 Technology peripherals
Technology peripherals AI
AI Artificial intelligence is ready to take off, security meets opportunities and challenges
Artificial intelligence is ready to take off, security meets opportunities and challengesArtificial intelligence is ready to take off, security meets opportunities and challenges
In recent years, with the improvement of its status, artificial intelligence has attracted more and more attention from the country. In July 2015, "artificial intelligence" was included in the "Guiding Opinions of the State Council on Actively Promoting the "Internet" Action"; in March 2016, the term "artificial intelligence" was included in the "13th Five-Year Plan" outline; in May 2016 In March, four departments including the National Development and Reform Commission jointly issued the "Three-Year Action Plan for "Internet" Artificial Intelligence"; in March 2017, "artificial intelligence" was included in the government work report. It can be said that artificial intelligence has reached a new height in promoting economic development, and many artificial intelligence concept stocks also performed well during the two sessions.
The "Artificial Intelligence Development Report 2016" shows that China's total number of artificial intelligence applications has reached 15,745, ranking second; investment in the field of artificial intelligence ranks third. It can be expected that in the next 5 to 10 years, artificial intelligence will be like water and electricity*, and a new era of "artificial intelligence" is coming.

Some analysts mentioned that the three to five years starting from 2017 will be the peak period when a large number of artificial intelligence professionals graduate and begin to enter the industry. The introduction of artificial intelligence technology into various industries brings huge opportunities. From an industrial point of view, the next few years will also be a period when artificial intelligence will fully penetrate into big data industries such as finance, medical care, education, and sensory interaction fields. Security, finance, medical care, automobiles, education, information security, retail and other industries are more electronic. The data is high, the data is concentrated and the data quality is high, so a large number of artificial intelligence scenario applications will emerge in these industries.
Those value stocks with stable profitability, clear business models, and reasonable valuations are naturally more popular. When making relevant thematic investment stock selections, you can consider it from three levels: first, continued policy support, second, technological innovation driving profit enhancement, and third, business model innovation. Observed from this point of view, it is not surprising that because artificial intelligence is in the rapid development period of the industry and because of its huge role in improving economic efficiency, it has received high support from policies and received focus from various institutions.
Looking again, there are some catalysts that may appear in the near future: First, the artificial intelligence plan is expected to be released in the near future; in addition, the 2017 IT Summit will be held on April 1, and the theme of the conference is "Moving into the New Era of Intelligence" "; Ke Jie and other human chess players will compete against AlphaGo again in April, etc. These are all factors that continue to catalyze the development of artificial intelligence.
What does artificial intelligence mean to security?
The development of artificial intelligence has certainly attracted the attention of the security industry. As one of the important application areas in the IT industry, the application of artificial intelligence in the security industry has a certain foundation. Even at the 215th IT Gantry Array hosted by TechWeb on March 14, Zhao Yong, founder of Gelin Shen Tong, also said that security monitoring must be the first area where artificial intelligence will generate commercial value on a large scale. This can already be seen in 2016. It can be seen that 2017 will be at least 10 times more than last year.
In fact, with the development of artificial intelligence technology, with video content analysis and recognition technology as the core, through structured description of unstructured data, condensed and summarized information is extracted to achieve rapid retrieval and search. , and carrying out big data analysis and information collision through thinking similar to the human brain are currently hot topics in the security industry.
According to industry forecasts, through big data technology, different types of data such as videos, pictures, WIFI signals, and electronic license plates can be analyzed, collided, potential connections discovered, valuable information extracted, and visualized. The results show that artificial intelligence will be applied in the following security fields:
Personnel analysis application relies on the results output by the artificial intelligence system's personnel characteristic identification service to conduct data analysis to realize personnel identification, personnel deployment, personnel deployment, and personnel identification. Face tracking and other functions.
The vehicle analysis application can meet the needs of full map operations and realize visual applications, including: trajectory analysis, car following analysis, collision analysis, frequency analysis, deck analysis, hidden vehicle mining and other functions.
Multi-resource spatio-temporal application can be based on the command and dispatch of GIS maps, realize the integrated management of various video resources through the geographical information system, and realize the intuitive visualization application of monitoring images. Achieve quick retrieval of images of monitoring points or monitoring areas that need attention, and achieve online tracking of targets. Through video layer overlay, video resource search and video positioning, road conditions, resource distribution, personnel distribution, geographical coordinate information, and police deployment are displayed in a graphical form to intuitively display global information in a comprehensive and multi-dimensional manner. , making command and dispatch more intuitive.
View content warning and automatic warning linkage application to automatically warn the content of the video. When the pre-set plan is triggered, the linked cameras will open the surveillance images at the same time, forming a surveillance blockade of the crime scene and alarming in real time. The control intelligent rule analysis functions include: regional intrusion, tripwire detection, illegal parking, loitering detection, fight detection, items, item loss, illegal tailgating, crowd gathering, traffic flow statistics, license plate feature recognition, fireworks detection, etc.
Video real-time annotation application can use real-time video for real-time structuring, including feature extraction of people, vehicles, and moving targets. Real-time video annotation converts video data into intelligence used by public security in actual combat, realizing the transformation of video data into information , transformation of information.
Facial portrait comparison and search application can compare suspects, quickly confirm the identity of the target, and provide intelligent, fast face comparison and complete video image big data analysis and mining applications. Comprehensive solution to personnel management and monitoring problems such as real-time portrait tracking, monitoring and early warning, rapid identification of personnel, retrieval and approval, personnel historical trajectory tracking and retrieval, etc.
The video image intelligent analysis and judgment application can use image processing algorithms suitable for various scenes and situations on videos and pictures in various formats to achieve clear processing of blurred images. It also provides video intelligent annotation services and retrieval services to achieve intelligent (the system automatically extracts description information) structured descriptions of suspect targets in videos and pictures, reducing the workload of manual annotation of entered structured description information, and meeting a variety of searches at the same time. This method improves the speed and efficiency of video viewing, achieves the purpose of quickly finding and locating suspect targets, and reduces the possibility of missing suspect target information in incident videos.
Vehicle data collision mining application can perform secondary identification of vehicle data in bayonet pictures, including license plate number, vehicle brand, vehicle sub-brand, vehicle year, vehicle color, license plate color, vehicle type, and license plate type , annual inspection standards, sun visors, seat belts and other detailed vehicle information, and conduct data collision and comparison on the vehicle's operating trajectory, activity patterns, etc., so as to mine hidden clues of the case and implement visual applications. The functions include: trajectory analysis, car following analysis , collision analysis, frequency analysis, deck analysis, hidden vehicle mining, etc.
The vehicle real-time deployment and control application can be used to target stolen vehicles, illegal vehicles, vehicles involved in crimes, high-risk personnel vehicles, key vehicles, etc., by analyzing the characteristic attributes of specific moving target objects (such as license plate number, model, color, space, etc.) area, etc.) and their combinations to perform online real-time deployment and control functions.
How to integrate artificial intelligence into security?
These are the advancement and diversification development trends shown by the security video surveillance market under the integration of cutting-edge technologies such as artificial intelligence. Future industry development, centered on the business development of video surveillance, will present a trend of integration of text, picture, geographical space and other information videoization and video data structuring, which will be brought about by the certainty of the development of security technology and the diversified development of business. The uncertain environment will bring opportunities and challenges to security companies in market competition.
From a technical perspective, the reason for promoting the development of intelligent security is the maturity of artificial intelligence in the fields of algorithms and chips and the decline in costs, which has made the commercialization of intelligence more popular. At the market level, the situation in which surveillance intelligence is flourishing is the result of the market seeking differentiated competition. In the future development and changes of the intelligent surveillance market, the popularization of high-definition will be a very critical link. Only when the collection end obtains high-definition video data sources can targeted analysis of events in the monitored area be carried out.
To this end, in the process surrounding the entire intelligent development of security, it is the ecological evolution of the entire industry chain from collection to processing, transmission, storage, and analysis. The evolution of this industry is to drive the upgrading of equipment and systems. motivation. In this process, mainstream equipment solution providers have made great efforts to deploy and achieved good results in actual combat. The industry threshold for this particular application may bring greater shock to the market structure.
The above is the detailed content of Artificial intelligence is ready to take off, security meets opportunities and challenges. For more information, please follow other related articles on the PHP Chinese website!
 The AI Skills Gap Is Slowing Down Supply ChainsApr 26, 2025 am 11:13 AM
The AI Skills Gap Is Slowing Down Supply ChainsApr 26, 2025 am 11:13 AMThe term "AI-ready workforce" is frequently used, but what does it truly mean in the supply chain industry? According to Abe Eshkenazi, CEO of the Association for Supply Chain Management (ASCM), it signifies professionals capable of critic
 How One Company Is Quietly Working To Transform AI ForeverApr 26, 2025 am 11:12 AM
How One Company Is Quietly Working To Transform AI ForeverApr 26, 2025 am 11:12 AMThe decentralized AI revolution is quietly gaining momentum. This Friday in Austin, Texas, the Bittensor Endgame Summit marks a pivotal moment, transitioning decentralized AI (DeAI) from theory to practical application. Unlike the glitzy commercial
 Nvidia Releases NeMo Microservices To Streamline AI Agent DevelopmentApr 26, 2025 am 11:11 AM
Nvidia Releases NeMo Microservices To Streamline AI Agent DevelopmentApr 26, 2025 am 11:11 AMEnterprise AI faces data integration challenges The application of enterprise AI faces a major challenge: building systems that can maintain accuracy and practicality by continuously learning business data. NeMo microservices solve this problem by creating what Nvidia describes as "data flywheel", allowing AI systems to remain relevant through continuous exposure to enterprise information and user interaction. This newly launched toolkit contains five key microservices: NeMo Customizer handles fine-tuning of large language models with higher training throughput. NeMo Evaluator provides simplified evaluation of AI models for custom benchmarks. NeMo Guardrails implements security controls to maintain compliance and appropriateness
 AI Paints A New Picture For The Future Of Art And DesignApr 26, 2025 am 11:10 AM
AI Paints A New Picture For The Future Of Art And DesignApr 26, 2025 am 11:10 AMAI: The Future of Art and Design Artificial intelligence (AI) is changing the field of art and design in unprecedented ways, and its impact is no longer limited to amateurs, but more profoundly affecting professionals. Artwork and design schemes generated by AI are rapidly replacing traditional material images and designers in many transactional design activities such as advertising, social media image generation and web design. However, professional artists and designers also find the practical value of AI. They use AI as an auxiliary tool to explore new aesthetic possibilities, blend different styles, and create novel visual effects. AI helps artists and designers automate repetitive tasks, propose different design elements and provide creative input. AI supports style transfer, which is to apply a style of image
 How Zoom Is Revolutionizing Work With Agentic AI: From Meetings To MilestonesApr 26, 2025 am 11:09 AM
How Zoom Is Revolutionizing Work With Agentic AI: From Meetings To MilestonesApr 26, 2025 am 11:09 AMZoom, initially known for its video conferencing platform, is leading a workplace revolution with its innovative use of agentic AI. A recent conversation with Zoom's CTO, XD Huang, revealed the company's ambitious vision. Defining Agentic AI Huang d
 The Existential Threat To UniversitiesApr 26, 2025 am 11:08 AM
The Existential Threat To UniversitiesApr 26, 2025 am 11:08 AMWill AI revolutionize education? This question is prompting serious reflection among educators and stakeholders. The integration of AI into education presents both opportunities and challenges. As Matthew Lynch of The Tech Edvocate notes, universit
 The Prototype: American Scientists Are Looking For Jobs AbroadApr 26, 2025 am 11:07 AM
The Prototype: American Scientists Are Looking For Jobs AbroadApr 26, 2025 am 11:07 AMThe development of scientific research and technology in the United States may face challenges, perhaps due to budget cuts. According to Nature, the number of American scientists applying for overseas jobs increased by 32% from January to March 2025 compared with the same period in 2024. A previous poll showed that 75% of the researchers surveyed were considering searching for jobs in Europe and Canada. Hundreds of NIH and NSF grants have been terminated in the past few months, with NIH’s new grants down by about $2.3 billion this year, a drop of nearly one-third. The leaked budget proposal shows that the Trump administration is considering sharply cutting budgets for scientific institutions, with a possible reduction of up to 50%. The turmoil in the field of basic research has also affected one of the major advantages of the United States: attracting overseas talents. 35
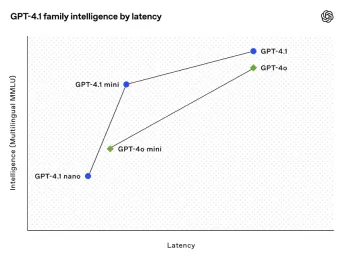 All About Open AI's Latest GPT 4.1 Family - Analytics VidhyaApr 26, 2025 am 10:19 AM
All About Open AI's Latest GPT 4.1 Family - Analytics VidhyaApr 26, 2025 am 10:19 AMOpenAI unveils the powerful GPT-4.1 series: a family of three advanced language models designed for real-world applications. This significant leap forward offers faster response times, enhanced comprehension, and drastically reduced costs compared t


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

WebStorm Mac version
Useful JavaScript development tools

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

EditPlus Chinese cracked version
Small size, syntax highlighting, does not support code prompt function

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

SublimeText3 English version
Recommended: Win version, supports code prompts!






