The best way to protect data transmission
In today's interconnected global marketplace, secure data transmission is more important than ever. As digital platforms become increasingly important for financial transactions and personal communications, ensuring the integrity and confidentiality of data is critical. If someone accesses the data without authorization, that's not good. If someone accesses the data without authorization, that's not good. It can cost a company money, ruin its reputation, and cause customers to lose trust. This article explores best practices for ensuring secure data transmission, providing valuable insights for anyone involved in online activities, whether a multinational company or an individual consumer.
Why secure data transmission is important
The importance of secure data transmission goes beyond just preventing sensitive information from falling into the wrong hands. It is the cornerstone of business integrity and the key to gaining competitive advantage in a rapidly evolving digital environment. As companies expand their operations globally, they often exchange data between different agencies, each with their own regulations and potential vulnerabilities. Secure data transfer is about more than just preventing financial losses from fraud or data theft; it's also about regulatory compliance, protecting intellectual property and maintaining customer trust. Businesses that are perceived as safe are more likely to attract customer engagement, and this perception directly affects a company's bottom line. In an era where data breaches are becoming increasingly common and costly,
Understand Data Encryption
Data encryption is the cornerstone of secure data transmission. Comprehensible data is converted into an incomprehensible format that can only be decrypted by an authorized individual using the correct "key" through encryption. There are many encryption methods, including symmetric and asymmetric algorithms. Using the same key to encrypt and decrypt data is faster, but may be less secure if compromised, which is a characteristic of symmetric encryption. On the other hand, a pair of keys is used for decryption and encryption - the public key is used to encrypt the data, and the private key is used to decrypt - adding an extra layer of security, which is a feature of asymmetric encryption. The choice between these approaches often depends on the specific needs of the business and the complexity of its operations. Understanding data encryption is more than a technical exercise; This is a strategic task for any company operating in global markets. Adequately implemented encryption protocols prevent unauthorized data interception, ensuring regulatory compliance and preventing malicious attacks.
The role of virtual private network
Virtual private networks can significantly ensure the security of data transmission, especially in global markets where data is often transmitted across different networks and institutions. Virtual Private Network Establishes a secure tunnel for transmitting data over the Internet, preventing unauthorized access or tampering. It encrypts your internet traffic, masks your IP address, and effectively protects your activity from prying eyes. For businesses, using a virtual private network adds an extra layer of security that is critical to protecting sensitive information and complying with data protection laws. In an increasingly connected world, virtual private networks are critical to a strong data security strategy.
The Importance of Secure Sockets Layer (SSL) and Transport Layer Security (TLS)
TLS and SSL are encryption protocols that secure data transmission over the Internet. They are most easily recognized in the context of HTTPS sites, represented by the padlock symbol in the URL bar. SSL and TLS encrypt data packets between the web browser and the server, ensuring that any sensitive information such as credit card details, personally identifiable or proprietary business data is protected from unauthorized access or tampering. For businesses operating in global markets, adopting SSL/TLS is not just a best practice; This is critical to maintaining customer trust and complying with regulations.
EDI Compliance and What It Means
EDI compliance refers to compliance with proven Electronic Data Interchange (EDI) standards and protocols. Businesses can use the system to exchange documents in a standardized electronic format. This ensures efficient and streamlined communication between different parties. In secure data transmission, EDI compliance is especially important for companies operating in global markets. EDI standards ensure smooth transactions, reduce human error and increase efficiency. Additionally, compliance with EDI standards often means adhering to specific security measures, such as encryption and secure channels for data transmission, thereby enhancing the overall integrity and security of the data being exchanged.
Multi-Factor Authentication (MFA)
This requires multiple forms of identification to gain access to an account or system. In addition to something you know (like a password), MFA often involves something you have (like a mobile device), a verification code, or something that is you (like a fingerprint). Implementing MFA is critical to protecting data transfers in global markets. Adding additional layers of security can significantly make it more difficult for unauthorized users to access sensitive data. MFA is highly effective at blocking cyberattacks such as phishing and credential stuffing, making it a best practice for enterprises that prioritize secure data transfer.
Secure File Transfer Protocol (SFTP and FTPS)
Secure file transfer protocols such as SFTP (Secure File Transfer Protocol) and FTPS (Secure FTP) are important tools for securely transferring data over the network. SFTP encrypts commands and data, effectively preventing common network threats such as data interception and unauthorized data access. However, FTPS uses SSL (Secure Socket Layer) encryption to secure the data channel. Both are significant upgrades from traditional, unencrypted FTP. For businesses operating in global markets, using SFTP or FTPS is critical as a data breach can have serious consequences. These protocols ensure that files containing sensitive information reach their intended destination safely.
Legal Compliance and Global Regulations
Adhering to legal compliance and global regulations is a business imperative and not just a matter of good governance. Laws such as Europe's GDPR (General Data Protection Regulation) and California's CCPA set strict data protection standards. Not only can failure to comply result in hefty fines, but it can also damage a company's reputation. These laws often mandate secure data transfer protocols, making them critical to global business operations.
Conclusion
In an increasingly interconnected global market, the importance of secure data transmission cannot be overstated. Businesses must remain vigilant, from understanding the nuances of data encryption to implementing advanced measures like virtual private networks and multi-factor authentication. Given the critical role of EDI compliance and compliance with international data protection laws, companies must be bold in developing data security strategies. Ignoring these best practices can result in financial and reputational damage that is difficult, if not impossible, to recover. Taking a comprehensive approach to protecting data in transit is more than just innovative business; This is a non-negotiable necessity.
The above is the detailed content of The best way to protect data transmission. For more information, please follow other related articles on the PHP Chinese website!
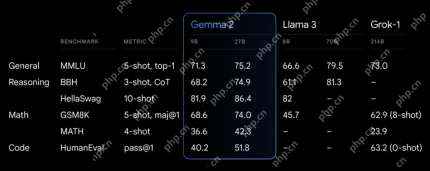 Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AM
Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AMGoogle's Gemma 2: A Powerful, Efficient Language Model Google's Gemma family of language models, celebrated for efficiency and performance, has expanded with the arrival of Gemma 2. This latest release comprises two models: a 27-billion parameter ver
 The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AM
The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AMThis Leading with Data episode features Dr. Kirk Borne, a leading data scientist, astrophysicist, and TEDx speaker. A renowned expert in big data, AI, and machine learning, Dr. Borne offers invaluable insights into the current state and future traje
 AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AM
AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AMThere were some very insightful perspectives in this speech—background information about engineering that showed us why artificial intelligence is so good at supporting people’s physical exercise. I will outline a core idea from each contributor’s perspective to demonstrate three design aspects that are an important part of our exploration of the application of artificial intelligence in sports. Edge devices and raw personal data This idea about artificial intelligence actually contains two components—one related to where we place large language models and the other is related to the differences between our human language and the language that our vital signs “express” when measured in real time. Alexander Amini knows a lot about running and tennis, but he still
 Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AM
Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AMCaterpillar's Chief Information Officer and Senior Vice President of IT, Jamie Engstrom, leads a global team of over 2,200 IT professionals across 28 countries. With 26 years at Caterpillar, including four and a half years in her current role, Engst
 New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AM
New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AMGoogle Photos' New Ultra HDR Tool: A Quick Guide Enhance your photos with Google Photos' new Ultra HDR tool, transforming standard images into vibrant, high-dynamic-range masterpieces. Ideal for social media, this tool boosts the impact of any photo,
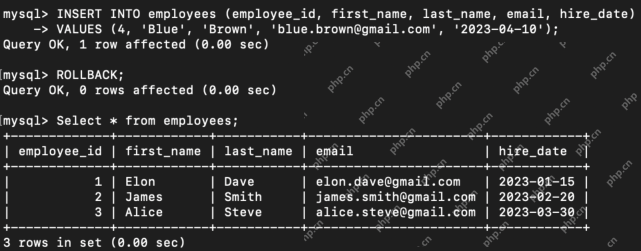 What are the TCL Commands in SQL? - Analytics VidhyaApr 22, 2025 am 11:07 AM
What are the TCL Commands in SQL? - Analytics VidhyaApr 22, 2025 am 11:07 AMIntroduction Transaction Control Language (TCL) commands are essential in SQL for managing changes made by Data Manipulation Language (DML) statements. These commands allow database administrators and users to control transaction processes, thereby
 How to Make Custom ChatGPT? - Analytics VidhyaApr 22, 2025 am 11:06 AM
How to Make Custom ChatGPT? - Analytics VidhyaApr 22, 2025 am 11:06 AMHarness the power of ChatGPT to create personalized AI assistants! This tutorial shows you how to build your own custom GPTs in five simple steps, even without coding skills. Key Features of Custom GPTs: Create personalized AI models for specific t
 Difference Between Method Overloading and OverridingApr 22, 2025 am 10:55 AM
Difference Between Method Overloading and OverridingApr 22, 2025 am 10:55 AMIntroduction Method overloading and overriding are core object-oriented programming (OOP) concepts crucial for writing flexible and efficient code, particularly in data-intensive fields like data science and AI. While similar in name, their mechanis


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SublimeText3 English version
Recommended: Win version, supports code prompts!

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

SublimeText3 Mac version
God-level code editing software (SublimeText3)

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

Atom editor mac version download
The most popular open source editor






