security mainly comes from two aspects: the ownership system and the borrow checker. The ownership system enables the compiler to check code for memory errors at compile time, thus avoiding common memory safety issues. By forcing checking of variable ownership transfers at compile time, Rust ensures that memory resources are properly managed and released. The borrow checker analyzes the life cycle of the variable to ensure that the same variable will not be accessed by multiple threads at the same time, thus avoiding common concurrency security issues. Through the combination of these two mechanisms, Rust can provide a highly secure programming environment and help developers write more reliable software.
Rust's performance mainly comes from two aspects: zero-cost abstraction and no garbage collection. Zero-cost abstraction means that Rust provides abstract features of high-level languages, such as generics and pattern matching, without negatively affecting the execution efficiency of the code. No garbage collection means that Rust can effectively manage memory and avoid the performance loss caused by garbage collection. These features make Rust a high-performance and safe programming language.
Now let’s see how to build a simple neural network using Rust.
First, we need to choose a neural network framework. In Rust, there are many excellent neural network frameworks to choose from, such as TensorFlow, PyTorch, Caffe, etc. But here, we decided to use rustlearn. rustlearn is a lightweight machine learning library focusing on linear algebra and statistical calculations.
Next, we need to define the structure of the neural network. In rustlearn, we can use a structure called NeuralNet to define neural networks. The code is as follows:
let mut net = NeuralNet::new(&[2, 3, 1]);
This example defines a three-layer neural network, with 2 neurons in the input layer, 3 neurons in the hidden layer, and 1 neuron in the output layer.
Then, we need to define the training data for the neural network. In this example, we use a simple logic gate dataset. The code is as follows:
let x = Array::from_vec(vec![vec![0., 0.], vec![0., 1.], vec![1., 0.], vec![1., 1.]]); let y = Array::from_vec(vec![vec![0.], vec![1.], vec![1.], vec![0.]]);
This example defines a training data set containing 4 samples, each sample contains 2 features and 1 label.
Finally, we can use the train method in rustlearn to train the neural network. The code is as follows:
net.train(&x, &y, SGD::default(), Loss::MSE, 1000);
This example uses the stochastic gradient descent algorithm (SGD) and the mean square error loss function (MSE) to train the neural network for 1,000 times.
The complete code is as follows:
use rustlearn::prelude::*;
use rustlearn::neural_network::{NeuralNet, SGD, Loss};
fn main() {
let mut net = NeuralNet::new(&[2, 3, 1]);
let x = Array::from_vec(vec![vec![0., 0.], vec![0., 1.], vec![1., 0.], vec![1., 1.]]);
let y = Array::from_vec(vec![vec![0.], vec![1.], vec![1.], vec![0.]]);
net.train(&x, &y, SGD::default(), Loss::MSE, 1000);
}The above is the detailed content of Steps to write a simple neural network using Rust. For more information, please follow other related articles on the PHP Chinese website!
 The Hidden Dangers Of AI Internal Deployment: Governance Gaps And Catastrophic RisksApr 28, 2025 am 11:12 AM
The Hidden Dangers Of AI Internal Deployment: Governance Gaps And Catastrophic RisksApr 28, 2025 am 11:12 AMThe unchecked internal deployment of advanced AI systems poses significant risks, according to a new report from Apollo Research. This lack of oversight, prevalent among major AI firms, allows for potential catastrophic outcomes, ranging from uncont
 Building The AI PolygraphApr 28, 2025 am 11:11 AM
Building The AI PolygraphApr 28, 2025 am 11:11 AMTraditional lie detectors are outdated. Relying on the pointer connected by the wristband, a lie detector that prints out the subject's vital signs and physical reactions is not accurate in identifying lies. This is why lie detection results are not usually adopted by the court, although it has led to many innocent people being jailed. In contrast, artificial intelligence is a powerful data engine, and its working principle is to observe all aspects. This means that scientists can apply artificial intelligence to applications seeking truth through a variety of ways. One approach is to analyze the vital sign responses of the person being interrogated like a lie detector, but with a more detailed and precise comparative analysis. Another approach is to use linguistic markup to analyze what people actually say and use logic and reasoning. As the saying goes, one lie breeds another lie, and eventually
 Is AI Cleared For Takeoff In The Aerospace Industry?Apr 28, 2025 am 11:10 AM
Is AI Cleared For Takeoff In The Aerospace Industry?Apr 28, 2025 am 11:10 AMThe aerospace industry, a pioneer of innovation, is leveraging AI to tackle its most intricate challenges. Modern aviation's increasing complexity necessitates AI's automation and real-time intelligence capabilities for enhanced safety, reduced oper
 Watching Beijing's Spring Robot RaceApr 28, 2025 am 11:09 AM
Watching Beijing's Spring Robot RaceApr 28, 2025 am 11:09 AMThe rapid development of robotics has brought us a fascinating case study. The N2 robot from Noetix weighs over 40 pounds and is 3 feet tall and is said to be able to backflip. Unitree's G1 robot weighs about twice the size of the N2 and is about 4 feet tall. There are also many smaller humanoid robots participating in the competition, and there is even a robot that is driven forward by a fan. Data interpretation The half marathon attracted more than 12,000 spectators, but only 21 humanoid robots participated. Although the government pointed out that the participating robots conducted "intensive training" before the competition, not all robots completed the entire competition. Champion - Tiangong Ult developed by Beijing Humanoid Robot Innovation Center
 The Mirror Trap: AI Ethics And The Collapse Of Human ImaginationApr 28, 2025 am 11:08 AM
The Mirror Trap: AI Ethics And The Collapse Of Human ImaginationApr 28, 2025 am 11:08 AMArtificial intelligence, in its current form, isn't truly intelligent; it's adept at mimicking and refining existing data. We're not creating artificial intelligence, but rather artificial inference—machines that process information, while humans su
 New Google Leak Reveals Handy Google Photos Feature UpdateApr 28, 2025 am 11:07 AM
New Google Leak Reveals Handy Google Photos Feature UpdateApr 28, 2025 am 11:07 AMA report found that an updated interface was hidden in the code for Google Photos Android version 7.26, and each time you view a photo, a row of newly detected face thumbnails are displayed at the bottom of the screen. The new facial thumbnails are missing name tags, so I suspect you need to click on them individually to see more information about each detected person. For now, this feature provides no information other than those people that Google Photos has found in your images. This feature is not available yet, so we don't know how Google will use it accurately. Google can use thumbnails to speed up finding more photos of selected people, or may be used for other purposes, such as selecting the individual to edit. Let's wait and see. As for now
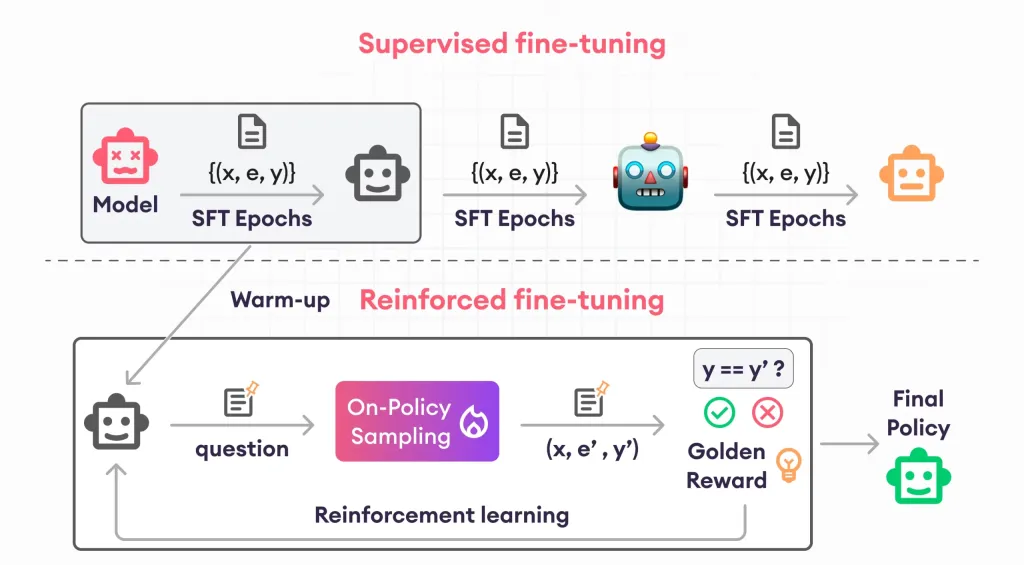 Guide to Reinforcement Finetuning - Analytics VidhyaApr 28, 2025 am 09:30 AM
Guide to Reinforcement Finetuning - Analytics VidhyaApr 28, 2025 am 09:30 AMReinforcement finetuning has shaken up AI development by teaching models to adjust based on human feedback. It blends supervised learning foundations with reward-based updates to make them safer, more accurate, and genuinely help
 Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AM
Let's Dance: Structured Movement To Fine-Tune Our Human Neural NetsApr 27, 2025 am 11:09 AMScientists have extensively studied human and simpler neural networks (like those in C. elegans) to understand their functionality. However, a crucial question arises: how do we adapt our own neural networks to work effectively alongside novel AI s


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

SublimeText3 Chinese version
Chinese version, very easy to use

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.






