Data security issues in artificial intelligence technology
Data security issues in artificial intelligence technology require specific code examples
With the rapid development of artificial intelligence technology, our lives have become more convenient, but at the same time There are also data security challenges. The core of artificial intelligence technology is data, and the large amount of data generated by people has become the target of hackers and criminals. In this article, we will explore data security issues in artificial intelligence technology and provide some concrete code examples to solve these problems.
1. Data leakage problem
Data leakage is one of the most common security issues in artificial intelligence technology. In the process of training the model, we need to use a large amount of data. However, this data may contain sensitive information such as personal privacy or business secrets. If this data is obtained by criminals, it will bring huge risks to individuals and organizations.
Solution: Encrypt data
An effective way to solve the problem of data leakage is to encrypt the data. The following is a code example that uses the symmetric encryption algorithm AES to encrypt data:
import javax.crypto.Cipher;
import javax.crypto.SecretKey;
import javax.crypto.spec.SecretKeySpec ;
public class EncryptionUtils {
private static final String ALGORITHM = "AES";
private static final String KEY = "mysecretkey";
public static byte[] encryptData(byte[] data) throws Exception {
SecretKey secretKey = new SecretKeySpec(KEY.getBytes(), ALGORITHM);
Cipher cipher = Cipher.getInstance(ALGORITHM);
cipher.init(Cipher.ENCRYPT_MODE, secretKey);
return cipher.doFinal(data);
}
public static byte[] decryptData(byte[] encryptedData) throws Exception {
SecretKey secretKey = new SecretKeySpec(KEY.getBytes(), ALGORITHM);
Cipher cipher = Cipher.getInstance(ALGORITHM);
cipher.init(Cipher.DECRYPT_MODE, secretKey);
return cipher.doFinal(encryptedData);
}}
Using the above code, we can encrypt and store sensitive data, and only authorized users can decrypt the data for use.
2. The problem of adversarial sample attack
An adversarial sample attack means that the attacker causes the intelligent system to misjudge by carefully designing the input data. This can cause AI systems to make incorrect decisions or ignore important safety issues. Adversarial sample attacks are an important challenge in current artificial intelligence technology.
Solution: Use adversarial sample detection algorithm
There are currently many adversarial sample detection algorithms that can deal with adversarial sample attacks. Here is a code example that uses a deep learning model to detect adversarial examples:
import tensorflow as tf
model = tf.keras.models.load_model('model.h5')
Load adversarial sample
adversarial_example = tf.load('adversarial_example.npy')
Determine whether the adversarial sample has been successfully detected
def detect_adversarial_example(example):
prediction = model.predict(example) return tf.math.argmax(prediction) == 0 # 假设模型的正常预测结果是0
print("Detection result:", detect_adversarial_example(adversarial_example))
In this code, we first load the previously trained deep learning model, and then pass in an adversarial sample to determine the Whether the sample was successfully tested.
3. Privacy Protection Issues
Another important data security issue in artificial intelligence technology is privacy protection. Many artificial intelligence applications need to process users' personal information, and this information often contains sensitive privacy content. Protecting user privacy has become an important issue in the development of artificial intelligence technology.
Solution: Use differential privacy technology
Differential privacy is a technology widely used in privacy protection. It makes it more difficult for attackers to obtain real data by introducing noise before processing sensitive data. The following is a code example that uses differential privacy technology to process data:
import numpy as np
import matplotlib.pyplot as plt
Generate sensitive data
sensitive_data = np .random.randint(0, 100, size=(1000,))
Add noise to data
epsilon = 0.1 # Privacy budget
noisy_data = np.random.laplace(scale =1.0 / epsilon, size=sensitive_data.shape)
protected_data = sensitive_data noisy_data
Show the difference between the data after adding noise and the original data
plt.plot(sensitive_data, label=' sensitive data')
plt.plot(protected_data, label='protected data')
plt.legend()
plt.show()
In the above code, we first generate some Sensitive data, then add Laplacian noise to the data to protect privacy, and draw a graph to show the difference between the data after adding the noise and the original data.
Conclusion
The development of artificial intelligence technology has brought us convenience, but at the same time it has also triggered a series of data security issues. When dealing with data in artificial intelligence technology, we should pay attention to issues such as data leakage, adversarial sample attacks, and privacy protection. This article provides some specific code examples to help resolve these issues. I hope this article can be helpful to readers on data security issues in artificial intelligence technology.
The above is the detailed content of Data security issues in artificial intelligence technology. For more information, please follow other related articles on the PHP Chinese website!
 AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AM
AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AMThere were some very insightful perspectives in this speech—background information about engineering that showed us why artificial intelligence is so good at supporting people’s physical exercise. I will outline a core idea from each contributor’s perspective to demonstrate three design aspects that are an important part of our exploration of the application of artificial intelligence in sports. Edge devices and raw personal data This idea about artificial intelligence actually contains two components—one related to where we place large language models and the other is related to the differences between our human language and the language that our vital signs “express” when measured in real time. Alexander Amini knows a lot about running and tennis, but he still
 Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AM
Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AMCaterpillar's Chief Information Officer and Senior Vice President of IT, Jamie Engstrom, leads a global team of over 2,200 IT professionals across 28 countries. With 26 years at Caterpillar, including four and a half years in her current role, Engst
 New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AM
New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AMGoogle Photos' New Ultra HDR Tool: A Quick Guide Enhance your photos with Google Photos' new Ultra HDR tool, transforming standard images into vibrant, high-dynamic-range masterpieces. Ideal for social media, this tool boosts the impact of any photo,
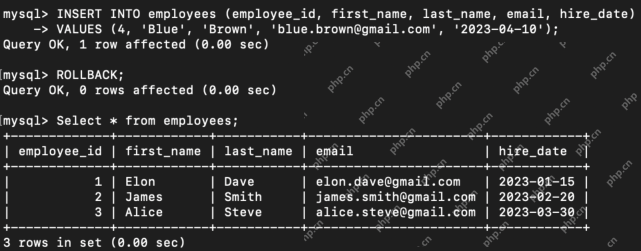 What are the TCL Commands in SQL? - Analytics VidhyaApr 22, 2025 am 11:07 AM
What are the TCL Commands in SQL? - Analytics VidhyaApr 22, 2025 am 11:07 AMIntroduction Transaction Control Language (TCL) commands are essential in SQL for managing changes made by Data Manipulation Language (DML) statements. These commands allow database administrators and users to control transaction processes, thereby
 How to Make Custom ChatGPT? - Analytics VidhyaApr 22, 2025 am 11:06 AM
How to Make Custom ChatGPT? - Analytics VidhyaApr 22, 2025 am 11:06 AMHarness the power of ChatGPT to create personalized AI assistants! This tutorial shows you how to build your own custom GPTs in five simple steps, even without coding skills. Key Features of Custom GPTs: Create personalized AI models for specific t
 Difference Between Method Overloading and OverridingApr 22, 2025 am 10:55 AM
Difference Between Method Overloading and OverridingApr 22, 2025 am 10:55 AMIntroduction Method overloading and overriding are core object-oriented programming (OOP) concepts crucial for writing flexible and efficient code, particularly in data-intensive fields like data science and AI. While similar in name, their mechanis
 Difference Between SQL Commit and SQL RollbackApr 22, 2025 am 10:49 AM
Difference Between SQL Commit and SQL RollbackApr 22, 2025 am 10:49 AMIntroduction Efficient database management hinges on skillful transaction handling. Structured Query Language (SQL) provides powerful tools for this, offering commands to maintain data integrity and consistency. COMMIT and ROLLBACK are central to t
 PySimpleGUI: Simplifying GUI Development in Python - Analytics VidhyaApr 22, 2025 am 10:46 AM
PySimpleGUI: Simplifying GUI Development in Python - Analytics VidhyaApr 22, 2025 am 10:46 AMPython GUI Development Simplified with PySimpleGUI Developing user-friendly graphical interfaces (GUIs) in Python can be challenging. However, PySimpleGUI offers a streamlined and accessible solution. This article explores PySimpleGUI's core functio


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 English version
Recommended: Win version, supports code prompts!

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

SublimeText3 Mac version
God-level code editing software (SublimeText3)

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

Atom editor mac version download
The most popular open source editor






