Home >Operation and Maintenance >Safety >How to implement APT34 leaked weapon report analysis
How to implement APT34 leaked weapon report analysis
- WBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBforward
- 2023-05-29 12:42:341701browse
APT34 is an APT organization from Iran. Since 2014, it has continued to launch APT attacks in the Middle East and Asia. The industries involved mainly include government, finance, energy, telecommunications, etc. The arsenal of attack weapons is constantly being upgraded, and attack methods are constantly being introduced. However, attackers will not stop their attacks just because they are exposed. This has been going on for many years.
APT34 Organization Background
On April 17, foreign media reported that a user named “Lab Dookhtegan” exposed attacks from the APT34 organization on Telegram. toolkit and some APT34 victim data were also exposed. This incident, like previous source code leaks, was extremely explosive. The APT34 organization has continued to launch multiple attacks on certain countries in the Middle East and Asia since at least 2014, targeting the government, finance, energy, telecommunications and other industries. The organization's targets are generally countries opposed to Iran, so some people speculate that the organization is a security department in Iran, or a security company that has long-term cooperation with the Iranian government. The organization is good at using social media, forging Internet accounts with various identities, and approaching attack targets through social engineering techniques. At the same time, the organization's attack arsenal is constantly upgrading, and its attack methods are becoming more and more sophisticated. They integrate attack methods such as spear phishing with new attack technologies to continuously expand the penetration scope of existing targets.

Exposed members of the APT34 organization
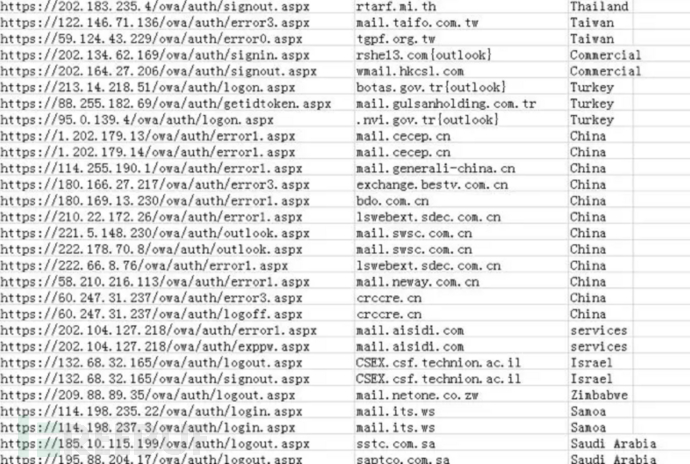
According to the leaked Webshell list, it is obvious that the organization has recently carried out large-scale attacks on China. This chart lists more than 10 websites labeled "China" that have been compromised, which can be used as evidence to support the argument for domestic attacks.
Lab Dookhtegan once claimed to expose the personal information of an organization member every few days, but now the accounts on Telegram and Twitter have been blocked.
Introduction to leaked tools
This source code leak includes a large number of important attack weapons commonly used by APT34 organizations, such as: Webshells_and_Panel, posion frog , Webmask, Glimpse. Dongxun Technology 2046Lab used the "Iron Dome Advanced Persistent Threat Warning System" to conduct threat detection on these attack weapons and conducted an in-depth analysis from the technical level.
Detection results
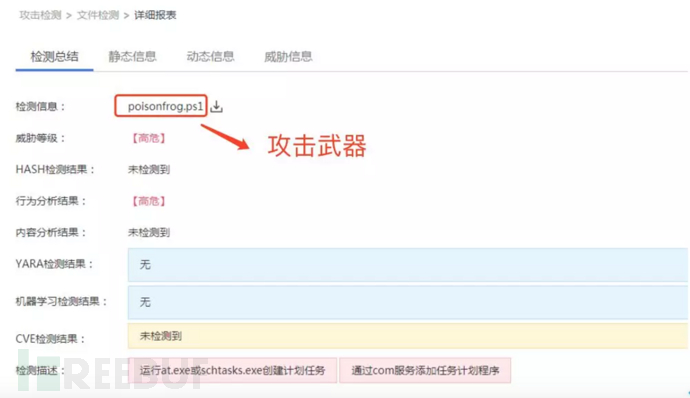
1. Webshell warning: [High risk]
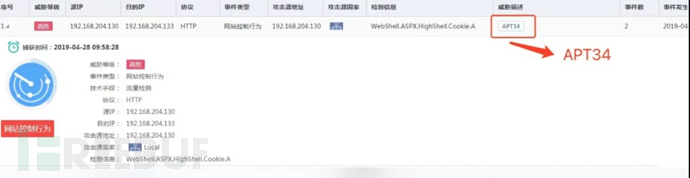
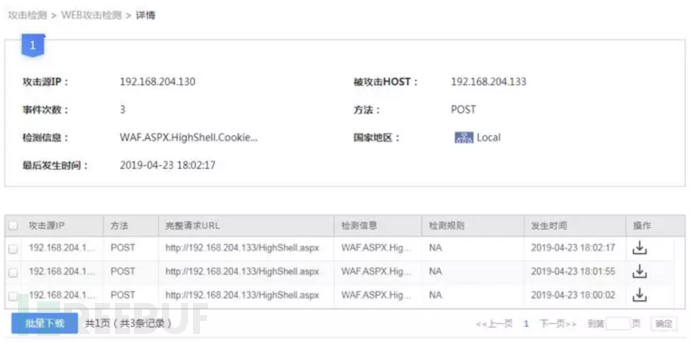
2. File sandbox detection warning : [High risk]
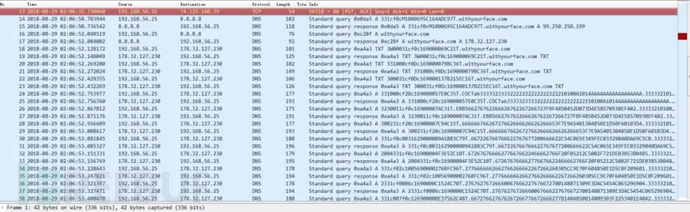
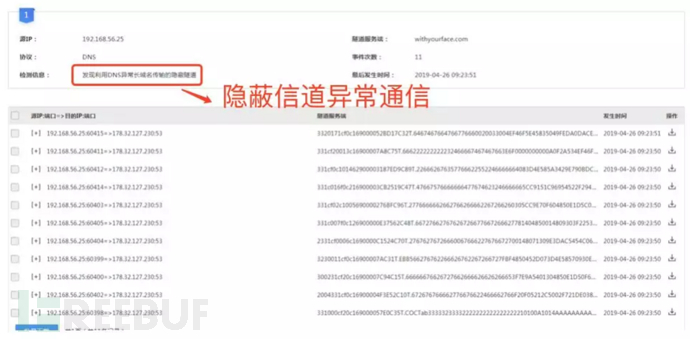
3. DNS covert channel detection warning: A covert tunnel using DNS to transmit abnormally long domain names was discovered
Analysis of attack weapons
1.Webshells_and_Panel
The Webshells_and_Panel directory mainly contains a variety of Webshell tools written in C#, and the Webshell directory contains two main files folders, respectively HighShell and HyperShell.
1.1 HighShell
There is only HighShell.aspx in the HighShell directory, which is a WebShell for Windows servers. The default interface after opening is as follows:

As can be seen from the above picture, this version is version 5.0, which has authentication, file upload, command execution, database operations, etc. Function.
To use this Webshell, you need to enter the connection password (Th!sN0tF0rFAN) in the red input box after the "Login" label and click the "Do it" button. When the input box turns green, you can use the Webshell to log in to the server. Carry out relevant operations. The following figure is an operation diagram for operating the "command" command and obtaining server information:

## 1.2 HyperShell
HyperShell is a A project with source code files, including multiple WebShell source code files. The following are several webshell functions that can be used.simple.aspx
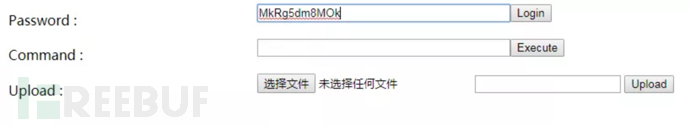
The simple webshell that includes authentication, command execution and file upload functions is simple.aspx. After opening, it will look as shown in the picture: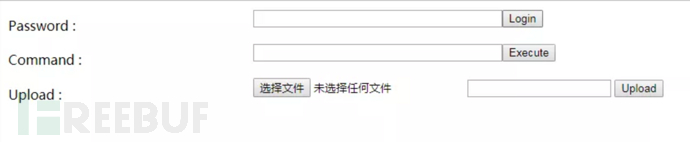 Enter the connection password (MkRg5dm8MOk) in the Password input box and click the "Login" button to control the server and upload files. The password connection is as shown below:
Enter the connection password (MkRg5dm8MOk) in the Password input box and click the "Login" button to control the server and upload files. The password connection is as shown below:
 The following picture is the operation diagram for operating the "command" command and obtaining the server information:
The following picture is the operation diagram for operating the "command" command and obtaining the server information: 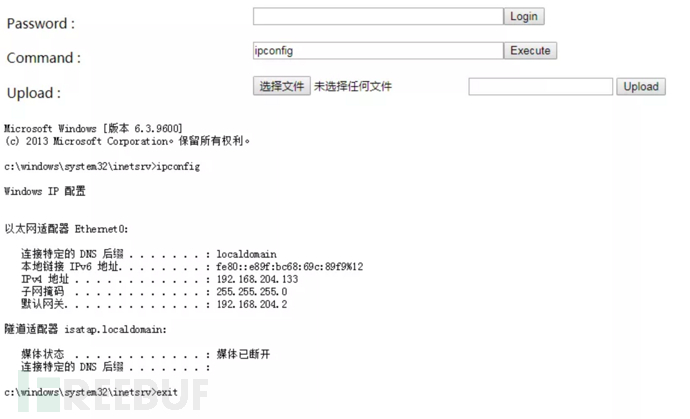
simpleDownload.aspx
simpleDownload.aspx has only one upload function, as shown below:
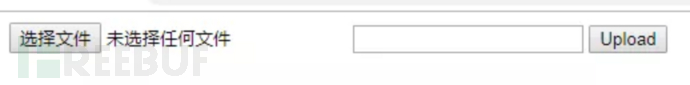
HighShelllocal.aspx
HighShelllocal. aspx is an upgraded version of HighShell. The version number is 8.6.2. The functions of this version are roughly the same as the independent version 5.0. The interface and functions are mainly optimized. The interface diagram is as follows:
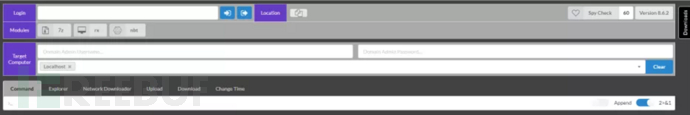
2.poison frog
2.1 Agent
2.1.1 poisonfrog.ps1
Poisonfrog.ps1 is the only file of Agent, which is used to plant backdoor programs on compromised hosts. After this file is run, three files, dUpdater.ps1, hUpdater.ps1 and UpdateTask.vbs, will be left in the C:\Users\Public\Public directory of the compromised host.
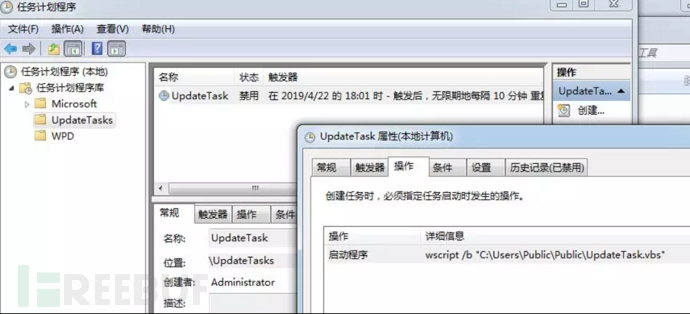
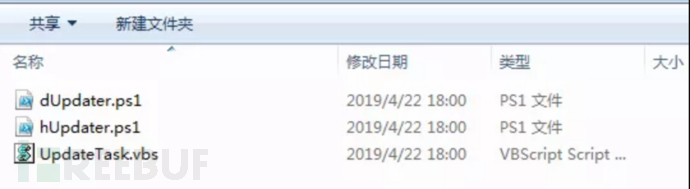 The backdoor program left on the host is the UpdateTask.vbs script, which is automatically run through scheduled tasks every 10 minutes. What it does is run two scripts: dUpdater.ps1 and hUpdater.ps1.
The backdoor program left on the host is the UpdateTask.vbs script, which is automatically run through scheduled tasks every 10 minutes. What it does is run two scripts: dUpdater.ps1 and hUpdater.ps1.
2.1.2 dUpdater.ps1
This script is a remote control script. It will generate a DNS domain name and connect to the control server, receive remote instructions from it, and Send and receive files. The DGA.Changer algorithm is used when generating DNS domain names to dynamically calculate server domain names. 2046Lab restored this DGA.Changer algorithm:
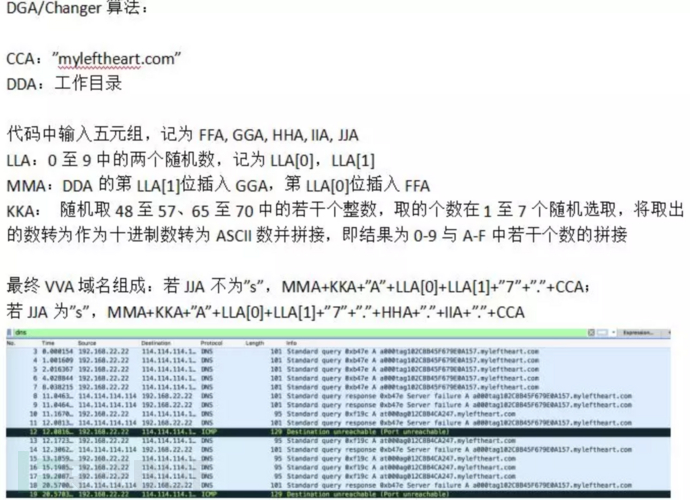
receive function:
Run the EEA function to obtain the VVA domain name, and set the JJA parameter to r;
Try to resolve the VVA domain name. If it fails, an exception will be thrown, and a new domain name will be regenerated and try to resolve the new domain name. Repeat the operation until the domain name is reached. The parsing is successful; if successful, take the first successfully parsed IP and take out each segment of the IP respectively;
If the IP is 1.2.3.*, set NNA to false and RRA The value is written into the PPA file and exits the main function;
If NNA is true, modify the value of RRA to the first three segments of the IP and continue to loop the main function;
If the IP is 24.125.*.*, then concatenate the third and fourth segments of the IP as the C:\Users\Public\Public\$DDA\receivebox subfolder name (PPA), set GGA to 1, and set NNA to true, continue to loop the main function;
If the IP is 11.24.237.110, stop parsing and exit the main function. This IP is the IP once used by OilRig.
Send function:
Run Slaber to check the sent file, run the EEA function to obtain the VVA domain name, and set the JJA parameter to s;
Try to resolve the VVA domain name, if it fails, then Throw an exception, regenerate a new domain name and try to resolve the new domain name. Repeat the operation until the domain name resolution is successful; if successful, take the first successfully resolved IP and take out each segment of the IP separately;
If the IP is 1.2.3.*, take out the value of the fourth segment of the IP and loop the main function;
If the IP is 11.24.237.110, stop parsing and exit the function, and delete the data to be sent. document.
Slaber function:
Check the size of the sent file. If it exceeds 600kb, an error will be reported. Otherwise, run the resolver function.
resolver function:
Resolve the sent file, each group of 30 characters.
Processor function:
Process the received file, MMB is the file in the "sendbox" folder;
If the received file name ends with "0", it will be received Write the file into the "sendbox" folder and use UTF-8 encoding, and then remove the previously received file;
If the received file name ends with "1", if there is a path in the received file content , then use this path as the sending path;
If it does not exist, write the "File not exist" string into the MMB file, and then remove the previously received file; The name ends with "2", set the RRB to the file in the "done" folder, move the received file to the "done" folder, then write the content of the file to the MMB file, and then remove the previously received file .
2.1.3 hUpdater.ps1Resolve the IP of "myleftheart.com" and try to connect;
If the C:\Users\Public\Public\files\ cfg.ini file exists, take the corresponding parameter fields such as srv, usr, pas, prt, and dom. Concatenate the values of srv and prt into a new string through ":", and set the string as a proxy server using http, and use the values of usr, pas, and dom as the credentials of the proxy server; if they do not exist, obtain the default proxy Server;
OOA: Randomly select several integers from 0 to 9, randomly select the number from 1 to 9, and splice the extracted numbers;
DDA: for dUpdater. DDA in ps1 script;
PPA: The fifth bit of DDA is obtained by inserting OOA;
Download the file from "http://myleftheart.com/co/$PPA", set the downloaded The file content is QQA, separate QQA with "", and set the array to SSA.
p is the path C:\Users\Public\Public\files\$SSA[0].
If the length of SSA[2] is greater than 0 and the "not" string does not exist in SSA[2], download the file from http://myleftheart.com/fil/SSA[3] to C:\Users \Public\Public\files\$SSA[2], and then write the content to the path p;
If the length of SSA[1] is greater than 0 and the "not" string does not exist in SSA[1], then Upload the file with path p to http://myleftheart.com/res/$PPA$SSA[0];
If the length of SSA[4] is greater than 0 and the "not" character does not exist in SSA[4] String, then upload the file with path SSA[4]d to http://myleftheart.com/res/$PPA$SSA[0];
If the last data value in SSA is "1" , then run the main function in a loop;
If the length of SSA[0] is greater than 0 and there is no "not" string in SSA[1], upload the file with path p to http://myleftheart.com/res /$PPA$SSA[0], and delete the file with path p.
2.2 Server Side
The Server Side is the general control end used by APT34 to manage the compromised host. It can download files from the compromised host and upload files to the compromised host.
This server provides a simple login interface.

Managing users and passwords through a JSON configuration file is very simple. In the leaked documents, easy-to-guess usernames (blacktusk) and passwords (fireinthehole) were used.
The GUID in the picture below (/7345SDFHSALKJDFHNASLFSDA3423423SAD22) is used to guide the browser to the login page. This GUID can be said to be very important.
 The host lists for both HTTP Agent and DNS Agent are also available on the server side.. From this list you can easily see which hosts are currently controlled.
The host lists for both HTTP Agent and DNS Agent are also available on the server side.. From this list you can easily see which hosts are currently controlled.
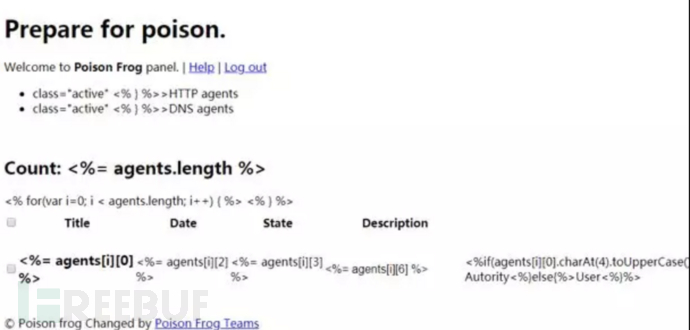
Each HTTP Agent and DNS Agent has a page with detailed information. Here, you can issue C&C commands to the compromised host and upload or download files. The DNS Agent here may have incorporated some functions of Glimpse. Glimpse is introduced in detail below.
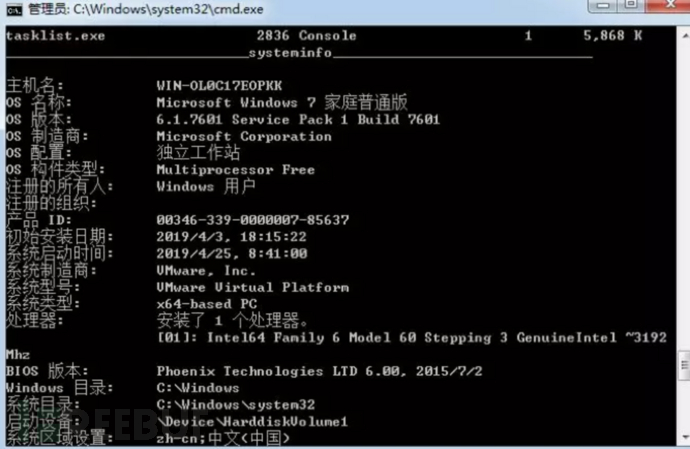
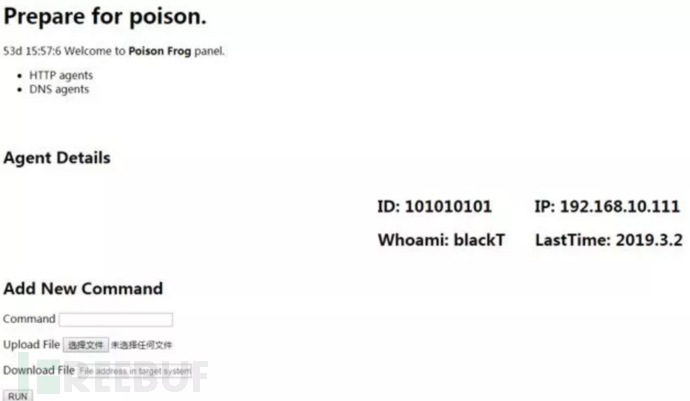 For compromised hosts, APT34 uses a default BAT remote control script to obtain host information. The information obtained is very detailed, including system, user, group, domain, specific registry, Scheduled tasks, anti-virus software, and more.
For compromised hosts, APT34 uses a default BAT remote control script to obtain host information. The information obtained is very detailed, including system, user, group, domain, specific registry, Scheduled tasks, anti-virus software, and more.

3.Webmask
This tool is mainly deployed on the attacker's server to implement DNS proxy, hijack specific DNS domain names, and Point the domain name to the local server by default, implement HTTP/HTTPS proxy through Squid3 ICAP, and steal sensitive information such as the victim's account password.
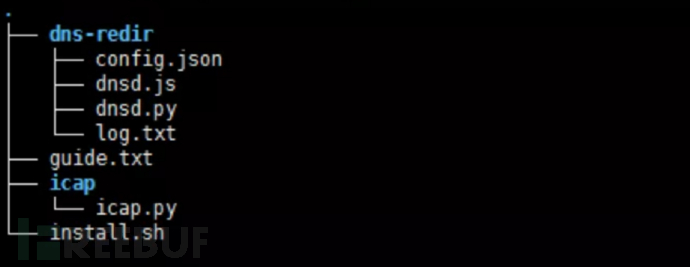
dns-redir directory:
dnsd.py: DNS proxy forwarding script
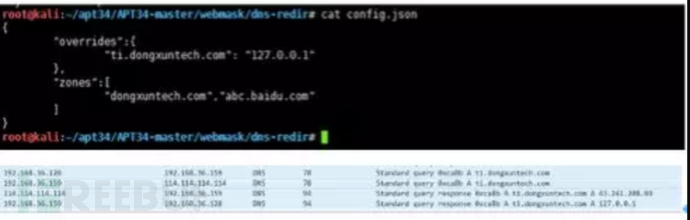
config.json: Configuration file
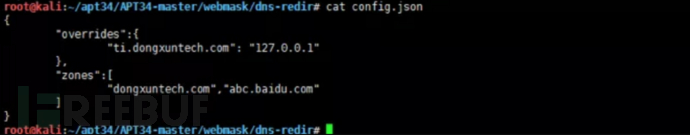
dnsd.js: JS type DNS proxy script, similar to dnsd.py in function.
The local simulated DNS proxy function screenshots are shown below:
icap directory:
icap.py: needs to be combined with Squid3 Use, build http/https proxy, and record sensitive data in the proxy locally.
squid.conf configuration file:

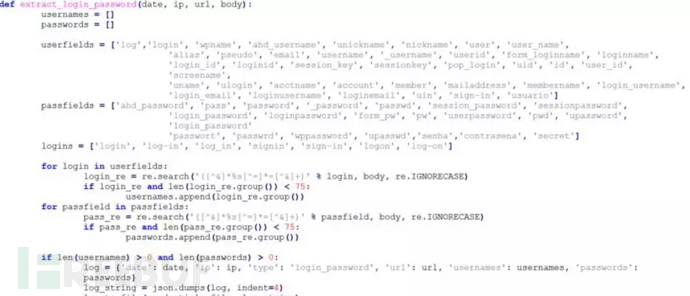
Squid3 ICAP implements a transparent proxy server. The icap.py script extracts and records sensitive data such as passwords. to the local log file.
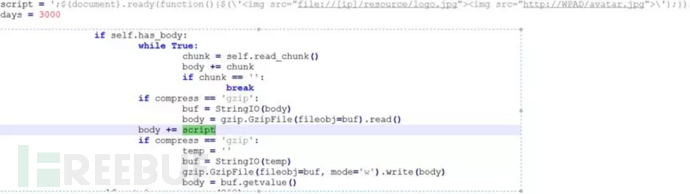
The icap script file adds hijacking code to the response_body part and loads the specified image element in the victim's browser.
4.Glimpse
Glimpse consists of three parts: Agent, Panel and Server. It is a DNS remote control tool. Judging from some codes in Glimpse Server, some of its functions may overlap with poison frog, such as the way to issue commands.
 Overall, Glimpse is very similar to the poison frog introduced above. The leaked information also gives us how to use Glimpse.
Overall, Glimpse is very similar to the poison frog introduced above. The leaked information also gives us how to use Glimpse.
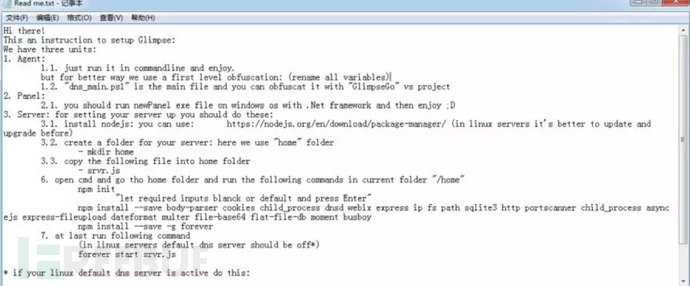
4.1 Agent
Similarly, the Agent in Glimpse is a backdoor program running on the compromised host. The main function is to accept commands, upload and download files.
Agent uses the C:\Users\Public\Libraries directory on the host as its working directory. Sending files and receiving files will be completed in subdirectories under this directory.
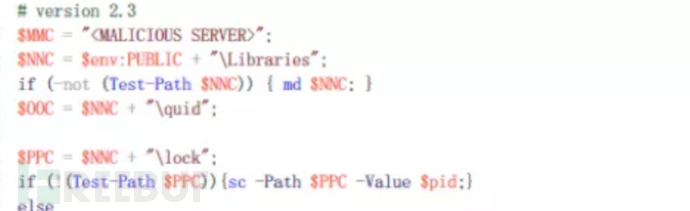 Agent can work in two modes, one is ping mode and the other is text mode.
Agent can work in two modes, one is ping mode and the other is text mode.
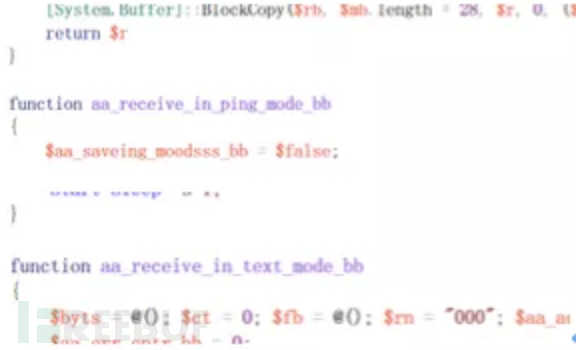
#ping mode is mainly used to exchange host information. The text mode is akin to the internal protocol mode between the Agent and Server, which enables the acceptance of internal instructions..
4.2 Panel
Panel is used to view the status of the master control. You can see how many compromised hosts are controlled. At the same time, you can send commands to the compromised hosts here.
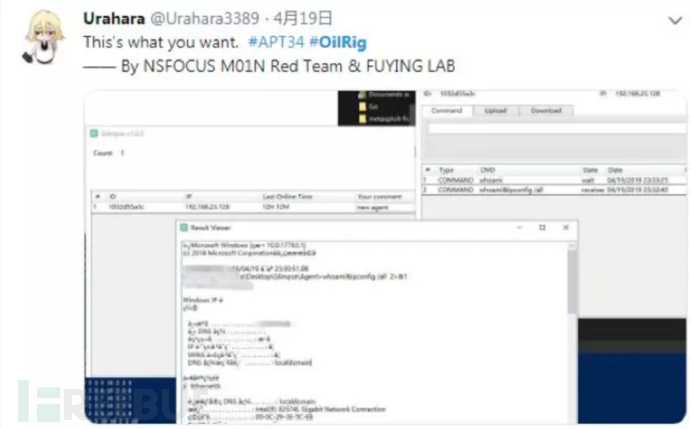
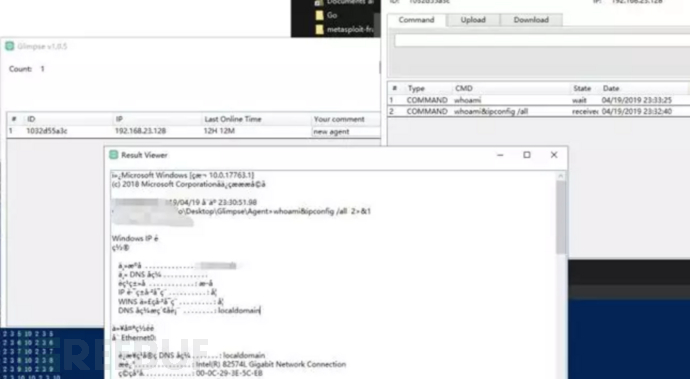
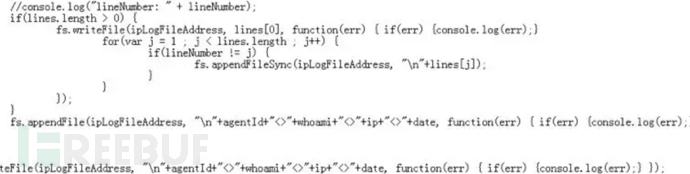
You can see that the command was sent to the compromised host through the panel and the result was returned.
4.3 Server
Server is the master control terminal. It communicates through the DNS tunnel protocol and can respond to the ping mode message or TXT mode command sent by the Agent. It can also respond to the Send commands to Agent in TXT mode. Judging from the code style, Glimpse and Poison Frog should be created by the same team.
#The server supports more protocol commands in TXT mode. We can briefly check the meaning of these commands.
if (action == 'M') { // in this place we check the request for type of connection ping or text type if (action == 'W') { // in this place we check the request type if its text we response it else if (action == 'D') { else if (action == '0') { // ctrl[0] => action, if 0 = is there any file else if (action == '1') { // ctrl[0] => action, if 1 = sending the file else if (action == '2') {// ctrl[0] => action, if 2 = receiveing the file
IOCs
MD5:
cd0bbff03ce7946cd7c9dc339726d90a9d3d8fe14927172ca5546bdb95d947625e17061bf2dce87d402ddd8531abb49f
Domain name:
myleftheart.com
IP:
11.24.237.110
Protection measures
1 .Do not easily open suspicious files, such as emails, suspicious links, suspicious documents, etc.
2. Install system patches in a timely manner and use the latest version of software.
3. Install anti-virus software and update the virus database in a timely manner.
The above is the detailed content of How to implement APT34 leaked weapon report analysis. For more information, please follow other related articles on the PHP Chinese website!

