SQL Data Control Language (DCL): Securing Your Database with GRANT and REVOKE
Maintaining data security and integrity is critical in relational databases. SQL's Data Control Language (DCL) provides the tools to manage user access privileges, ensuring only authorized individuals can interact with database objects. The GRANT and REVOKE commands are central to this permission management system.

Key Concepts:
- SQL's DCL commands, primarily
GRANTandREVOKE, control database access. -
GRANTassigns specific privileges (SELECT, INSERT, UPDATE, DELETE, etc.) to users or roles. -
REVOKEremoves previously granted privileges, enhancing data security. - Role-based access control simplifies permission management by assigning predefined roles to users.
- Proper use of
GRANTandREVOKEensures controlled and secure database access.
Understanding DCL:
DCL, or Data Control Language, governs user access to database components: tables, views, stored procedures, and functions. It's distinct from Data Definition Language (DDL), which defines database structure, and Data Manipulation Language (DML), which handles data insertion, modification, and retrieval.
The GRANT Command: Assigning Privileges:
The GRANT command bestows database object access privileges. Its syntax allows granting specific permissions to users (or roles) on specified objects:
GRANT <privilege_type> ON <object_name> TO <user_name>;</user_name></object_name></privilege_type>
Privilege Types:
-
SELECT: Retrieve data. -
INSERT: Add new data. -
UPDATE: Modify existing data. -
DELETE: Remove data. -
ALTER: Modify object structure. -
REFERENCES: Reference another object. -
EXECUTE: Execute stored procedures or functions. (Further privileges exist depending on the database system.)
Example: Granting SELECT Access:
Consider a customers table. To grant sales_rep read access:
GRANT SELECT ON customers TO sales_rep;
The REVOKE Command: Removing Privileges:
REVOKE is the inverse of GRANT, used to withdraw previously granted permissions. The syntax mirrors GRANT:
REVOKE <privilege_type> ON <object_name> FROM <user_name>;</user_name></object_name></privilege_type>
Example: Revoking SELECT Access:
To remove sales_rep's access to the customers table:
REVOKE SELECT ON customers FROM sales_rep;
Important Considerations:
- Granularity: Permissions can be granted at various levels (entire tables or specific columns).
- Cascading Revocation: Revoking permissions from a user also removes them from users who inherited those permissions.
- Role-Based Access Control (RBAC): Groups simplify permission management by assigning predefined roles to users.
Managing User Permissions with Roles (Bookstore Example):
Let's manage permissions for a bookstore database with roles: Manager (full access), Sales Staff (read-only access to books and customers), and Inventory Staff (add and update books).
Database Setup (Example): (Table creation omitted for brevity; assume tables authors, books, customers, and orders exist.)
Creating Roles (PostgreSQL Example):
CREATE ROLE role_manager; CREATE ROLE role_sales_staff; CREATE ROLE role_inventory_staff;
(MySQL Example):
CREATE ROLE 'role_manager'; CREATE ROLE 'role_sales_staff'; CREATE ROLE 'role_inventory_staff';
Granting Privileges to Roles (PostgreSQL Example):
GRANT SELECT, INSERT, UPDATE, DELETE ON ALL TABLES IN SCHEMA public TO role_manager; GRANT SELECT ON books, customers TO role_sales_staff; GRANT INSERT, UPDATE ON books TO role_inventory_staff;
(MySQL Example): (Requires specifying the database name)
GRANT SELECT ON database_name.books TO 'role_sales_staff'; GRANT SELECT ON database_name.customers TO 'role_sales_staff'; GRANT INSERT, UPDATE ON database_name.books TO 'role_inventory_staff';
(Output images omitted for brevity)
Creating and Assigning Users to Roles (Similar syntax for PostgreSQL and MySQL, database name required for MySQL): (Example omitted for brevity)
Conclusion:
GRANT and REVOKE are essential for robust database security. Effective privilege management protects sensitive data and maintains database integrity. Understanding these commands is crucial for secure database administration.
Frequently Asked Questions (FAQ): (Omitted for brevity, as they are repetitive and already covered in the original text.)
The above is the detailed content of What are Grant and Revoke in SQL? - Analytics Vidhya. For more information, please follow other related articles on the PHP Chinese website!
 Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AM
Tesla's Robovan Was The Hidden Gem In 2024's Robotaxi TeaserApr 22, 2025 am 11:48 AMSince 2008, I've championed the shared-ride van—initially dubbed the "robotjitney," later the "vansit"—as the future of urban transportation. I foresee these vehicles as the 21st century's next-generation transit solution, surpas
 Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AM
Sam's Club Bets On AI To Eliminate Receipt Checks And Enhance RetailApr 22, 2025 am 11:29 AMRevolutionizing the Checkout Experience Sam's Club's innovative "Just Go" system builds on its existing AI-powered "Scan & Go" technology, allowing members to scan purchases via the Sam's Club app during their shopping trip.
 Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AM
Nvidia's AI Omniverse Expands At GTC 2025Apr 22, 2025 am 11:28 AMNvidia's Enhanced Predictability and New Product Lineup at GTC 2025 Nvidia, a key player in AI infrastructure, is focusing on increased predictability for its clients. This involves consistent product delivery, meeting performance expectations, and
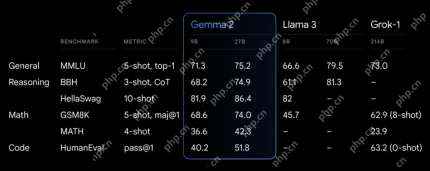 Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AM
Exploring the Capabilities of Google's Gemma 2 ModelsApr 22, 2025 am 11:26 AMGoogle's Gemma 2: A Powerful, Efficient Language Model Google's Gemma family of language models, celebrated for efficiency and performance, has expanded with the arrival of Gemma 2. This latest release comprises two models: a 27-billion parameter ver
 The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AM
The Next Wave of GenAI: Perspectives with Dr. Kirk Borne - Analytics VidhyaApr 22, 2025 am 11:21 AMThis Leading with Data episode features Dr. Kirk Borne, a leading data scientist, astrophysicist, and TEDx speaker. A renowned expert in big data, AI, and machine learning, Dr. Borne offers invaluable insights into the current state and future traje
 AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AM
AI For Runners And Athletes: We're Making Excellent ProgressApr 22, 2025 am 11:12 AMThere were some very insightful perspectives in this speech—background information about engineering that showed us why artificial intelligence is so good at supporting people’s physical exercise. I will outline a core idea from each contributor’s perspective to demonstrate three design aspects that are an important part of our exploration of the application of artificial intelligence in sports. Edge devices and raw personal data This idea about artificial intelligence actually contains two components—one related to where we place large language models and the other is related to the differences between our human language and the language that our vital signs “express” when measured in real time. Alexander Amini knows a lot about running and tennis, but he still
 Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AM
Jamie Engstrom On Technology, Talent And Transformation At CaterpillarApr 22, 2025 am 11:10 AMCaterpillar's Chief Information Officer and Senior Vice President of IT, Jamie Engstrom, leads a global team of over 2,200 IT professionals across 28 countries. With 26 years at Caterpillar, including four and a half years in her current role, Engst
 New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AM
New Google Photos Update Makes Any Photo Pop With Ultra HDR QualityApr 22, 2025 am 11:09 AMGoogle Photos' New Ultra HDR Tool: A Quick Guide Enhance your photos with Google Photos' new Ultra HDR tool, transforming standard images into vibrant, high-dynamic-range masterpieces. Ideal for social media, this tool boosts the impact of any photo,


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

DVWA
Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is very vulnerable. Its main goals are to be an aid for security professionals to test their skills and tools in a legal environment, to help web developers better understand the process of securing web applications, and to help teachers/students teach/learn in a classroom environment Web application security. The goal of DVWA is to practice some of the most common web vulnerabilities through a simple and straightforward interface, with varying degrees of difficulty. Please note that this software

PhpStorm Mac version
The latest (2018.2.1) professional PHP integrated development tool

SublimeText3 English version
Recommended: Win version, supports code prompts!

Atom editor mac version download
The most popular open source editor





