 Technology peripherals
Technology peripherals AI
AI The significance and methods of tokenization, mapping and filling of text data for enhancement
The significance and methods of tokenization, mapping and filling of text data for enhancementThe significance and methods of tokenization, mapping and filling of text data for enhancement

In order to perform machine learning or natural language processing tasks, text needs to be converted into a numerical representation, which is called text data augmentation. Text data enhancement usually includes three steps: tokenization, mapping and filling.
1. Tokenization
Tokenization is the process of converting text into individual words or tokens. It divides text into independent words or tokens so that computers can understand and process it. During tokenization, we need to take into account various situations such as abbreviations, hyphens, numbers, and punctuation marks. Commonly used tokenization methods include space-delimited, character-delimited, regular expressions, and natural language toolkits such as NLTK and spaCy. These methods can select appropriate methods for tokenization based on specific needs and language characteristics. Tokenization is an important step in natural language processing, which provides the basis for subsequent text analysis and language model building.
2. Mapping
Mapping is the process of converting tokenized text into digital form. Through mapping, each word or token is given a unique numerical ID so that computers can process the text. Commonly used mapping methods include bag-of-words models, TF-IDF, and word embeddings. These methods help computers understand and analyze text data.
1) Bag of words model: Bag of words model is a common method to convert text into vector form. In the bag-of-words model, each word or token is considered a feature and the text is represented as a vector, where the value of each feature represents the number of times it occurs in the text. The bag-of-words model ignores the relationship and order between words.
2) TF-IDF: TF-IDF is an enhancement method based on the bag-of-word model, which takes into account the importance of words in the text. TF-IDF compares the frequency of a word with the frequency of the word in the entire corpus to determine the importance of the word in the text. TF-IDF can reduce the impact of common words on the text while increasing the weight of rare words.
3) Word embedding: Word embedding is a technique that maps words into a continuous vector space. By embedding words into vector space, the relationships and semantic information between words can be captured. Common word embedding algorithms include Word2Vec and GloVe.
3. Padding
Padding is the process of converting text to a fixed length. In machine learning models, a fixed-length vector is usually required as input, so the text needs to be padded to a fixed length. Commonly used filling methods include forward filling and backward filling.
Forward padding: In forward padding, text is added to the front of the vector to reach a fixed length. If the text is shorter than the fixed length, 0 is added to the front of the text until the fixed length is reached.
Backward padding: In backward padding, text is added to the back of the vector to a fixed length. If the text is shorter than the fixed length, 0 is added after the text until the fixed length is reached.
Overall, tokenization, mapping, and padding are important techniques for converting textual data into a numerical form that can be used for machine learning. These techniques not only allow machine learning algorithms to better understand text data, but also improve the accuracy and efficiency of the algorithms.
The above is the detailed content of The significance and methods of tokenization, mapping and filling of text data for enhancement. For more information, please follow other related articles on the PHP Chinese website!
 Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AM
Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AMSince 2008, I've championed the shared-ride van—initially dubbed the "robotjitney," later the "vansit"—as the future of urban transportation. I foresee these vehicles as the 21st century's next-generation transit solution, surpas
 Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AM
Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AMRevolutionizing the Checkout Experience Sam's Club's innovative "Just Go" system builds on its existing AI-powered "Scan & Go" technology, allowing members to scan purchases via the Sam's Club app during their shopping trip.
 Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AM
Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AMNvidia's Enhanced Predictability and New Product Lineup at GTC 2025 Nvidia, a key player in AI infrastructure, is focusing on increased predictability for its clients. This involves consistent product delivery, meeting performance expectations, and
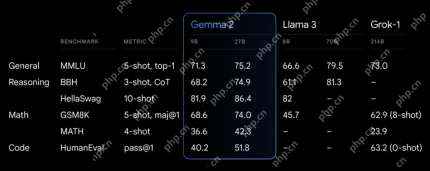 Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AM
Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AMGoogle's Gemma 2: A Powerful, Efficient Language Model Google's Gemma family of language models, celebrated for efficiency and performance, has expanded with the arrival of Gemma 2. This latest release comprises two models: a 27-billion parameter ver
 The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AM
The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AMThis Leading with Data episode features Dr. Kirk Borne, a leading data scientist, astrophysicist, and TEDx speaker. A renowned expert in big data, AI, and machine learning, Dr. Borne offers invaluable insights into the current state and future traje
 AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AM
AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AMThere were some very insightful perspectives in this speech—background information about engineering that showed us why artificial intelligence is so good at supporting people’s physical exercise. I will outline a core idea from each contributor’s perspective to demonstrate three design aspects that are an important part of our exploration of the application of artificial intelligence in sports. Edge devices and raw personal data This idea about artificial intelligence actually contains two components—one related to where we place large language models and the other is related to the differences between our human language and the language that our vital signs “express” when measured in real time. Alexander Amini knows a lot about running and tennis, but he still
 Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AM
Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AMCaterpillar's Chief Information Officer and Senior Vice President of IT, Jamie Engstrom, leads a global team of over 2,200 IT professionals across 28 countries. With 26 years at Caterpillar, including four and a half years in her current role, Engst
 New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AM
New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AMGoogle Photos' New Ultra HDR Tool: A Quick Guide Enhance your photos with Google Photos' new Ultra HDR tool, transforming standard images into vibrant, high-dynamic-range masterpieces. Ideal for social media, this tool boosts the impact of any photo,


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Atom editor mac version download
The most popular open source editor

SublimeText3 Linux new version
SublimeText3 Linux latest version

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

Zend Studio 13.0.1
Powerful PHP integrated development environment

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.




