Strengthening home WiFi security: Responding to growing cyber threats

With the popularity of remote work, attacks on home WiFi networks are becoming increasingly rampant, as home networks often store a lot of valuable and sensitive information, and home WiFi security settings are often not enough to deal with these threats. Whether you are a business owner with remote employees, a freelancer working from home, or a regular home user, you need to take steps to ensure your network security.
What security threats does home WiFi face?
Many people think that home WiFi is safer than public WiFi, but that is not necessarily true. Unless you take appropriate security measures, your home network is as vulnerable to attacks as WiFi in public places. Many people have never changed the default settings of their routers, nor have they set complex passwords, enable encryption, filter unknown devices, or use virtual private networks (VPNs).
The following guides will help you improve your home WiFi security:
1. Reset the router to factory settings
First, reset the router to factory settings and clear all custom settings. This removes outdated WiFi security types, closes unnecessary network ports, and changes default login credentials. This step is especially important if you purchased a router from someone else. The reset method varies by router model, please refer to your router manual. It is usually necessary to hold the reset button for about 30 seconds, then wait for 30 seconds before restarting the router.
2. Create a unique username and password
Most routers use "admin" by default as username, which is easily guessed by hackers. Be sure to change the default username and create a strong password. You can use the password manager to generate a long and complex password containing letters, numbers and special characters.
3. Enable a secure WiFi network for visitors
Create a separate WiFi network for visitors, which can effectively isolate the visitor's device and prevent malware from infecting your primary network. Most routers support creating multiple WiFi networks.
4. Use the latest WPA network encryption
Choose the latest WPA network encryption protocol, such as WPA2 or WPA3 (if your router supports it). Avoid outdated WEP encryption.
5. Hide your WiFi network
Hide your SSID (Service Set Identifier) can increase security because only people who know the SSID and password can connect to your WiFi.

6. Filter unknown MAC addresses
Only known devices are allowed to connect to your WiFi network. You can add the MAC address of all devices to the router's allow list. How to find MAC addresses on your Mac: System Preferences ➙ Network ➙ Advanced ➙ Hardware Tab.

7. Limit wireless devices via IP
You can limit the number of devices connected to the network by limiting the size of the DHCP pool.
8. Using a Virtual Private Network (VPN)
Using a VPN can encrypt your connection and prevent data from being stolen. ClearVPN is a recommended VPN client that offers multiple connectivity options and powerful security features.

9. Improve the quality of WiFi connection
Using WiFi analysis tools such as WiFi Explorer and NetSpot, you can monitor WiFi connection quality and optimize the placement of your router to improve WiFi signal strength and coverage.


Through the above steps, you can effectively improve the security of your home WiFi network and enjoy faster and more stable network connections. Tools like ClearVPN, WiFi Explorer, and NetSpot can help you get these settings easier.
The above is the detailed content of How To Secure WiFi Network At Home – Setapp. For more information, please follow other related articles on the PHP Chinese website!
 How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AM
How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AMThe MacOS Sequoia public beta program is now available, providing Mac users with an early chance to explore the new major MacOS system software update. However, it's important to note that, like all beta versions, MacOS Sequoia public beta may be mor
 How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AM
How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AMInterested in running Ubuntu Linux on your Apple Silicon Mac? It's now simpler than ever to run Ubuntu alongside MacOS without the hassle of partitioning, dual booting, or risking your Mac's operating system. Thanks to virtual machine technology, you
 How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AM
How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AMThere are multiple methods to track CPU usage on a Mac, with the most popular being Activity Monitor for the graphical interface and htop or top for command line users. While Activity Monitor can display an optional core graph and htop shows CPU core
 chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AM
chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AMSome Mac users occasionally find that the "chronod" process in MacOS either consumes a lot of system resources or requests access to a network connection. Sometimes, chronods are also marked by overly alert antivirus applications. While many people will ignore this situation, there are also curious Mac users who actively explore what specific processes that consume a lot of resources are, or what the intentions are of a process that requires or requires Internet access. So, what is chronod on Mac? Why does it use high CPU and system resources? Why does it require network access? Let's dive into the chronod process to better understand its functionality. What is chronod? The chronod process is
 Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AM
Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AMWhat is Security Agent on MacSecurity Agent on Mac functions as a background process responsible for managing user authentication, system security notifications, and requests for application permissions. It collaborates with macOS's Security Server t
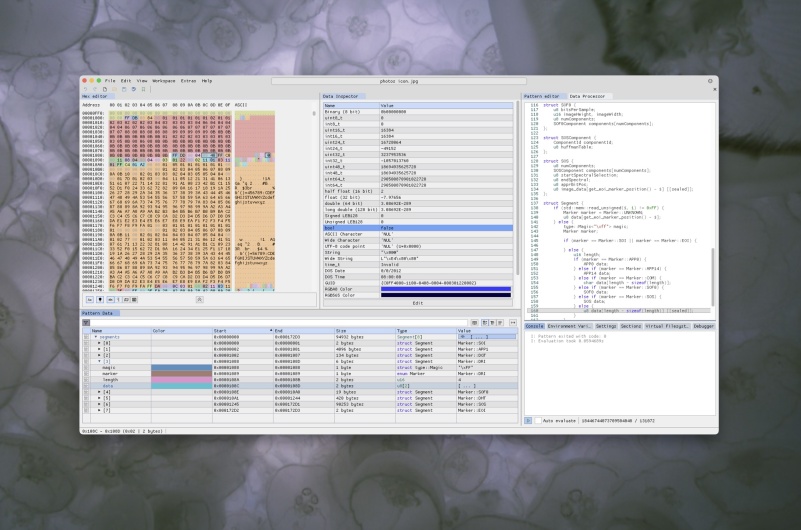 2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AM
2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AMHex editors are specialized software tools designed for viewing and editing hexadecimal data as well as raw binary data within files. These tools are indispensable for programmers, developers, and reverse engineers who need to inspect, debug, and ana
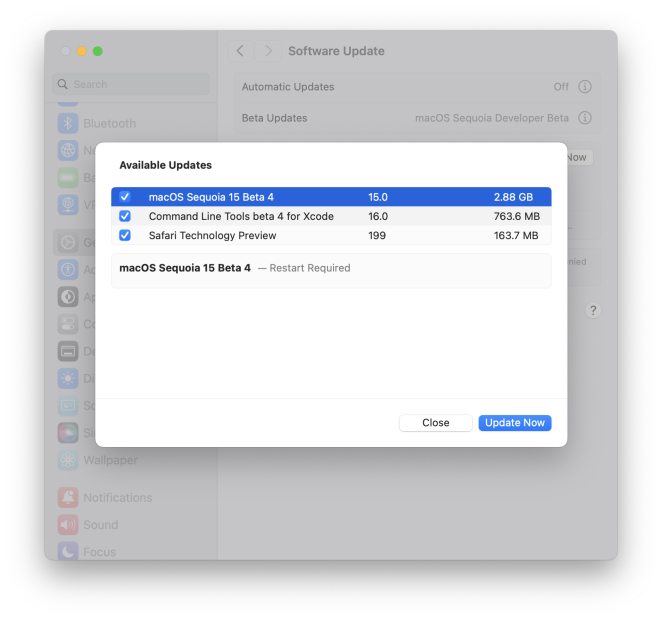 MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AM
MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AMApple has unveiled the fourth beta release of MacOS Sequoia 15 for those engaged in the macOS Sequoia developer beta testing program. Typically, the corresponding build for public beta testers, labeled as macOS Sequoia public beta 2, is released shor
 FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AM
FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AMApple's FaceTime application is designed to connect Apple users seamlessly, offering features such as dual-camera support on smartphones for enhanced video chat experiences.Occasionally, though, FaceTime might not function as intended. This article d


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Dreamweaver CS6
Visual web development tools

ZendStudio 13.5.1 Mac
Powerful PHP integrated development environment

SublimeText3 Linux new version
SublimeText3 Linux latest version

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft






