Email remains a primary online communication method, despite its inherent security vulnerabilities. Its free accessibility means nearly everyone possesses an email address, yet its design prioritizes text and attachments over inherent security. While encrypted email is gaining traction, not all providers offer robust protection.
Safeguarding Your Emails
This article explores email encryption, secure email transmission, and the security measures (or lack thereof) employed by popular email providers. We'll also introduce three top-tier apps designed to encrypt your emails.
Understanding Email Encryption
Email encryption prevents unauthorized access to your messages, though it doesn't stop interception. Public key cryptography scrambles the email content, making it readable only by the sender and recipient who possess the corresponding private key for decryption.
Email Encryption in Apple Mail
Apple Mail supports S/MIME, a common email encryption standard. To enable encryption:
- Access Keychain Access.
- Use Certificate Assistant > Request a Certificate From a Certificate Authority (CA). Provide your email address, name, and the CA's email address (e.g., VeriSign).
- Customize key pair information (optional).
- Review and confirm.

After CA approval, export your certificate, adding a strong passphrase for enhanced security and cross-device compatibility. Restart Mail; your emails will be automatically signed using the public key (checkmark icon). Encryption (lock icon) is enabled when the recipient also possesses a certificate. Expired certificates require renewal by repeating the process. Never delete old keys unless you intend to lose access to older messages.
Gmail Encryption
Gmail employs TLS (Transport Layer Security) for incoming and outgoing emails, but its effectiveness depends on both sender and receiver using TLS. Google Workspace users have access to S/MIME for enhanced protection. However, both TLS and S/MIME are only effective if both parties have them enabled, and neither prevents Google from scanning email content.
Gmail Attachment and Confidential Mode Encryption
TLS covers all Gmail content, including attachments, but requires both parties to use TLS. Gmail's "Confidential Mode" offers limited control (expiration dates, access revocation, passcode requirements), but isn't true encryption. It also necessitates sharing the recipient's phone number with Google.

Apps for Email Encryption
Canary Mail offers default email encryption (SecureSend and PGP). Enable it in Settings > Security. You can also manually manage encryption keys.


Canary Mail simplifies encryption management, eliminating the need for manual key creation. Its Setapp integration provides iOS compatibility and access to Copilot, an AI assistant for email management.
Data Requiring Email Encryption
Given email's vulnerability, encrypting sensitive information is crucial:
- Bank details
- Addresses
- Signatures
- Travel plans
- Personal information about others
Additional Security Measures
Beyond email encryption, consider using tools like CleanMyMac X's Shredder to permanently delete files and its Privacy tab to clear browsing history and other data traces.


Secrets is recommended for password management and secure storage of sensitive data.

Conclusion
Email encryption is vital for protecting sensitive data. Canary Mail, CleanMyMac X, and Secrets offer a comprehensive approach to email security, data deletion, and password management. A seven-day Setapp trial provides access to these and other productivity apps. After the trial, Setapp costs $9.99/month or $8.99/month with annual prepayment.
The above is the detailed content of How to encrypt email Gmail and Mail. For more information, please follow other related articles on the PHP Chinese website!
 How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AM
How to Install MacOS Sequoia Public BetaMay 15, 2025 am 10:39 AMThe MacOS Sequoia public beta program is now available, providing Mac users with an early chance to explore the new major MacOS system software update. However, it's important to note that, like all beta versions, MacOS Sequoia public beta may be mor
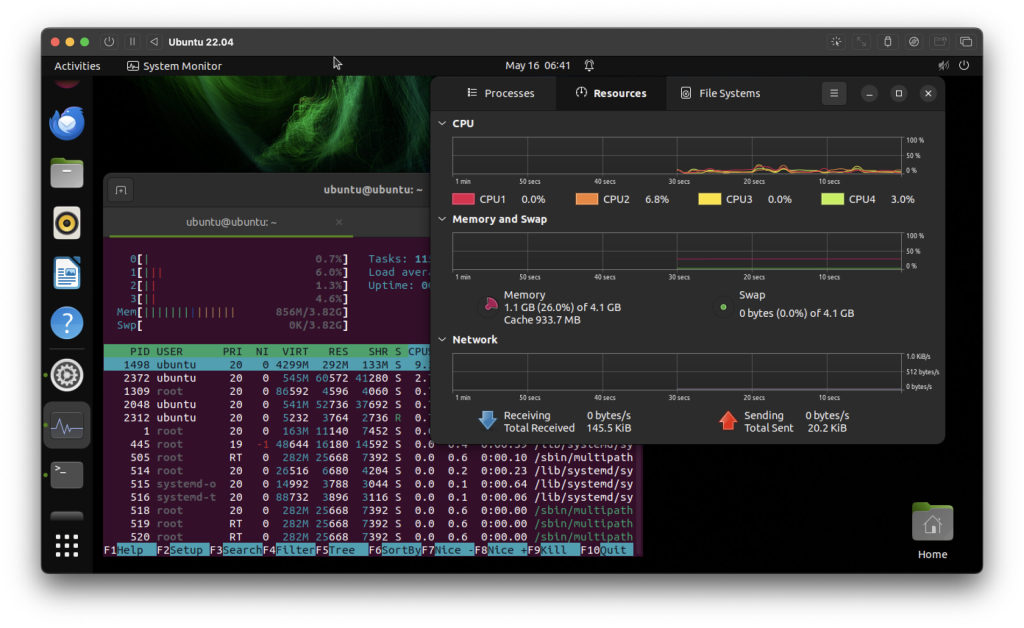 How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AM
How to Run Ubuntu Linux on Apple Silicon MacMay 15, 2025 am 10:37 AMInterested in running Ubuntu Linux on your Apple Silicon Mac? It's now simpler than ever to run Ubuntu alongside MacOS without the hassle of partitioning, dual booting, or risking your Mac's operating system. Thanks to virtual machine technology, you
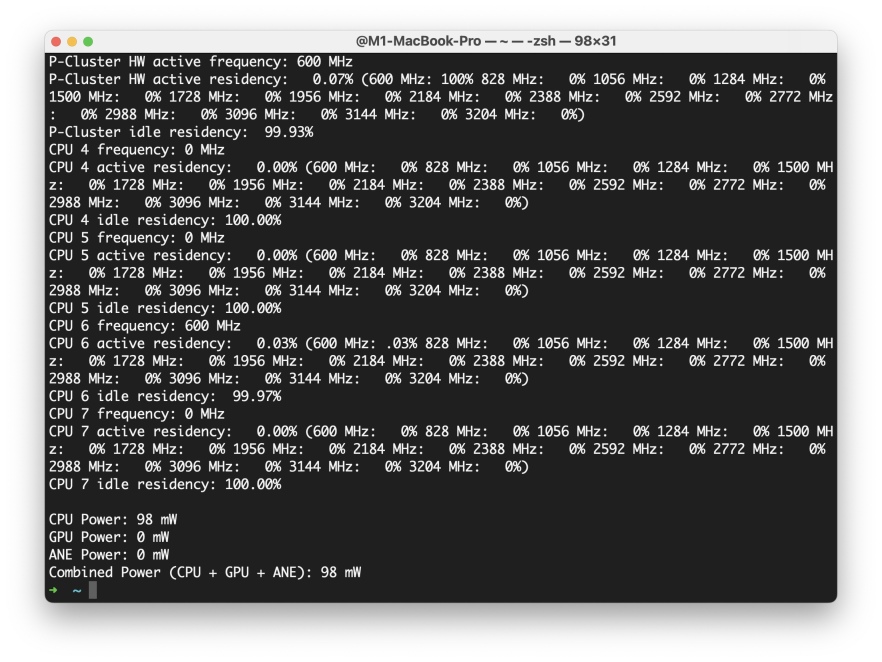 How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AM
How to See Individual Core CPU Usage on Mac with powermetricsMay 15, 2025 am 10:31 AMThere are multiple methods to track CPU usage on a Mac, with the most popular being Activity Monitor for the graphical interface and htop or top for command line users. While Activity Monitor can display an optional core graph and htop shows CPU core
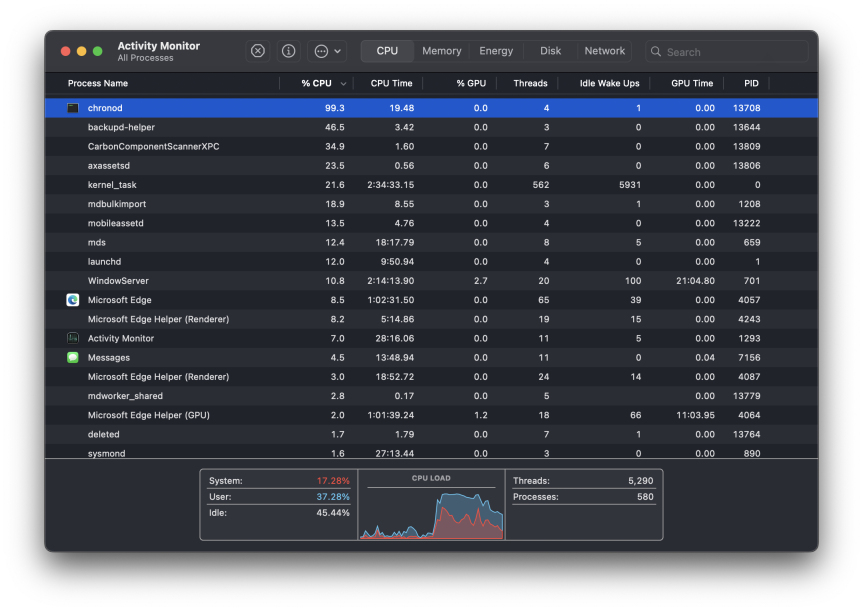 chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AM
chronod on Mac – High CPU Use & Network Access Requests ExplainedMay 15, 2025 am 10:18 AMSome Mac users occasionally find that the "chronod" process in MacOS either consumes a lot of system resources or requests access to a network connection. Sometimes, chronods are also marked by overly alert antivirus applications. While many people will ignore this situation, there are also curious Mac users who actively explore what specific processes that consume a lot of resources are, or what the intentions are of a process that requires or requires Internet access. So, what is chronod on Mac? Why does it use high CPU and system resources? Why does it require network access? Let's dive into the chronod process to better understand its functionality. What is chronod? The chronod process is
 Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AM
Security Agent on Mac: What Is It & What Does It Do on MacBook Air/Pro?May 15, 2025 am 10:11 AMWhat is Security Agent on MacSecurity Agent on Mac functions as a background process responsible for managing user authentication, system security notifications, and requests for application permissions. It collaborates with macOS's Security Server t
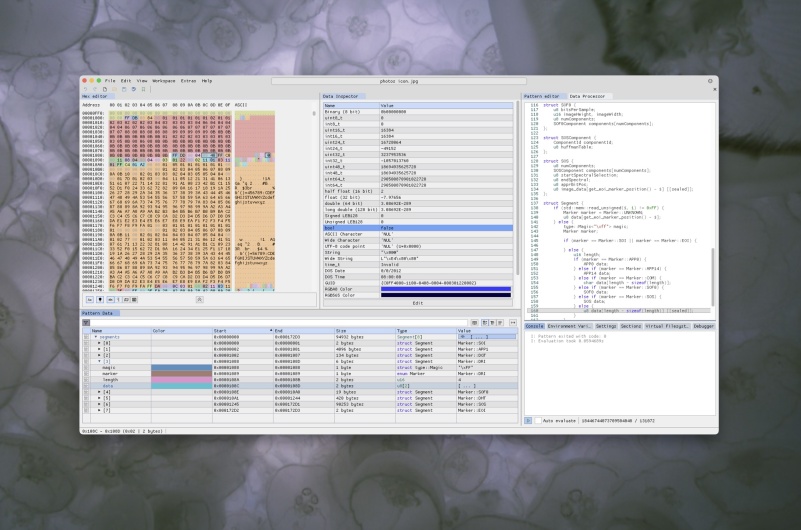 2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AM
2 of the Best Hex Editors for Mac: ImHex & Hex FiendMay 15, 2025 am 10:05 AMHex editors are specialized software tools designed for viewing and editing hexadecimal data as well as raw binary data within files. These tools are indispensable for programmers, developers, and reverse engineers who need to inspect, debug, and ana
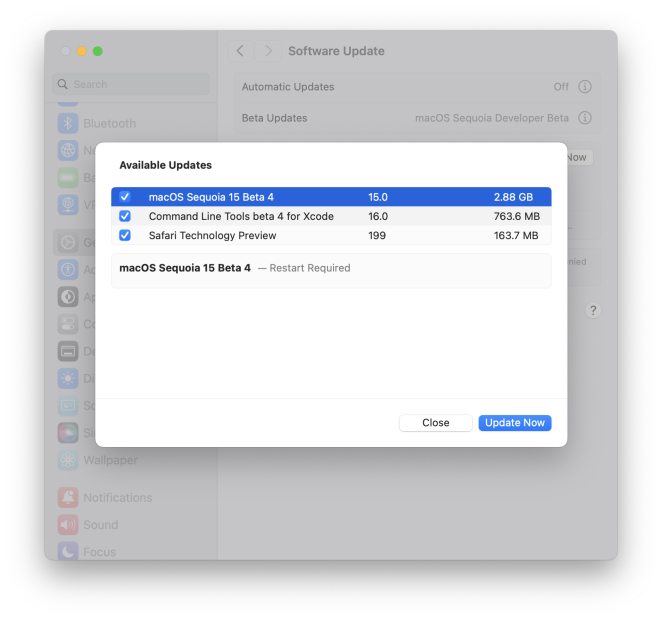 MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AM
MacOS Sequoia 15 Beta 4 Available to DownloadMay 15, 2025 am 09:54 AMApple has unveiled the fourth beta release of MacOS Sequoia 15 for those engaged in the macOS Sequoia developer beta testing program. Typically, the corresponding build for public beta testers, labeled as macOS Sequoia public beta 2, is released shor
 FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AM
FaceTime Not Working on Mac? Here's How to Fix ItMay 15, 2025 am 09:49 AMApple's FaceTime application is designed to connect Apple users seamlessly, offering features such as dual-camera support on smartphones for enhanced video chat experiences.Occasionally, though, FaceTime might not function as intended. This article d


Hot AI Tools

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Undress AI Tool
Undress images for free

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

SecLists
SecLists is the ultimate security tester's companion. It is a collection of various types of lists that are frequently used during security assessments, all in one place. SecLists helps make security testing more efficient and productive by conveniently providing all the lists a security tester might need. List types include usernames, passwords, URLs, fuzzing payloads, sensitive data patterns, web shells, and more. The tester can simply pull this repository onto a new test machine and he will have access to every type of list he needs.

SublimeText3 English version
Recommended: Win version, supports code prompts!

SublimeText3 Linux new version
SublimeText3 Linux latest version

VSCode Windows 64-bit Download
A free and powerful IDE editor launched by Microsoft

SublimeText3 Mac version
God-level code editing software (SublimeText3)






