Home >Operation and Maintenance >Safety >Example Analysis of Security Risks of SolarWinds Supply Chain APT Attack Incident
Example Analysis of Security Risks of SolarWinds Supply Chain APT Attack Incident
- 王林forward
- 2023-05-18 12:52:271109browse
Background
On December 13, FireEye, the top security company in the United States (Chinese name: Fire Eye) Released a report stating that it had discovered a global intrusion activity and named the organization UNC2452. The APT organization invaded SolarWinds, implanted malicious code in the SolarWinds Orion commercial software update package, and distributed it. FireEye called it SUNBURST malware. The backdoor contains the ability to transfer files, execute files, analyze the system, reboot the machine, and disable system services, allowing for lateral movement and data theft.
SolarWinds Orion Platform is a powerful, scalable infrastructure monitoring and management platform designed to simplify IT management of on-premises, hybrid and software-as-a-service (SaaS) environments with a single interface. The platform provides real-time monitoring and analysis of network equipment, and supports customized web pages, various user feedback, and map browsing of the entire network.
Event Overview
On December 13, FireEye disclosed that it would commercialize SolarWinds Orion In a software update Trojanized supply chain attack, the SolarWinds digital signature component of the Orion software framework, SolarWinds.Orion.Core.BusinessLayer.dll, is inserted into a backdoor that communicates with a third-party server via HTTP. FireEye said this type of attack may have first appeared in the spring of 2020 and is still ongoing. From March to May 2020, the attacker digitally signed multiple Trojan updates and published them to the SolarWinds update website, including hxxps://downloads.solarwinds[.]com/solarwinds/CatalogResources/Core/ 2019.4/2019.4.5220.20574/SolarWinds-Core-v2019.4.5220-Hotfix5.msp. FireEye has released the characteristics and detection rules of the backdoor on GitHub. The GitHub address is as follows:
https://github.com/fireeye/sunburst_countermeasures
File with Trojan implanted For the SolarWinds.Orion.Core.BusinessLayer.dll component, a standard Windows installer patch file. Once the update package is installed, the malicious DLL will be loaded by the legitimate SolarWinds.BusinessLayerHost.exe or SolarWinds.BusinessLayerHostx64.exe (depending on system configuration) program.
SolarWinds.Orion.Core.BusinessLayer.dll (b91ce2fa41029f6955bff20079468448) is a SolarWinds signature plug-in component of the Orion software framework. The SolarWinds.Orion.Core.BusinessLayer.OrionImprovementBusinessLayer class implements communication with third-party servers through HTTP. , a backdoor that transfers and executes files, analyzes the system, and disables system services. The backdoor’s network transfer protocol is disguised as legitimate SolarWinds activity to evade detection by security tools. 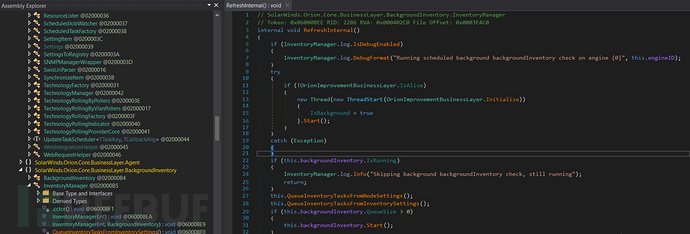
SolarWinds.Orion.Core.BusinessLayer.dll is signed by solarwind with serial number 0f:e9:73:75:20:22:a6:06:ad:f2:a3:6e: Certificate of 34:5d:c0:ed. The document was signed on March 24, 2020. 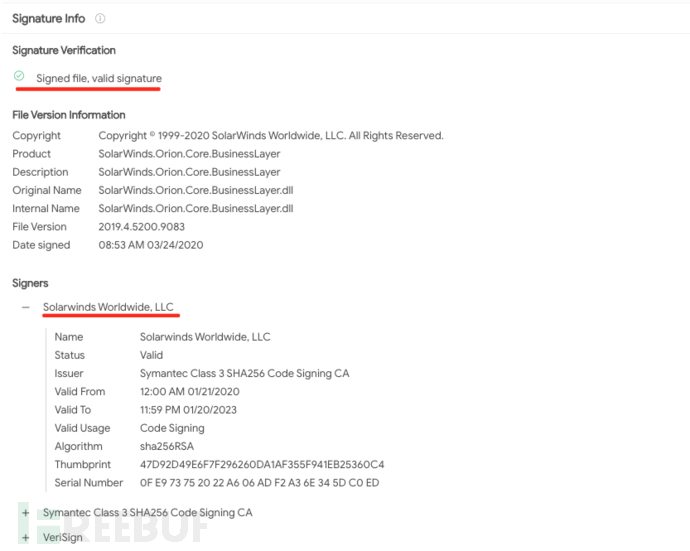
Scope of Impact
Solution
The above is the detailed content of Example Analysis of Security Risks of SolarWinds Supply Chain APT Attack Incident. For more information, please follow other related articles on the PHP Chinese website!

