Background introduction
6G technology introduction
With the 5G network expectations With the development of digital transformation, the 6G communication era envisions how humans will interact with the digital virtual world after 2030 to cope with the communication and network challenges after 2030. While traditional applications (such as multimedia streaming) will still exist, the article envisions new application areas for 6G systems, such as multi-sensor extended reality (XR) applications, connected robots and autonomous systems (CRAS), and wireless brain-computer interaction (BCI) [1]. Holographic telepresence, eHealth (including in vivo networks) are other 6G use cases that require extremely high data rates, ultra-low latency and ultra-reliability [2].
6G revolutionizes wireless networks from connected things to “connected intelligence” [1], [2]. Therefore, artificial intelligence becomes an integral part of the network. Distributed heterogeneous networks require ubiquitous AI services to ensure 6G goals are achieved. Intelligent wireless communications, network closed-loop optimization, and 6G big data analysis emphasize the use of artificial intelligence in all aspects of 6G networks.
After 2030, wireless applications will require higher data rates (up to 1 Tb/s), extremely low end-to-end latency (
Threats to 6G security
This section also discusses the Security issues arising from architectural changes and new technologies. Figure 1 illustrates possible attacks on different layers of the 6G architecture, outlining how this paper presents the security threat picture for 6G.

Figure 1 Intelligent 6G architecture [6] and 6G security and privacy issues
in 5G Network softwareization technologies such as software-defined networking (SDN), network functions virtualization (NFV), multi-access edge computing (MEC), and network slicing are still applicable to 6G systems; therefore, their security issues still exist in 6G. Prominent security issues related to SDN are attacks on SDN controllers, attacks on northbound and southbound interfaces, inherent vulnerabilities in the platforms used to deploy SDN controllers/applications [7]. NFV-related security issues are attacks on virtual machines (VMs), virtual network functions (VNFs), hypervisors, VNF managers, and NFV coordinators [8]. Due to the massively distributed nature of 6G systems, MEC in 6G is subject to physical security threats, distributed denial of service (DDoS), and man-in-the-middle attacks. A potential attack on network slicing is a DoS attack, where information is stolen through a compromised slice. Attacks on network softwareization technologies prevent 6G networks from achieving the promised dynamism and full automation.
6G envisions the Internet of Everything (IOE), a collection of billions of heterogeneous devices. A basic device security model that relies on SIM cards is not a realistic deployment of IOE in 6G, especially for small form factor devices such as in-body sensors. In such a large network, key distribution and management functions are inefficient. Resource-constrained IoT devices are unable to provide complex passwords to maintain strong security, making them prime targets for attackers. These devices can be compromised and potentially used to launch attacks. Hyperconnected IOEs pose privacy concerns for providing data collection for 6G applications. Exploiting resource-constrained IoT devices for data theft will impact data privacy, location privacy, and identity privacy.
Existing 5G network deployments typically serve vertical industries such as industry, healthcare, and education. 6G further extends this concept by allowing smaller networks such as in-body networks, swarms of drones, environmental sensor networks with longer battery life [4]. These local networks operate as independent networks and interoperate with wide area connections when needed. Unlike well-defined native 5G networks, many stakeholders implement native 6G networks with varying levels of embedded security. On-premises 6G networks with minimal security provide an opportunity for intruders to launch attacks. Then infiltrate into the network of trust-compromised networks.
Security of 6G architecture
Dense cellular deployments, mesh networks, multiple connections and device-to-device (D2D) communications will become the norm in 6G. Malicious parties are more likely to exploit distributed networks with more vulnerable devices, each with mesh connectivity, increasing the threat surface. The definition of subnetworks requires changes to the security policy. It is far from practical for a WAN to provide security for a large number of devices within each subnet. In 6G, a hierarchical security mechanism that distinguishes subnet-level communication security and subnet-to-WAN security will be a better approach. 6G networks will coexist with frameworks such as zero-touch networking and service management (ZSM) architectures to shorten service time to market, lower operational costs and reduce human error. Full automation with self-learning capabilities allows attacks to propagate in a closed loop and data privacy protection is extremely challenging because in a zero-touch network, automation and less human intervention are required.
The security of 6G technology
6G relies on artificial intelligence to achieve a fully autonomous network . Therefore, attacks on AI systems, especially machine learning (ML) systems, will impact 6G. Poisoning attacks, data injection, data manipulation, logic destruction, model evasion, model inversion, model extraction, and membership inference attacks are potential security threats against ML systems. A larger set of features makes AI systems perform better. Attacks on collected data, as well as inadvertent use of private data, can lead to privacy concerns because data processing is often invisible to users. Blockchain is also a key technology to unlock the potential of 6G systems. Blockchain is suitable for decentralized resource management, spectrum sharing and service management in large-scale distributed 6G networks. A 51% attack is feasible on quantum computers to destabilize a blockchain. Since blockchain networks store data publicly, privacy protection is challenging. The current 5G standard does not address the security issues posed by quantum computing; instead, it relies on traditional cryptography such as elliptic curve cryptography (ECC). Since the 6G era marks the emergence of quantum computers, current security mechanisms based on asymmetric key encryption are vulnerable to quantum computer-based attacks. Therefore, without the design of quantum-safe cryptographic algorithms, secure 5G communications utilizing asymmetric key cryptography may no longer be suitable for post-quantum security.
The important role of AI in 6G security
##Use AI to mitigate security issues in 6G architecture Compared to current centralized cloud-based AI systems, 6G will primarily rely on edge intelligence. The distributed nature enables edge-based federated learning to be performed across large-scale devices and data systems to achieve network security and ensure communication efficiency. 6G architecture envisions connected intelligence and uses AI at different levels of the network hierarchy. Tiny cell-level AI has the potential to thwart DoS attacks on cloud servers at the lowest level. The multi-connectivity of devices in a mesh network allows multiple base stations to evaluate a device's behavior using an AI classification algorithm and jointly determine authenticity using a weighted average scheme. Behavior-based approaches reduce the overhead of frequent key exchanges due to frequent handovers caused by microcells and multiple-access technologies. Based on federated learning, there can be different levels of authorization at the subnet level and WAN level. Trust scores obtained within a subnetwork level can be shared externally only when external communication is required. Learning-based intrusion detection methods may be good candidates for preventing CPMS and UPMS attacks because the edge already has data provided by intelligent services. Frameworks like ZSM are equipped with domain analysis and domain intelligence services for zero-touch management of networks, primarily based on artificial intelligence. AI model evaluation, API security AI engine is a key security functional component that enhances the security of the ZSM reference architecture. Using AI to mitigate security issues in 6G technology Predictive analysis using AI can Predict attacks before they occur, such as 51% blockchain attacks. Quantum computers could threaten asymmetric key encryption. However, they can also provide exponential speeds to AI/ML algorithms to perform tasks faster and achieve previously impossible tasks. Therefore, quantum machine learning for cybersecurity is a potential defense technology against quantum computer-based attacks. Reinforcement learning (RL)-based smart beamforming technology provides optimal beamforming strategies against eavesdropper attacks in VLC systems. Jamming is similar to a DoS attack. Therefore, anomaly-based detection systems equipped with AI are possible solutions to detect jamming attacks. AI-based authentication and authorization systems are also suitable for preventing node disclosure attacks. Using AI for 6G privacy protectionMulti-connectivity mesh networks with microcells in 6G allow devices to communicate simultaneously through multiple base stations. Edge-based ML models can be used for dynamic detection of privacy-preserving routing, ranking devices, and allowing devices to transmit data through privacy-preserving routing based on ranking. Compared to cloud-based centralized learning, federated learning keeps data close to users to enhance data privacy and location privacy. 6G subnetwork-level AI allows privacy to be preserved within the subnetwork and only shared externally learned information to minimize privacy risks. Restricting data within a network is suitable for applications such as in vivo networks. With the vast number of applications in 6G and the massive collection of data to feed intelligent models, users will choose different levels of privacy on different applications. AI-based service-oriented privacy protection policy updates are potential solutions to support fully automated 6G networks.
References
[1] W.Saad, M.Bennis, and M.Chen, “A Vision of 6G Wireless Systems: Applications, Trends, Technologies, and Open Research Problems, ” IEEE Network, vol. 34, no. 3, pp. 134–142, 2019
[2] C. de Alwis, A. Kalla, Q. V. Pham , P. Kumar, K. Dev, W. J. Hwang, and M. Liyanage, “Survey on 6G Frontiers: Trends, Applications, Requirements, Technologies and Future Research,” IEEE Open Journal of the Communications Society, pp. 1–1, 2021.
[3]J. Lin, W. Yu, N. Zhang, X. Yang, H. Zhang, W. Zhao, A survey on internet of things: architecture, enabling technologies, security and privacy, and applications, IEEE Internet Things J. 4 (5) (2017) 1 125–1 142 .
[4]T. Shinzaki , I. Morikawa , Y. Yamaoka , Y. Sakemi , IoT security for utilization of big data: Mutual authentication technology and anonymization technology for positional data, Fujitsu Sci. Tech. J. 52 (4) (2016) 52–60 .
[5]M. Ylianttila, R. Kantola, A. Gurtov, L. Mucchi, I. Oppermann, Z. Yan, T. H. Nguyen, F. Liu, T. Hewa, M. Liyanage et al., “6G White Paper: Research Challenges for Trust, Security and Privacy,” arXiv preprint arXiv :2004.11665, 2020.
[6]K. B. Letaief, W. Chen, Y. Shi, J. Zhang, and Y.-J. A. Zhang, “The Roadmap to 6G: AI Empowered Wireless Networks,” IEEE Communi cations Magazine, vol. 57, no. 8, pp. 84–90, 2019.
[7]I. Ahmad, T. Kumar, M. Liyanage, J. Okwuibe, M. Ylianttila, and A . Gurtov, “Overview of 5G Security Challenges and Solutions,” IEEE Communications Standards Magazine, vol. 2, no. 1, pp. 36–43, 2018.
[8]R. Khan, P. Kumar , D. N. K. Jayakody, and M. Liyanage, “A survey on security and privacy of 5g technologies: Potential solutions, recent advancements, and future directions,” IEEE Communications Surveys & Tutorials, vol. 22, no. 1, pp.196–248 , 2019.
The above is the detailed content of AI meets 6G—opportunities and challenges. For more information, please follow other related articles on the PHP Chinese website!
 The AI Skills Gap Is Slowing Down Supply ChainsApr 26, 2025 am 11:13 AM
The AI Skills Gap Is Slowing Down Supply ChainsApr 26, 2025 am 11:13 AMThe term "AI-ready workforce" is frequently used, but what does it truly mean in the supply chain industry? According to Abe Eshkenazi, CEO of the Association for Supply Chain Management (ASCM), it signifies professionals capable of critic
 How One Company Is Quietly Working To Transform AI ForeverApr 26, 2025 am 11:12 AM
How One Company Is Quietly Working To Transform AI ForeverApr 26, 2025 am 11:12 AMThe decentralized AI revolution is quietly gaining momentum. This Friday in Austin, Texas, the Bittensor Endgame Summit marks a pivotal moment, transitioning decentralized AI (DeAI) from theory to practical application. Unlike the glitzy commercial
 Nvidia Releases NeMo Microservices To Streamline AI Agent DevelopmentApr 26, 2025 am 11:11 AM
Nvidia Releases NeMo Microservices To Streamline AI Agent DevelopmentApr 26, 2025 am 11:11 AMEnterprise AI faces data integration challenges The application of enterprise AI faces a major challenge: building systems that can maintain accuracy and practicality by continuously learning business data. NeMo microservices solve this problem by creating what Nvidia describes as "data flywheel", allowing AI systems to remain relevant through continuous exposure to enterprise information and user interaction. This newly launched toolkit contains five key microservices: NeMo Customizer handles fine-tuning of large language models with higher training throughput. NeMo Evaluator provides simplified evaluation of AI models for custom benchmarks. NeMo Guardrails implements security controls to maintain compliance and appropriateness
 AI Paints A New Picture For The Future Of Art And DesignApr 26, 2025 am 11:10 AM
AI Paints A New Picture For The Future Of Art And DesignApr 26, 2025 am 11:10 AMAI: The Future of Art and Design Artificial intelligence (AI) is changing the field of art and design in unprecedented ways, and its impact is no longer limited to amateurs, but more profoundly affecting professionals. Artwork and design schemes generated by AI are rapidly replacing traditional material images and designers in many transactional design activities such as advertising, social media image generation and web design. However, professional artists and designers also find the practical value of AI. They use AI as an auxiliary tool to explore new aesthetic possibilities, blend different styles, and create novel visual effects. AI helps artists and designers automate repetitive tasks, propose different design elements and provide creative input. AI supports style transfer, which is to apply a style of image
 How Zoom Is Revolutionizing Work With Agentic AI: From Meetings To MilestonesApr 26, 2025 am 11:09 AM
How Zoom Is Revolutionizing Work With Agentic AI: From Meetings To MilestonesApr 26, 2025 am 11:09 AMZoom, initially known for its video conferencing platform, is leading a workplace revolution with its innovative use of agentic AI. A recent conversation with Zoom's CTO, XD Huang, revealed the company's ambitious vision. Defining Agentic AI Huang d
 The Existential Threat To UniversitiesApr 26, 2025 am 11:08 AM
The Existential Threat To UniversitiesApr 26, 2025 am 11:08 AMWill AI revolutionize education? This question is prompting serious reflection among educators and stakeholders. The integration of AI into education presents both opportunities and challenges. As Matthew Lynch of The Tech Edvocate notes, universit
 The Prototype: American Scientists Are Looking For Jobs AbroadApr 26, 2025 am 11:07 AM
The Prototype: American Scientists Are Looking For Jobs AbroadApr 26, 2025 am 11:07 AMThe development of scientific research and technology in the United States may face challenges, perhaps due to budget cuts. According to Nature, the number of American scientists applying for overseas jobs increased by 32% from January to March 2025 compared with the same period in 2024. A previous poll showed that 75% of the researchers surveyed were considering searching for jobs in Europe and Canada. Hundreds of NIH and NSF grants have been terminated in the past few months, with NIH’s new grants down by about $2.3 billion this year, a drop of nearly one-third. The leaked budget proposal shows that the Trump administration is considering sharply cutting budgets for scientific institutions, with a possible reduction of up to 50%. The turmoil in the field of basic research has also affected one of the major advantages of the United States: attracting overseas talents. 35
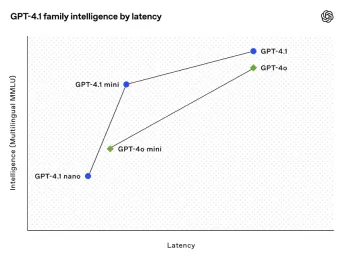 All About Open AI's Latest GPT 4.1 Family - Analytics VidhyaApr 26, 2025 am 10:19 AM
All About Open AI's Latest GPT 4.1 Family - Analytics VidhyaApr 26, 2025 am 10:19 AMOpenAI unveils the powerful GPT-4.1 series: a family of three advanced language models designed for real-world applications. This significant leap forward offers faster response times, enhanced comprehension, and drastically reduced costs compared t


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

WebStorm Mac version
Useful JavaScript development tools

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SublimeText3 English version
Recommended: Win version, supports code prompts!







