Home >Operation and Maintenance >Nginx >How to configure Nginx server https
How to configure Nginx server https
- WBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBforward
- 2023-05-23 11:01:061698browse
Apply for a certificate
There are currently many organizations on the Internet that provide personal free SSL certificates, with validity periods ranging from several months to several years. Take startssl: https://www.startssl.com as an example. After successful application, it will be valid for 3 years and can be renewed for free after expiration.
The specific application process is also very simple.
After registering and logging in, select certificates wizard >> dv ssl certificate to apply for a free ssl certificate.
After verifying the domain name through email, then generate the csr of the ssl certificate in your own server, Remember the secret to generate the input , you will use it later:
openssl req -newkey rsa:2048 -keyout weizhimiao.cn.key -out weizhimiao.cn.csr
will generate The certificate is placed in the specified directory where the certificate is stored, such as /data/secret/. View the contents of the certificate weizhimiao.csr, copy the contents to the certificate signing request (csr) section of the page, and submit the page.
Download the generated certificate and select the corresponding web server (nginx, 1_weizhimiao.cn_bundle.crt), so that we have both the private key and the public key.
1_weizhimiao.cn_bundle.crt (public key)
weizhimiao.cn.key (private key)
nginx configuration (add https to the specified domain name)
nginx.conf current configuration
...
http {
...
include /etc/nginx/conf.d/*.conf;
server {
...
}
}./conf.d/weizhimiao.cn.conf added
server{
listen 443 ssl;
server_name weizhimiao.cn;
ssl_certificate /data/secret/1_weizhimiao.cn_bundle.crt;
ssl_certificate_key /data/secret/weizhimiao.cn.key;
ssl_prefer_server_ciphers on;
ssl_protocols tlsv1 tlsv1.1 tlsv1.2;
ssl_ciphers 'keecdh+ecdsa+aes128 keecdh+ecdsa+aes256 keecdh+aes128 keecdh+aes256 kedh+aes128 kedh+aes256 des-cbc3-sha +sha !anull !enull !low !md5 !exp !dss !psk !srp !kecdh !camellia !rc4 !seed';
add_header strict-transport-security 'max-age=31536000; preload';
add_header x-frame-options deny;
ssl_session_cache shared:ssl:10m;
ssl_session_timeout 10m;
keepalive_timeout 70;
ssl_dhparam /data/secret/dhparam.pem;
add_header x-content-type-options nosniff;
add_header x-xss-protection 1;
root /data/www/weizhimiao.cn;
index index.html;
location / {
}
}Note:
A /data/secret/dhparam.pem file is used in the configuration. This file is a key file in pem format and is used for tls in session. Used to enhance the security of ssl. The method to generate this file,
cd /data/secret/ openssl dhparam 2048 -out dhparam.pem
will redirect the original access to port 80. Add
server{
listen 80;
server_name weizhimiao.cn;
return 301 https://weizhimiao.cn$request_uri;
}test
to ./conf.d/weizhimiao.cn.conf to check whether there are syntax errors in the configuration file. You need to enter the previous input when generating the public key. password.
nginx -t enter pem pass phrase: nginx: the configuration file /etc/nginx/nginx.conf syntax is ok nginx: configuration file /etc/nginx/nginx.conf test is successful
Restart nginx (remember, reload does not work)
nginx -s stop enter pem pass phrase: nginx enter pem pass phrase:
Visit weizhimiao.cn with the browser to see if it takes effect.
In addition, after nginx is configured with a security certificate, nginx requires a password for each reload, stop, and other operations.
You can generate a decrypted key file to replace the original key file.
cd /data/secret/ openssl rsa -in weizhimiao.cn.key -out weizhimiao.cn.key.unsecure
Replace the weizhimiao.cn.key file in weizhimiao.cn.conf.
server {
...
ssl_certificate /data/secret/1_weizhimiao.cn_bundle.crt;
ssl_certificate_key /data/secret/weizhimiao.cn.key.unsecure;
...
}Every time after reload, it will not You need to enter your password.
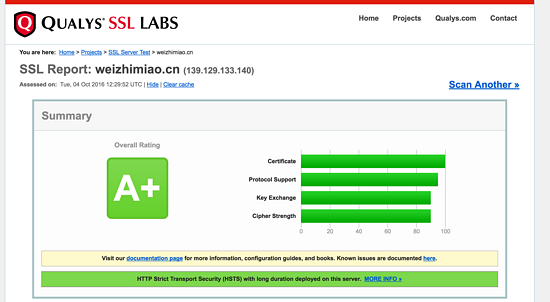
Finally, use ssllabs to test.
result
The above is the detailed content of How to configure Nginx server https. For more information, please follow other related articles on the PHP Chinese website!

