Home >Operation and Maintenance >Safety >How to Conduct Authorized APK Penetration Testing
How to Conduct Authorized APK Penetration Testing
- 王林forward
- 2023-05-20 12:29:002469browse
This article aims to provide some testing ideas for beginners who also lack penetration testing experience. The content involved may be relatively basic, cousins, please forgive me. After unpacking the APK and getting the apk, use 7-Zip to unzip it directly to get several folders, an AndroidManifest.xml file, and a dex file. Use dex2jar https://sourceforge.net/projects/dex2jar/ to decompress this dex file to generate a jar file, and then use jd-gui to view the java source code. While it is possible to look for code vulnerabilities by looking at the source code, obfuscation often occurs and will not be discussed in depth here. The xml file mentioned above must not be distributed before. It involves many important configuration items, such as: - android:debuggable is true in the AndroidManifest.xml file. The app can be debugged arbitrarily - android: allowBackup is true in the AndroidManifest.xml file. App data can be backed up and exported. - Wait... There is another point that may be used during the actual test: after decompressing the apk, you can try to search the db file in powershell. There may be sensitive information (why do you say this, because I encountered it once ...)
for /r F:\source-code %i in (*.db) do echo %i
apk security analysis and detection:
Experiment: apk security analysis and detection (Hetian Network Security Laboratory)
Conduct experiments to learn how to run apk security analysis Detection program, and use this to perform security analysis and detection on the apk, and the results reveal potential threats. )
The simplest case of enumerating user names is that when entering a user name and logging in, the system will respond that the user name does not exist. What I encountered this time was that logging in does not require a password, but you need to enter a registered username. Then a verification code will be sent to the corresponding mobile phone based on the username. At the same time, it is set that it cannot be resent within 120s, and the verification code is valid for 120s. At this time, it seems that we can't do anything through the verification code, but during the actual test process, we found that 1. When we enter the existing account, it prompts that the sending is successful; 2. If we send it repeatedly, we will respond that it cannot be sent again within 120s; 3. Enter If there is no user, it will prompt that the sending failed. Even if a time limit is set, username enumeration can still verify whether the username exists through blasting, just based on the information returned by the server.
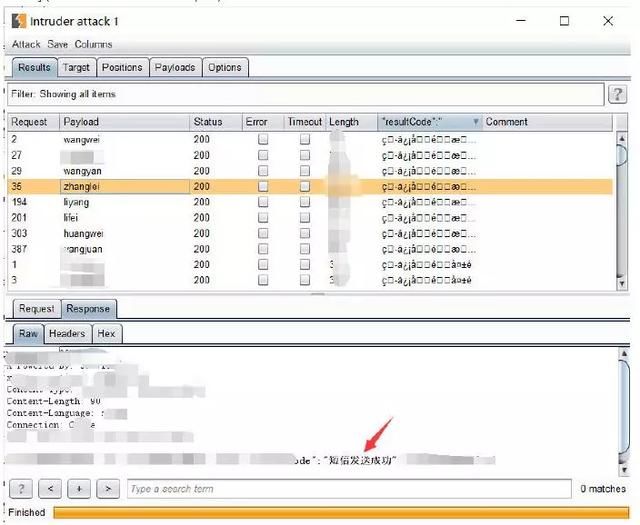
Wait, since we don’t know the mobile phone number and we are not allowed to enter the password to log in, even if we get the username to generate the social engineering dictionary, it will not be used. Then we get the user What's the use of a name? Of course it is useful, but it depends on the specific scenario. For example, in the following case, any verification code can be bypassed. When we log in, the server sends a SMS verification code to the mobile phone number bound to the account. We enter an account number obtained in the previous step and enter the verification code casually. Click to capture the packet after logging in. The login fails and there are two code fields in the response
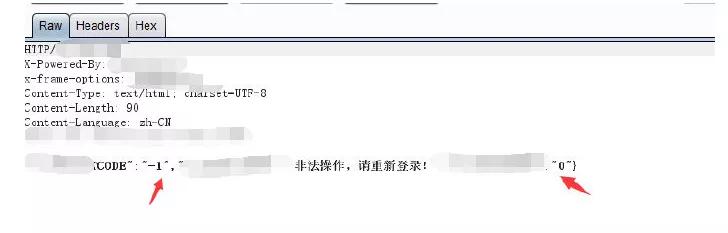
Try changing it:

It works!
Verification code bypass vulnerability:
Experiment: Verification code bypass vulnerability
(Master the common verification code bypass vulnerability principles, and bypass Method exploitation and vulnerability protection)
After successfully logging in to the function page, click on each function. On the personal information page, there is a function to query the number of people online in real time. That column only displays the number of people, and there is no arrow next to it
I once thought I couldn't click there (in fact, because the amount of data was too large, it took a long time to load, so I just clicked back, which gave me the feeling that there was nothing here) , after entering, you can see the information of all logged in people.

After I tried different users, I found that the user information here does not have permission restrictions, which means it is visible to everyone, and the permissions are obviously improperly configured. The application also has several query functions. The BURP tool shows that the format of the returned data packets is JSON
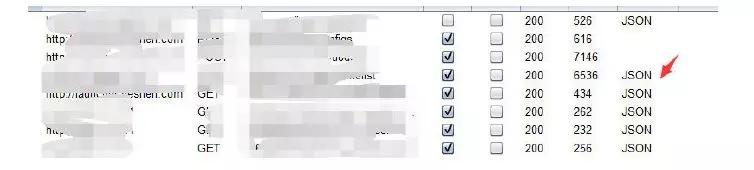
. Try injecting JSON and trying XXE. Trying everywhere does not help. Because I don't have much experience. There is another parameter in front, try it?

There is drama!
Try xss
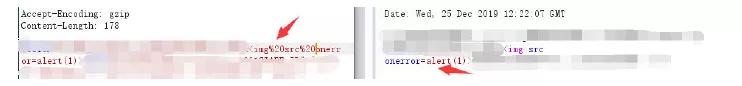
Put it in the browser and the pop-up window will be successful!
The above is the detailed content of How to Conduct Authorized APK Penetration Testing. For more information, please follow other related articles on the PHP Chinese website!

