Email Security: A Comprehensive Guide to Protecting Your Inbox
Email remains a cornerstone of communication, despite the rise of newer technologies. However, its widespread use makes it a prime target for security threats. This guide explores the importance of email security and provides practical steps to safeguard your inbox.

Why Email Security Matters
Your email is more than just an inbox; it's the key to your online life. It's linked to nearly every online service, making it a critical vulnerability. Compromised email access can lead to password resets and account theft across various platforms, from social media to banking.
Recognizing the Threats
The primary email security threats stem from user actions, not inherent inbox vulnerabilities. These include:
- Malware: Malicious software disguised as email attachments that can damage your computer.
- Phishing: Attempts to steal personal information by impersonating legitimate entities (banks, companies) via deceptive emails and links.
- Spam: Unwanted promotional emails, easily managed with filters and unsubscribe options.
- Account Takeover: Unauthorized access to your email account, often due to weak or reused passwords.

Essential Security Practices
Protecting your email involves proactive measures:
- Avoid Suspicious Emails: Never open emails from unknown senders or download attachments/click links from untrusted sources.
- Verify Senders: Always confirm the sender's email address before interacting with the message.
- Protect Personal Information: Never share sensitive data (credit card numbers, social security numbers, etc.) via email.
- Use Email Filters: Configure filters to automatically delete or mark spam emails as read. (Example: In the Mail app, go to Preferences (⌘ ,), navigate to Rules, add a rule to identify spam patterns (email address or subject), and set actions to "Mark as Read" and "Delete Message".)

- Strong Passwords: Use unique, complex passwords (letters, numbers, special characters) and change them regularly. Consider a password manager like Secrets for generating and securely storing passwords.

- Two-Factor Authentication (2FA): Enable 2FA for enhanced security, requiring a code from your mobile device in addition to your password.
- Team Security (for organizations): Ensure all team members are aware of and follow established security protocols.
- Encrypted Email Services: For highly sensitive information, utilize a secure email server and encryption (like PGP) offered by private email services.
Managing Newsletters
Unsubscribe from unwanted newsletters easily with apps like Leave Me Alone. This app allows you to manage multiple email accounts, identify newsletters, and unsubscribe with a single click. It also offers features to roll up multiple newsletters for easier reading.

Encrypted Email Services Explained
Private email services offer two key security aspects: secure email servers and encryption. Encryption, like HTTPS, protects email content from unauthorized access. PGP is a common encryption technology using public and private keys. Email clients like Canary Mail simplify the process of using encryption.

Canary Mail offers a user-friendly interface with built-in privacy features, including automatic/manual encryption, a focused inbox, and tools for managing emails efficiently.
Conclusion
Robust email security is achievable with a combination of vigilance, best practices, and the use of helpful tools. By following these guidelines and utilizing apps like Secrets and Canary Mail, you can significantly enhance the protection of your email and online accounts. Consider exploring Setapp for a trial of these and other apps designed to optimize your digital workflow.
The above is the detailed content of Top Email Security Tips For Mac. For more information, please follow other related articles on the PHP Chinese website!
 How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AM
How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AMThe MacOS Sequoia public beta program is now available, providing Mac users with an early chance to explore the new major MacOS system software update. However, it's important to note that, like all beta versions, MacOS Sequoia public beta may be mor
 How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AM
How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AMInterested in running Ubuntu Linux on your Apple Silicon Mac? It's now simpler than ever to run Ubuntu alongside MacOS without the hassle of partitioning, dual booting, or risking your Mac's operating system. Thanks to virtual machine technology, you
 How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AM
How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AMThere are multiple methods to track CPU usage on a Mac, with the most popular being Activity Monitor for the graphical interface and htop or top for command line users. While Activity Monitor can display an optional core graph and htop shows CPU core
 chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AM
chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AMSome Mac users occasionally find that the "chronod" process in MacOS either consumes a lot of system resources or requests access to a network connection. Sometimes, chronods are also marked by overly alert antivirus applications. While many people will ignore this situation, there are also curious Mac users who actively explore what specific processes that consume a lot of resources are, or what the intentions are of a process that requires or requires Internet access. So, what is chronod on Mac? Why does it use high CPU and system resources? Why does it require network access? Let's dive into the chronod process to better understand its functionality. What is chronod? The chronod process is
 Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AM
Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AMWhat is Security Agent on MacSecurity Agent on Mac functions as a background process responsible for managing user authentication, system security notifications, and requests for application permissions. It collaborates with macOS's Security Server t
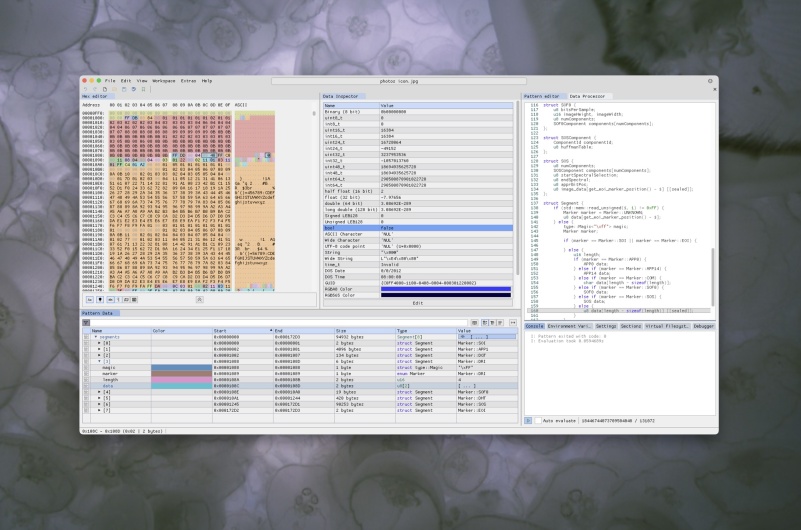 2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AM
2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AMHex editors are specialized software tools designed for viewing and editing hexadecimal data as well as raw binary data within files. These tools are indispensable for programmers, developers, and reverse engineers who need to inspect, debug, and ana
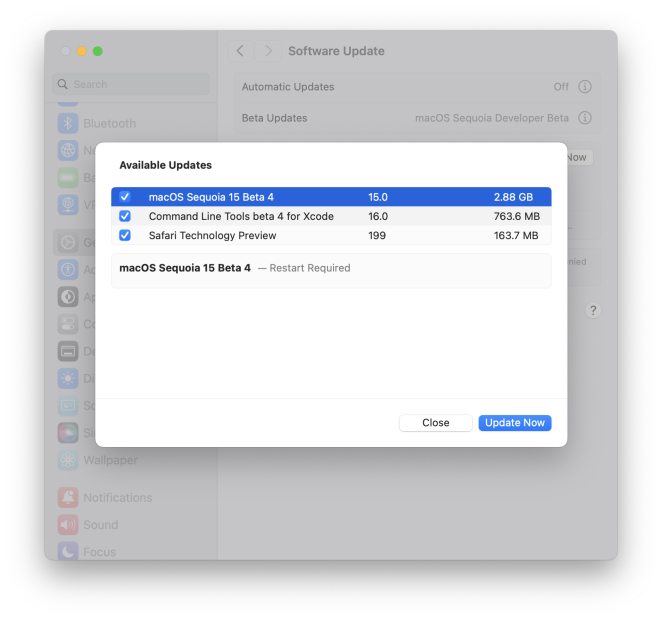 MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AM
MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AMApple has unveiled the fourth beta release of MacOS Sequoia 15 for those engaged in the macOS Sequoia developer beta testing program. Typically, the corresponding build for public beta testers, labeled as macOS Sequoia public beta 2, is released shor
 FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AM
FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AMApple's FaceTime application is designed to connect Apple users seamlessly, offering features such as dual-camera support on smartphones for enhanced video chat experiences.Occasionally, though, FaceTime might not function as intended. This article d


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Safe Exam Browser
Safe Exam Browser is a secure browser environment for taking online exams securely. This software turns any computer into a secure workstation. It controls access to any utility and prevents students from using unauthorized resources.

SublimeText3 English version
Recommended: Win version, supports code prompts!

MinGW - Minimalist GNU for Windows
This project is in the process of being migrated to osdn.net/projects/mingw, you can continue to follow us there. MinGW: A native Windows port of the GNU Compiler Collection (GCC), freely distributable import libraries and header files for building native Windows applications; includes extensions to the MSVC runtime to support C99 functionality. All MinGW software can run on 64-bit Windows platforms.

mPDF
mPDF is a PHP library that can generate PDF files from UTF-8 encoded HTML. The original author, Ian Back, wrote mPDF to output PDF files "on the fly" from his website and handle different languages. It is slower than original scripts like HTML2FPDF and produces larger files when using Unicode fonts, but supports CSS styles etc. and has a lot of enhancements. Supports almost all languages, including RTL (Arabic and Hebrew) and CJK (Chinese, Japanese and Korean). Supports nested block-level elements (such as P, DIV),

Dreamweaver CS6
Visual web development tools






