Home >Database >Mysql Tutorial >What is the injection error of mysql statement?
What is the injection error of mysql statement?
- 青灯夜游Original
- 2020-10-20 14:18:572474browse
The injection error of mysql statement is to use the external interface of some databases to insert user data into the actual SQL language, thereby achieving the purpose of invading the database and even the operating system. Attackers use it to read, modify or delete data in the database, obtain user information, passwords and other information in the database, or more seriously, gain administrator privileges.

(Recommended tutorial: mysql video tutorial)
SQL injection error(SQL injection)
SQL Injection is to use the external interface of certain databases to insert user data into the actual database operating language (SQL), thereby achieving the purpose of invading the database and even the operating system. It occurs mainly because the program does not strictly filter the data input by the user, resulting in the execution of illegal database query statements.
"MySQL in simple terms"
Hazards
Attackers use it to read, modify or delete data in the database, and obtain user information and passwords in the database, etc. information, and more seriously, obtaining administrator privileges.
Example
//注入式错误
public static void test3(String name,String passward){
Connection connection = null;
Statement st = null;
ResultSet rs = null;
try {
// 加载JDBC 驱动
Class.forName("com.mysql.jdbc.Driver");
// 获得JDBC 连接
String url = "jdbc:mysql://localhost:3306/tulun";
connection = DriverManager.getConnection(url,"root","123456");
//创建一个查询语句
st = connection.createStatement();
//sql语句
String sql = "select * from student where name = '"+ name+"' and passward = '"+passward+"'";
rs = st.executeQuery(sql);
if(rs.next()){
System.out.println("登录成功。");
}else{
System.out.println("登录失败。");
}
} catch (Exception e) {
e.printStackTrace();
}
}
public static void main(String[] args) {
test3("wjm3' or '1 = 1","151515");
}
Database information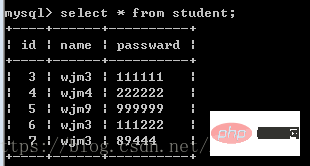 ## As shown in the above code, the user name is wjm3' or '1 = 1, the password is 151515. It can be seen from the database that we do not have such a user. It should have shown a login failure, but the result was a successful login, because or '1 = 1 is no longer the content of the user name. It Now it is the content in the SQL statement. No matter what, the result is true, which means you can log in without entering a password. A security issue arises here.
## As shown in the above code, the user name is wjm3' or '1 = 1, the password is 151515. It can be seen from the database that we do not have such a user. It should have shown a login failure, but the result was a successful login, because or '1 = 1 is no longer the content of the user name. It Now it is the content in the SQL statement. No matter what, the result is true, which means you can log in without entering a password. A security issue arises here.
1. PrepareStatement
//注入式错误
public static void test3(String name,String passward){
Connection connection = null;
PreparedStatement st = null;
ResultSet rs = null;
try {
// 加载JDBC 驱动
Class.forName("com.mysql.jdbc.Driver");
// 获得JDBC 连接
String url = "jdbc:mysql://localhost:3306/tulun";
connection = DriverManager.getConnection(url,"root","123456");
//创建一个查询语句
String sql1 = "select * from student where name = ? and passward = ?";
st = connection.prepareStatement(sql1);
st.setString(1,name);
st.setString(2,passward);
//sql语句
//String sql = "select * from student where name = '"+ name+"' and passward = '"+passward+"'";
rs = st.executeQuery();
if(rs.next()){
System.out.println("登录成功。");
}else{
System.out.println("登录失败。");
}
} catch (Exception e) {
e.printStackTrace();
}finally{
try {
connection.close();
st.close();
rs.close();
} catch (SQLException e) {
e.printStackTrace();
}
}
}
public static void main(String[] args) {
test3("wjm3' or '1 = 1","151515");
}No matter what the name parameter is in the above code, it is only the name parameter and will not be used as a sql statement This method is generally recommended as it is safer.
2. Define your own function for verification
- Organize the data to make it valid
- Reject known illegal input
- Only accept known legal input
So if you want to obtain the best security status, the best solution at present is to simply classify the data submitted by the user or that may change, Regular expressions are applied respectively to strictly detect and validate the input data provided by the user.In fact, you only need to filter illegal symbol combinations to prevent known forms of attacks, and if newer attack symbol combinations are discovered, these symbol combinations can also be added to continue to prevent new attacks. In particular, the space symbol and the symbol that separates keywords have the same effect, such as "/**/". If this symbol can be successfully filtered, then many injection attacks will not occur, and at the same time they must also be filtered. The hexadecimal representation is "%XX".
The above is the detailed content of What is the injection error of mysql statement?. For more information, please follow other related articles on the PHP Chinese website!
Related articles
See more- What are the benefits of using mysql's case method?
- What is the usage of mysql aggregate function?
- Online slow query accident caused by wrong index selection in MySQL
- What are the connection queries for mysql tables?
- How to convert string to uppercase in mysql?
- What should I do if there is an error in adding a partition in mysql?
- What should I do if I forget to change mysql password on Linux?
- How to batch modify the character set of mysql table

