 Technology peripherals
Technology peripherals AI
AI Introduction to the 12 most important algorithms of unsupervised learning and a summary of their use cases
Introduction to the 12 most important algorithms of unsupervised learning and a summary of their use casesIntroduction to the 12 most important algorithms of unsupervised learning and a summary of their use cases
Unsupervised Learning (Unsupervised Learning) is another mainstream machine learning method opposite to supervised learning. Unsupervised learning does not have any data annotation, only the data itself.

There are several types of unsupervised learning algorithms. The following are the 12 most important ones:
1. Clustering algorithms classify data points based on similarities. Grouping into clusters
k-means clustering is a popular clustering algorithm that divides data into k groups.
2. Dimensionality reduction algorithm reduces the dimensionality of data, making it easier to visualize and process
Principal component analysis (PCA) is a dimensionality reduction algorithm that projects data into low dimensions space, PCA can be used to reduce the dimensionality of data to its most important features.
3. Anomaly detection algorithm identifies outliers or abnormal data points
Support vector machines can be used for anomaly detection (example). Anomaly detection algorithms are used to detect abnormal points in data sets. There are many methods of anomaly detection, but most of them can be divided into supervised and unsupervised. Supervised methods require labeled datasets, while unsupervised methods do not.
Unsupervised anomaly detection algorithms are usually based on density estimation, trying to find points outside dense regions in the data space.
A simple method is to calculate the average distance of each point to its k nearest neighbors. Points that are very far from neighboring points are likely to be outliers.
There are also many density-based anomaly detection algorithms, including Local Outlier Factor (LOF) and Support Vector Domain Description (SVDD). These algorithms are more complex than simple k-nearest neighbor methods and can often detect more subtle anomalies. Most anomaly detection algorithms require tuning, such as specifying a parameter to control how sensitive the algorithm is to anomalies. If the parameters are too low, the algorithm may miss some anomalies. If set too high, the algorithm may produce false positives (identifying normal points as abnormal points).
4. Segmentation algorithm divides data into segments or groups
The segmentation algorithm can divide the image into foreground and background.
These algorithms can automatically segment data sets into meaningful groups without the need for human supervision. One of the more well-known algorithms in this field is the k-means algorithm. This algorithm divides data points into k groups by minimizing the sum of squared distances within the group.
Another popular segmentation algorithm is the mean shift algorithm. The algorithm works by iteratively moving each data point toward the center of its local neighborhood. Mean shift is robust to outliers and can handle data sets with uneven density. But running it on large datasets can be computationally expensive.
The Gaussian Mixture Model (GMM) is a probabilistic model that can be used for segmentation. Previously gmm required a lot of computation to train, but recent research advances have made it faster. gmm is very flexible and can be used with any type of data. But they sometimes don't always produce the best results. For simple data sets, k-means is a good choice, while gmm is more suitable for complex data sets. Mean shift can be used in either case, but can be computationally expensive on large data sets.
5. Denoising algorithm reduces or removes noise in data
Wavelet transform can be used for image denoising. But noise can arise from various sources, including data corruption, missing values, and outliers. Denoising algorithms improve the accuracy of unsupervised learning models by reducing the amount of noise in the data.
There are many existing denoising algorithms, including principal component analysis (PCA), independent component analysis (ICA) and non-negative matrix factorization (NMF).
6. Link prediction algorithms predict future connections between data points (e.g., future interactions between two nodes in a network)
Link prediction can be used to predict who will become a member of a social network friends in. One of the more commonly used link prediction algorithms is the preferential join algorithm, which predicts that two nodes are more likely to be connected if they have many existing connections.
Another popular link prediction algorithm is the local path algorithm, which predicts that two nodes are more likely to be associated if they share a common neighbor. This algorithm can capture the concept of "structural equivalence" and is therefore frequently used in biological networks.
Finally, the random walk with restart algorithm is also a link prediction algorithm that simulates a random walker on the network and restarts the walker at a random node [17]. The probability of a walker arriving at a specific node is then used to measure the likelihood that a connection exists between two nodes.
7. Reinforcement learning algorithms learn through trial and error
Q-learning is an example of a value-based learning algorithm; it is simple to implement and versatile. But Q-learning sometimes converges to suboptimal solutions. Another example is TD learning, which is more computationally demanding than Q-learning, but often leads to better solutions.
8. Generative models: Algorithms use training data to generate new data
Autoencoders are generative models that can be used to create unique images from image datasets. In machine learning, a generative model is a model that captures the statistical properties of a set of data. These models can be used to generate new data, just like the data they were trained on.
Generative models are used for various tasks such as unsupervised learning, data compression and denoising. There are many types of generative models, such as hidden Markov models and Boltzmann machines. Each model has its pros and cons and is suitable for different tasks.
Hidden Markov models are good at modeling sequential data, while Boltzmann machines are better at modeling high-dimensional data. Generative models can be used for unsupervised learning by training them on unlabeled data. Once the model is trained, it can be used to generate new data. This generated data can then be labeled by humans or other machine learning algorithms. This process can be repeated until the generative model learns to generate data that resembles the desired output.
9. Random forest is a machine learning algorithm that can be used for both supervised and unsupervised learning
For unsupervised learning, random forest can find a group of similar entries, identify outliers, and Compress data.
Random forests have been proven to outperform other popular machine learning algorithms (such as support vector machines) for both supervised and unsupervised tasks. Random forests are a powerful tool for unsupervised learning because they can handle high-dimensional data with many features. They also resist overfitting, meaning they generalize well to new data.
10. DBSCAN is a density-based clustering algorithm that can be used for unsupervised learning
It is based on density, that is, the number of points in each region. DBSCAN points points within a group if they are close together and ignores points if they are further apart. DBSCAN has some advantages compared to other clustering algorithms. It can find clusters of different sizes and shapes and does not require the user to specify the number of clusters in advance. Furthermore, DBSCAN is insensitive to outliers, which means it can be used to find data that is not well represented by other datasets. But DBSCAN also has some shortcomings. For example, it may have difficulty finding good clusters in a very noisy data set. The other thing is that DBSCAN requires a density threshold, which may not be applicable to all data sets.
11. The Apriori algorithm is used to find associations, frequent itemsets and sequential patterns
The Apriori algorithm is the first association rule mining algorithm and the most classic algorithm. It works by first finding all frequent itemsets in the data and then using these itemsets to generate rules.
There are many ways to implement the Apriori algorithm, which can be customized for different needs. For example, support and confidence thresholds can be controlled to find different types of rules.
12. The Eclat algorithm mines frequent item sets from transaction databases and can be used for shopping cart analysis, intrusion detection and text mining.
The Eclat algorithm is a depth-first algorithm that uses vertical data representation. , based on the concept lattice theory, the search space (concept lattice) is divided into smaller subspaces (sub-concept lattice) using the prefix-based equivalence relationship.
The above is the detailed content of Introduction to the 12 most important algorithms of unsupervised learning and a summary of their use cases. For more information, please follow other related articles on the PHP Chinese website!
 AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AM
AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AMThere were some very insightful perspectives in this speech—background information about engineering that showed us why artificial intelligence is so good at supporting people’s physical exercise. I will outline a core idea from each contributor’s perspective to demonstrate three design aspects that are an important part of our exploration of the application of artificial intelligence in sports. Edge devices and raw personal data This idea about artificial intelligence actually contains two components—one related to where we place large language models and the other is related to the differences between our human language and the language that our vital signs “express” when measured in real time. Alexander Amini knows a lot about running and tennis, but he still
 Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AM
Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AMCaterpillar's Chief Information Officer and Senior Vice President of IT, Jamie Engstrom, leads a global team of over 2,200 IT professionals across 28 countries. With 26 years at Caterpillar, including four and a half years in her current role, Engst
 New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AM
New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AMGoogle Photos' New Ultra HDR Tool: A Quick Guide Enhance your photos with Google Photos' new Ultra HDR tool, transforming standard images into vibrant, high-dynamic-range masterpieces. Ideal for social media, this tool boosts the impact of any photo,
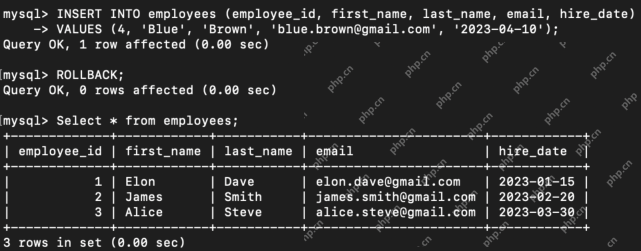 What are the TCL Commands in SQL? - Analytics VidhyaApr 22, 2025 am 11:07 AM
What are the TCL Commands in SQL? - Analytics VidhyaApr 22, 2025 am 11:07 AMIntroduction Transaction Control Language (TCL) commands are essential in SQL for managing changes made by Data Manipulation Language (DML) statements. These commands allow database administrators and users to control transaction processes, thereby
 How to Make Custom ChatGPT? - Analytics VidhyaApr 22, 2025 am 11:06 AM
How to Make Custom ChatGPT? - Analytics VidhyaApr 22, 2025 am 11:06 AMHarness the power of ChatGPT to create personalized AI assistants! This tutorial shows you how to build your own custom GPTs in five simple steps, even without coding skills. Key Features of Custom GPTs: Create personalized AI models for specific t
 Difference Between Method Overloading and OverridingApr 22, 2025 am 10:55 AM
Difference Between Method Overloading and OverridingApr 22, 2025 am 10:55 AMIntroduction Method overloading and overriding are core object-oriented programming (OOP) concepts crucial for writing flexible and efficient code, particularly in data-intensive fields like data science and AI. While similar in name, their mechanis
 Difference Between SQL Commit and SQL RollbackApr 22, 2025 am 10:49 AM
Difference Between SQL Commit and SQL RollbackApr 22, 2025 am 10:49 AMIntroduction Efficient database management hinges on skillful transaction handling. Structured Query Language (SQL) provides powerful tools for this, offering commands to maintain data integrity and consistency. COMMIT and ROLLBACK are central to t
 PySimpleGUI: Simplifying GUI Development in Python - Analytics VidhyaApr 22, 2025 am 10:46 AM
PySimpleGUI: Simplifying GUI Development in Python - Analytics VidhyaApr 22, 2025 am 10:46 AMPython GUI Development Simplified with PySimpleGUI Developing user-friendly graphical interfaces (GUIs) in Python can be challenging. However, PySimpleGUI offers a streamlined and accessible solution. This article explores PySimpleGUI's core functio


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

MantisBT
Mantis is an easy-to-deploy web-based defect tracking tool designed to aid in product defect tracking. It requires PHP, MySQL and a web server. Check out our demo and hosting services.

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

Dreamweaver CS6
Visual web development tools

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment





