Home >Web Front-end >Front-end Q&A >what is html injection
what is html injection
- 青灯夜游Original
- 2021-06-21 11:27:216477browse
HTML injection is a vulnerability, a type of network attack that occurs when a web page fails to sanitize user-supplied input or validate output. This allows an attacker to forge their own payload and pass it through a vulnerable field. Malicious HTML code is injected into the application to modify the content of the web page and even obtain some sensitive data.

The operating environment of this tutorial: Windows 7 system, HTML5 version, Dell G3 computer.
What is HTML injection?
HTML injection (Hypertext Markup Language Injection) Chinese means "Hypertext Markup Language Injection". As we all know, HTML contains various tags. If the web application does not thoroughly process the data input by the user, If so, then some data submitted by illegal users may contain other HTML tags, and these data happen to be displayed by the server as normal HTML tags, then the final result is that the illegal tags are parsed (can be applied to phishing, social engineering, etc.) , causing a great impact on other users.
An attacker can forge his own payload and inject malicious HTML code into the application through vulnerable fields, thereby modifying the content of the web page and even obtaining some sensitive data.
The difference between HTML injection and XSS
The Chinese translation of XSS (Cross-site Scripting) is "cross-site scripting attack". XSS is essentially an HTML injection attack, but Different from HTML injection, XSS uses script tags to run JavaScript and other script programs, and can obtain confidential data and a series of dangerous operations through JavaScript, while HTML injection only uses HTML tags to modify page content.
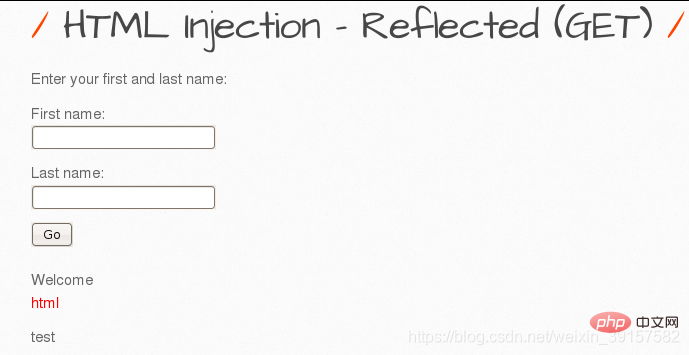
HTML Injection - Reflected (GET)
Reflected HTML Injection (GET method)
First name fill inhtml, fill in test as Last name, and find that the html letters turn red, indicating that the html code we wrote was successfully executed, and there is html injection on this website.
HTML Injection - Reflected (POST)
Reflected HTML Injection (POST method)
Note: After submitting data in GET method, the submitted data will be displayed in the browser address bar, but not in POST.
Same as the GET method above
First name is filled in
html2
, Last name is filled in test, and the letters html2 are found to turn green, indicating that we write The entered html code was executed successfully, and there is html injection in this website. 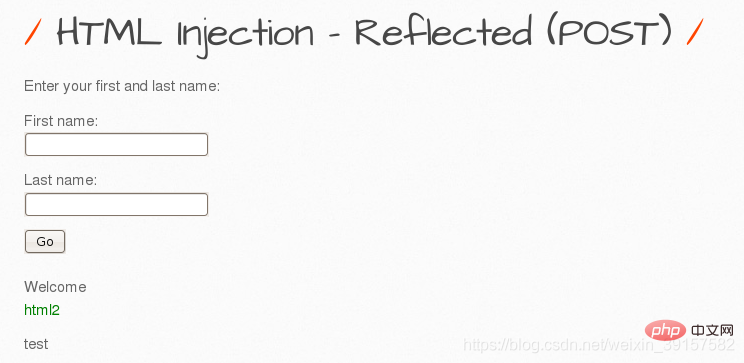
HTML Injection - Reflected (Current URL)
Reflected HTML Injection (Current URL)
First, let’s analyze the source code
Core code
<div> <h1>HTML Injection - Reflected (URL)</h1> <?php echo "<p align=\"left\">Your current URL: <i>" . $url . "</i>";?> </div>
There is a piece of PHP code in this code, which executes the html statement and outputs a piece of "Your current URL:" characters, and call the $url variable to follow the output content.
Protection code
$url= "";
switch($_COOKIE["security_level"])
{
case "0" :
// $url = "http://" . $_SERVER["HTTP_HOST"] . urldecode($_SERVER["REQUEST_URI"]);
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"]; //$url= ''接受的参数来自请求头HOST和URL
break;
case "1" :
$url = "<script>document.write(document.URL)</script>";
break;
case "2" :
$url = "http://" . $_SERVER["HTTP_HOST"] . xss_check_3($_SERVER["REQUEST_URI"]);
break;
default :
// $url = "http://" . $_SERVER["HTTP_HOST"] . urldecode($_SERVER["REQUEST_URI"]);
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"];
break;
}
<select name="security_level">
<option value="0">low</option>
<option value="1">medium</option>
<option value="2">high</option>
</select>Reading the defense code, you can understand that the defense code called is different depending on the difficulty of the setting.
(1) LOW
When setting the level to Low, execute the following statement
$url = "http://" . $_SERVER["HTTP_HOST"] . $_SERVER["REQUEST_URI"];
$_SERVER here ["HTTP_HOST"] means to get the current domain name
Here $_SERVER["REQUEST_URI"]" is to get the complete address path behind the domain name
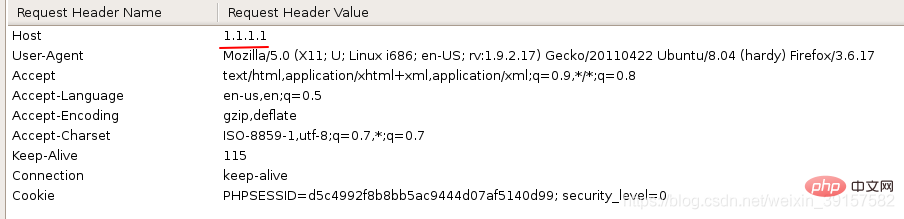
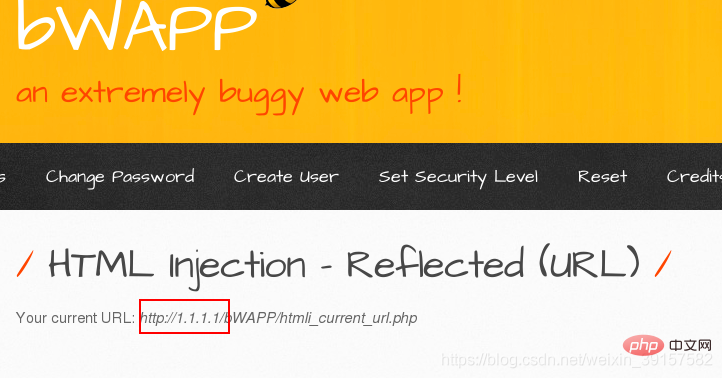
You can find out by modifying the host parameter through burp packet capture Changes have occurred on the page
(2) medium
When setting the level to medium, execute The following statement
$url = "<script>document.write(document.URL)</script>";
The document object here represents the entire HTML document and can be used to access all elements in the page;
document.write() is dynamic Write content to the page
document.URL is to set the URL attribute to open another page in the same window
(3) high
will level When set to high, execute the following statement
$url = "http://" . $_SERVER["HTTP_HOST"] . xss_check_3($_SERVER["REQUEST_URI"]);
The xss_check_3 function is called here to filter the part behind the host, making it impossible to inject.
HTML Injection - Stored (Blog)
Stored HTML Injection
Note: The reflective page will no longer exist after refreshing, while the storage type is written to the server database and will still exist after refreshing. HTML
Therefore, the storage type is much more harmful than the reflection type.
Enter 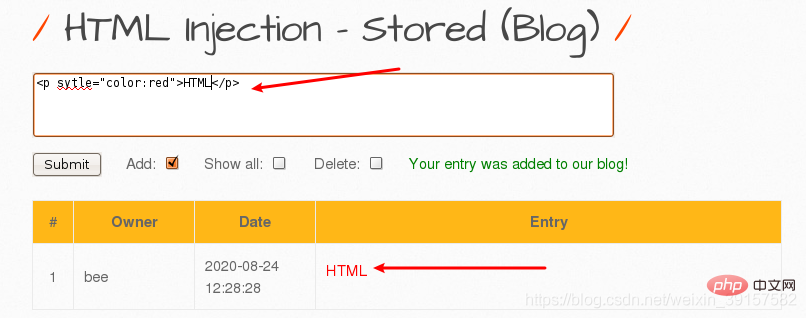
Recommended tutorial: "html video tutorial"
The above is the detailed content of what is html injection. For more information, please follow other related articles on the PHP Chinese website!

