 Technology peripherals
Technology peripherals AI
AI It's scary to think about it! PimEyes steals photos of dead people to train facial recognition algorithm
It's scary to think about it! PimEyes steals photos of dead people to train facial recognition algorithmIt's scary to think about it! PimEyes steals photos of dead people to train facial recognition algorithm
When you search for your own photos on PimEyes, you will see many photos of yourself and people who look like you.
However, when this tool trains the algorithm, it does not use photos authorized by the user, but based on photos from various platforms across the entire network to perform facial recognition.
So after your photo is recognized, the search results will often show screenshots of videos from many websites.
Not only that, but the website was also revealed to have been stealing photos of dead people to train algorithms.

Don’t spare the dead
Some people are dead, but they are still alive on the Internet.
Cher Scarlett is a software engineer and writer.
Recently, she suddenly discovered that photos of her mother, her great-great-grandmother who had passed away long ago, and her sister who passed away in 18 years all appeared on PimEyes.
All of these photos are pictures that she and her family uploaded to Ancestry themselves, but the site openly prohibits 「from Ancestry in its terms and conditions scrape data, including photos, from our websites and services and resell, copy or publish any content or information found on Ancestry.
## So Scarlett felt Shockingly, not only was this against Ancestry policy, but there was no way her deceased family would have allowed PimEyes to use these photos to train their algorithm.
This sounds similar to the story of Henrietta Lacks: 「 immortal HeLa cells」has been used for decades For medical research and drug development, it is one of the most important medical achievements in hundreds of years. But these studies were actually conducted after her death and without her permission. Without her knowledge, her cells were studied, reproduced, and even her genetic sequence was made public.

#Although these two things are not of the same magnitude. However, it is true that your privacy should be respected after your death.
Daniel Leufer, senior policy analyst at digital rights group Access Now, said: "Although PimEyes says it won't give you the person's identity directly through their website, But you can see the picture website with one click, and your name will indeed appear on the website.
『When I think of everyone photos will be entered into the biometric identifier of the facial recognition software without their knowledge or consent. I believe that no one will easily post photos on social media anymore. 」Scarlett feels Very disappointed.
『My sister is dead and she can’t come back to life to ask this website to take down her photos.』
Scarlett said this for a reason, because she had previously had issues with this website about withdrawing photos.
If you want to delete your nude photos, you can recharge $29.9 per monthWhen Scarlett first heard about this software, she wanted to test how it looked like her Who are the celebrities like.
She found herself somewhat similar to Britney Spears and Kate Hudson.

After flipping through the pages, she suddenly found a photo of herself being abused more than ten years ago.
This experience once made Scarlett want to commit suicide, so much so that her body's self-protection mechanism made her selectively forget this experience.
Suddenly seeing these photos on the website, she almost collapsed, but she forced herself to investigate the source of these photos and found that she needed to pay a membership fee to view them.
After paying, she found that the photos were scattered on various websites.
What’s even more terrible is that if you want to clear these photos, you not only have to submit an application to verify your identity, but you also have to recharge US$29.9 every month and subscribe to their service so that you can manage the search. As a result, some photos you don't want to be seen are hidden.

Scarlett has been trying to clear the photos, but there is no way to permanently remove them. She even bought PimEyes' most expensive service, but it didn't help. The website stated that as long as the photo subsequently appears in a link to other websites, it will still be displayed.
In other words, subscribing every month is not enough. You have to become a distinguished annual member and apply for cleanup regularly, and each approval takes a long time.
It wasn’t until April last year, when she shared her experience on social networks, that PimEyes actually approved her deletion request.
Investigate you, track you

PimEyes can find other photos they have published online from a person’s photos. Including pictures posted everywhere on websites, blogs, news, and articles.
By piecing together information related to these images, text from blogs and articles, and photos from your work website, someone who wants to investigate you can find out where you work and track you. your residence.
##『Images of anyone, including children, can be searched and tracked on the Internet.』
People who have been domestically abused or abused will lose their sense of security; stalkers will also quietly stalk you, just like in a horror movie; when applying for jobs or entering higher education, this tool can also be used to adjust Reveal all your background information so you have no secrets.
PimEyes has been accused of illegally processing the biometric data of millions of British citizens, arguing that it did not obtain the consent of those whose images were analyzed.
However, faced with accusations of breaching data protection laws, PimEyes argued that it was technically impossible to know how many British citizens’ faces they had analyzed, which amounted to an indirect admission. There is no authorization for this.
Although the platform claims that PimEyes is not designed to monitor others, the platform does not have relevant measures to supervise it, so people are also very dissatisfied with the platform's data security department. trust.

But PimEyes is working hard to reverse the criticism. They say the tool can help journalists with their investigations and say they are working with law enforcement and humanitarian organizations in Germany, Italy, the United Kingdom and the United States to help combat child crime, human trafficking and terrorism.
And, as mentioned above, after the matter was brought to light, PimEyes finally began to help women and began to approve and delete non-consensual nude pornographic photos, which can be regarded as Gain some virtue.
The above is the detailed content of It's scary to think about it! PimEyes steals photos of dead people to train facial recognition algorithm. For more information, please follow other related articles on the PHP Chinese website!
 Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AM
Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AMSince 2008, I've championed the shared-ride van—initially dubbed the "robotjitney," later the "vansit"—as the future of urban transportation. I foresee these vehicles as the 21st century's next-generation transit solution, surpas
 Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AM
Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AMRevolutionizing the Checkout Experience Sam's Club's innovative "Just Go" system builds on its existing AI-powered "Scan & Go" technology, allowing members to scan purchases via the Sam's Club app during their shopping trip.
 Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AM
Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AMNvidia's Enhanced Predictability and New Product Lineup at GTC 2025 Nvidia, a key player in AI infrastructure, is focusing on increased predictability for its clients. This involves consistent product delivery, meeting performance expectations, and
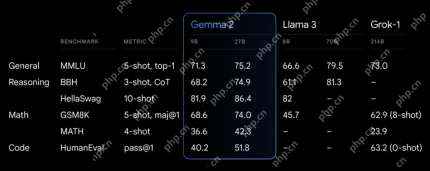 Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AM
Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AMGoogle's Gemma 2: A Powerful, Efficient Language Model Google's Gemma family of language models, celebrated for efficiency and performance, has expanded with the arrival of Gemma 2. This latest release comprises two models: a 27-billion parameter ver
 The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AM
The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AMThis Leading with Data episode features Dr. Kirk Borne, a leading data scientist, astrophysicist, and TEDx speaker. A renowned expert in big data, AI, and machine learning, Dr. Borne offers invaluable insights into the current state and future traje
 AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AM
AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AMThere were some very insightful perspectives in this speech—background information about engineering that showed us why artificial intelligence is so good at supporting people’s physical exercise. I will outline a core idea from each contributor’s perspective to demonstrate three design aspects that are an important part of our exploration of the application of artificial intelligence in sports. Edge devices and raw personal data This idea about artificial intelligence actually contains two components—one related to where we place large language models and the other is related to the differences between our human language and the language that our vital signs “express” when measured in real time. Alexander Amini knows a lot about running and tennis, but he still
 Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AM
Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AMCaterpillar's Chief Information Officer and Senior Vice President of IT, Jamie Engstrom, leads a global team of over 2,200 IT professionals across 28 countries. With 26 years at Caterpillar, including four and a half years in her current role, Engst
 New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AM
New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AMGoogle Photos' New Ultra HDR Tool: A Quick Guide Enhance your photos with Google Photos' new Ultra HDR tool, transforming standard images into vibrant, high-dynamic-range masterpieces. Ideal for social media, this tool boosts the impact of any photo,


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

Dreamweaver Mac version
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SAP NetWeaver Server Adapter for Eclipse
Integrate Eclipse with SAP NetWeaver application server.

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software





