Nine ways to use machine learning to launch attacks
Machine learning and artificial intelligence (AI) are becoming core technologies for some threat detection and response tools. Its ability to learn on the fly and automatically adapt to cyber threat dynamics empowers security teams.
However, some malicious hackers will also use machine learning and AI to expand their network attacks, circumvent security controls, and find new vulnerabilities at an unprecedented speed with devastating consequences. Common ways hackers exploit these two technologies are as follows.

1. Spam
Omida analyst Fernando Montenegro said that epidemic prevention personnel use machine learning technology Detecting spam has been around for decades. “Spam prevention is the most successful initial use case for machine learning.” You can adjust your behavior. They use legitimate tools to make their attacks more successful. "With enough submissions, you can recover what the model is, and then you can tailor your attack to bypass that model."
It's not just spam filters that are vulnerable . Any security vendor that provides a score or some other output is open to abuse. "Not everyone has this problem, but if you're not careful, someone will take advantage of this output."
2. More sophisticated phishing emails
Attackers don’t just use machine learning security tools to test whether their emails can pass spam filters. They also use machine learning to craft these emails. "They advertise these services on criminal forums. They use these techniques to generate more sophisticated phishing emails and create false personas to advance their scams," said Adam Malone, a partner at Ernst & Young's technology consulting firm.
#The use of machine learning is highlighted when advertising these services, and it may not just be marketing rhetoric, but reality. “You’ll know if you try it,” Malone said. “The effect is really good.”
Attackers can use machine learning to creatively customize phishing emails to prevent them from being Mark your email as spam to give targeted users a chance to click through. They customize more than just email text. Attackers will use AI to generate realistic-looking photos, social media profiles and other materials to make communications appear as authentic and trustworthy as possible.
3. More efficient password guessing
Cybercriminals also use machine learning to guess passwords. "We have evidence that they are using password guessing engines more frequently and with higher success rates." Cybercriminals are creating better dictionaries to crack stolen hashes.
They also use machine learning to identify security controls so that they can guess passwords with fewer attempts, increasing the probability of successfully breaching a system.
4. Deepfakes
The most alarming misuse of artificial intelligence is deepfake tools: generating video or audio that can look fake tool. "Being able to imitate other people's voices or looks is very effective in deceiving people." Montenegro said, "If someone pretends to be my voice, you will probably be tricked as well."
In fact, in the past few years, A series of major cases disclosed here show that fake audio can cost companies hundreds, thousands or even millions of dollars. "People will get calls from their bosses — and it's fake," said Murat Kantarcioglu, a professor of computer science at the University of Texas. More commonly, scammers use AI generates photos, user profiles, and phishing emails that look authentic, making their emails look more trustworthy. This is big business. According to an FBI report, business email fraud has resulted in losses of more than $43 billion since 2016. Last fall, media reported that a bank in Hong Kong was defrauded into transferring $35 million to a criminal gang simply because a bank employee received a call from a company director whom he knew. He recognized the director's voice and authorized the transfer without question.
5. Neutralize off-the-shelf security tools
Many security tools commonly used today have some form of artificial intelligence or machine learning built into them. For example, antivirus software relies on more than basic signatures when looking for suspicious behavior. "Anything available on the Internet, especially open source, can be exploited by bad actors."
Attackers can use these tools, not to defend against attacks, but to adjust themselves of malware until detection can be bypassed. "AI models have many blind spots." Kantarcioglu said, "You can adjust it by changing the characteristics of the attack, such as the number of packets sent, the resources of the attack, etc."
Moreover, attackers are leveraging more than just AI-powered security tools. AI is just one of a bunch of different technologies. For example, users can often learn to identify phishing emails by looking for grammatical errors. And AI-powered grammar checkers, like Grammarly, can help attackers improve their writing.
6. Reconnaissance
Machine learning can be used for reconnaissance, allowing attackers to view a target’s traffic patterns, defenses, and potential vulnerabilities. Reconnaissance is not an easy task and is beyond the reach of ordinary cybercriminals. "If you want to use AI for reconnaissance, you have to have certain skills. So, I think that only advanced state hackers will use these technologies."
However, once to a certain extent, Once it is commercialized and this technology is provided as a service through the underground black market, many people can take advantage of it. “This could also happen if a hacker nation-state develops a toolkit that uses machine learning and releases it to the criminal community,” Mellen said. “But cybercriminals still need to understand the role and effectiveness of machine learning applications. The method of exploitation, this is the threshold for exploitation."
7. Autonomous Agent
If the enterprise finds that it is under attack, disconnect the affected system's Internet connection, the malware may not be able to connect back to its command and control (C2) server to receive further instructions. "An attacker may want to develop an intelligent model that can persist for a long time even if it cannot be directly controlled." Kantarcioglu said, "But for ordinary cybercrime, I don't think this is particularly important."
8. AI Poisoning
An attacker can trick a machine learning model by feeding it new information. Alexey Rubtsov, senior associate researcher at the Global Risk Institute, said: "Adversaries can manipulate training data sets. For example, they deliberately bias the model so that the machine learns the wrong way."
For example For example, a hacker can manipulate a hijacked user account to log in to the system at 2 a.m. every day to perform harmless work, causing the system to think that there is nothing suspicious about working at 2 a.m., thus reducing the security levels that users must pass.
The Microsoft Tay chatbot was taught to be racist in 2016 for a similar reason. The same approach can be used to train a system to think that a specific type of malware is safe, or that a specific crawler behavior is completely normal.
9. AI Fuzz Testing
Legitimate software developers and penetration testers use fuzz testing software to generate random sample inputs in an attempt to crash the application program or find loopholes. Enhanced versions of this type of software use machine learning to generate input in a more targeted and organized manner, such as prioritizing text strings most likely to cause problems. This type of fuzz testing tool can achieve better testing results when used by enterprises, but it is also more deadly in the hands of attackers.
These techniques are among the reasons why cybersecurity approaches such as security patches, anti-phishing education, and micro-segmentation remain vital. "That's one of the reasons why defense in depth is so important," said Forrester's Mellen. "You have to put up multiple roadblocks, not just the one that attackers can use against you."
Lack of expertise hinders malicious hackers from exploiting machine learning and AI
Investing in machine learning requires a lot of expertise, and machine learning-related expertise is currently scarce Skill. And, because many vulnerabilities remain unpatched, there are many easy ways for attackers to break through corporate defenses.
“There are a lot of low-hanging fruit, and there are a lot of other ways to make money without using machine learning and artificial intelligence to launch attacks.” Mellen said, “In my experience, "In the vast majority of cases, attackers do not utilize these techniques." However, as enterprise defenses improve and cybercriminals and hacker nations continue to invest in attack development, the balance may soon begin to shift.
The above is the detailed content of Nine ways to use machine learning to launch attacks. For more information, please follow other related articles on the PHP Chinese website!
 The AI Skills Gap Is Slowing Down Supply ChainsApr 26, 2025 am 11:13 AM
The AI Skills Gap Is Slowing Down Supply ChainsApr 26, 2025 am 11:13 AMThe term "AI-ready workforce" is frequently used, but what does it truly mean in the supply chain industry? According to Abe Eshkenazi, CEO of the Association for Supply Chain Management (ASCM), it signifies professionals capable of critic
 How One Company Is Quietly Working To Transform AI ForeverApr 26, 2025 am 11:12 AM
How One Company Is Quietly Working To Transform AI ForeverApr 26, 2025 am 11:12 AMThe decentralized AI revolution is quietly gaining momentum. This Friday in Austin, Texas, the Bittensor Endgame Summit marks a pivotal moment, transitioning decentralized AI (DeAI) from theory to practical application. Unlike the glitzy commercial
 Nvidia Releases NeMo Microservices To Streamline AI Agent DevelopmentApr 26, 2025 am 11:11 AM
Nvidia Releases NeMo Microservices To Streamline AI Agent DevelopmentApr 26, 2025 am 11:11 AMEnterprise AI faces data integration challenges The application of enterprise AI faces a major challenge: building systems that can maintain accuracy and practicality by continuously learning business data. NeMo microservices solve this problem by creating what Nvidia describes as "data flywheel", allowing AI systems to remain relevant through continuous exposure to enterprise information and user interaction. This newly launched toolkit contains five key microservices: NeMo Customizer handles fine-tuning of large language models with higher training throughput. NeMo Evaluator provides simplified evaluation of AI models for custom benchmarks. NeMo Guardrails implements security controls to maintain compliance and appropriateness
 AI Paints A New Picture For The Future Of Art And DesignApr 26, 2025 am 11:10 AM
AI Paints A New Picture For The Future Of Art And DesignApr 26, 2025 am 11:10 AMAI: The Future of Art and Design Artificial intelligence (AI) is changing the field of art and design in unprecedented ways, and its impact is no longer limited to amateurs, but more profoundly affecting professionals. Artwork and design schemes generated by AI are rapidly replacing traditional material images and designers in many transactional design activities such as advertising, social media image generation and web design. However, professional artists and designers also find the practical value of AI. They use AI as an auxiliary tool to explore new aesthetic possibilities, blend different styles, and create novel visual effects. AI helps artists and designers automate repetitive tasks, propose different design elements and provide creative input. AI supports style transfer, which is to apply a style of image
 How Zoom Is Revolutionizing Work With Agentic AI: From Meetings To MilestonesApr 26, 2025 am 11:09 AM
How Zoom Is Revolutionizing Work With Agentic AI: From Meetings To MilestonesApr 26, 2025 am 11:09 AMZoom, initially known for its video conferencing platform, is leading a workplace revolution with its innovative use of agentic AI. A recent conversation with Zoom's CTO, XD Huang, revealed the company's ambitious vision. Defining Agentic AI Huang d
 The Existential Threat To UniversitiesApr 26, 2025 am 11:08 AM
The Existential Threat To UniversitiesApr 26, 2025 am 11:08 AMWill AI revolutionize education? This question is prompting serious reflection among educators and stakeholders. The integration of AI into education presents both opportunities and challenges. As Matthew Lynch of The Tech Edvocate notes, universit
 The Prototype: American Scientists Are Looking For Jobs AbroadApr 26, 2025 am 11:07 AM
The Prototype: American Scientists Are Looking For Jobs AbroadApr 26, 2025 am 11:07 AMThe development of scientific research and technology in the United States may face challenges, perhaps due to budget cuts. According to Nature, the number of American scientists applying for overseas jobs increased by 32% from January to March 2025 compared with the same period in 2024. A previous poll showed that 75% of the researchers surveyed were considering searching for jobs in Europe and Canada. Hundreds of NIH and NSF grants have been terminated in the past few months, with NIH’s new grants down by about $2.3 billion this year, a drop of nearly one-third. The leaked budget proposal shows that the Trump administration is considering sharply cutting budgets for scientific institutions, with a possible reduction of up to 50%. The turmoil in the field of basic research has also affected one of the major advantages of the United States: attracting overseas talents. 35
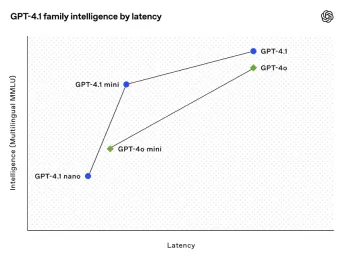 All About Open AI's Latest GPT 4.1 Family - Analytics VidhyaApr 26, 2025 am 10:19 AM
All About Open AI's Latest GPT 4.1 Family - Analytics VidhyaApr 26, 2025 am 10:19 AMOpenAI unveils the powerful GPT-4.1 series: a family of three advanced language models designed for real-world applications. This significant leap forward offers faster response times, enhanced comprehension, and drastically reduced costs compared t


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

Atom editor mac version download
The most popular open source editor

Notepad++7.3.1
Easy-to-use and free code editor

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),







